PARAGRAPH PAGE
A.1 GENERAL. 50A.1.1 Scope. 50A.1.2 Applicability. 50A.2 APPLICABLE DOCUMENTS. 50A.2.1 General. 50A.2.2 Government documents. 50A.2.2.1 Specifications, standards, and handbooks. 50A.2.3 Non-Government publications. 51A.3 DEFINITIONS. 52A.3.1 Terms. 52A.3.2 Abbreviations and acronyms. 52A.3.3 Definitions of timing symbols. 54A.4 GENERAL REQUIREMENTS. 55A.4.1 ALE introduction. 55A.4.1.1 ALE addresses. 55A.4.1.2 Scanning. 55A.4.1.3 Calling. 56A.4.1.4 Channel evaluation. 56A.4.1.5 Channel quality display. 57A.4.2 System performance requirements. 57A.4.2.1 Scanning rate. 57A.4.2.1.1 Alternative Quick Call (AQC). 57A.4.2.1.2 Recommendation. 57A.4.2.2 Occupancy detection - not tested (NT). 57A.4.2.3 Linking probability. 58A.4.2.3.1 AQC-ALE linking probability. 60A.4.2.3.2 AQC-ALE linking performance. 60A.4.3 Required data structures. 60A.4.3.1 Channel memory. 60A.4.3.2 Self address memory. 61A.4.3.3 Other station table. 63A.4.3.3.1 Other station address storage. 63A.4.3.3.2 Link quality memory. 65A.4.3.3.3 Other station settings storage. 65A.4.3.4 Operating parameters. 65A.4.3.5 Message memory. 65A.4.4 ALE operational rules. 66A.4.5 Alternate Quick Call ALE (AQC-ALE) (NT). 66A.4.5.1 Introduction. 66A.4.5.2 General signaling strategies. 66TABLE OF CONTENTS(continued)PARAGRAPH PAGEA.4.5.3 Features supported by AQC-ALE. 67A.4.5.4 Features not provided by AQC-ALE. 68A.5. DETAILED REQUIREMENTS. 68A.5.1 ALE modem waveform. 68A.5.1.1 Introduction. 68A.5.1.2 Tones. 68A.5.1.3 Timing. 69A.5.1.4 Accuracy. 69A.5.2 Signal structure. 71A.5.2.1 Introduction. 71A.5.2.2 FEC. 71A.5.2.2.1 General. 71A.5.2.2.2 Golay coding. 71A.5.2.2.2.1 Encoding. 71A.5.2.2.2.2 Decoding. 71A.5.2.2.3 Interleaving and deinterleaving. 76A.5.2.2.4 Redundant words. 76A.5.2.3 Word structures. 76A.5.2.3.1 ALE word format. 76A.5.2.3.1.1 Structure. 81A.5.2.3.1.2 Word types. 81A.5.2.3.1.3 Preambles. 81A.5.2.3.2 Address words. 82A.5.2.3.2.1 TO. 82A.5.2.3.2.2 THIS IS (TIS). 82A.5.2.3.2.3 THIS WAS (TWAS). 82A.5.2.3.2.4 THRU. 82A.5.2.3.2.5 FROM. 83A.5.2.3.3 Message words. 83A.5.2.3.3.1 CMD. 83A.5.2.3.4 Extension words. 84A.5.2.3.4.1 DATA. 84A.5.2.3.4.2 REP. 84A.5.2.4 Addressing. 84A.5.2.4.1 Introduction. 84A.5.2.4.2 Basic 38 subset. 85A.5.2.4.3 Stuffing. 86A.5.2.4.4 Individual addresses. 86A.5.2.4.4.1 Basic size. 88A.5.2.4.4.2 Extended size. 88TABLE OF CONTENTS(continued)PARAGRAPH PAGEA.5.2.4.5 Net addresses. 90A.5.2.4.6 Group addresses. 90A.5.2.4.7 Allcall addresses. 90A.5.2.4.8 AnyCalls. 91A.5.2.4.9 Wildcards. 91A.5.2.4.10 Self addresses. 92A.5.2.4.11 Null address. 93A.5.2.4.12 In-link address. 93A.5.2.5 Frame structure. 93A.5.2.5.1 Calling cycle. 95A.5.2.5.2 Message section. 98A.5.2.5.3 Conclusion. 100A.5.2.5.4 Valid sequences. 103A.5.2.5.5 Basic frame structure examples. 103A.5.2.6 Synchronization. 107A.5.2.6.1 Transmit word phase. 107A.5.2.6.2 Receiver word sync. 108A.5.2.6.3 Synchronization criteria. 108A.5.3 Sounding. 109A.5.3.1 Introduction. 109A.5.3.2 Single channel. 110A.5.3.3 Multiple channels. 110A.5.3.4 Optional handshake. 115A.5.4 Channel selection. 117A.5.4.1 LQA. 117A.5.4.1.1 BER. 117A.5.4.1.2 SINAD. 118A.5.4.1.3 MP (optional). 118A.5.4.1.4 Operator display (optional). 118A.5.4.2 Current channel quality report (LQA CMD). 118A.5.4.2.1 BER field in LQA CMD. 118A.5.4.2.2 SINAD. 118A.5.4.2.3 MP. 118A.5.4.3 Historical LQA report. 120A.5.4.4 Local noise report CMD (optional). 120A.5.4.5 Single-station channel selection. 121A.5.4.5.1 Single-station channel selection for link establishment. 121A.5.4.5.2 Single-station channel selection for one-way broadcast. 123A.5.4.5.3 Single-station channel selection for listening. 123A.5.4.6 Multiple-station channel selection. 123TABLE OF CONTENTS(continued)PARAGRAPH PAGEA.5.4.7 Listen before transmit. 124A.5.4.7.1 Listen-before-transmit duration. 124A.5.4.7.2 Modulations to be detected. 124A.5.4.7.3 Listen before transmit override. 124A.5.5 Link establishment protocols. 124A.5.5.1 Manual operation. 124A.5.5.2 ALE. 125A.5.5.2.1 Timing. 125A.5.5.2.2 ALE states. 125A.5.5.2.3 ALE channel selection. 125A.5.5.2.3.1 Rejected channel. 126A.5.5.2.3.2 Busy channel. 126A.5.5.2.3.3 Exhausted channel list. 126A.5.5.2.4 End of frame detection. 126A.5.5.3 One-to-one calling. 129A.5.5.3.1 Sending an individual call. 129A.5.5.3.2 Receiving an individual call. 130A.5.5.3.3 Response. 131A.5.5.3.4 Acknowledgment. 132A.5.5.3.5 Link termination. 133A.5.5.3.5.1 Manual termination. 133A.5.5.3.5.2 Automatic termination. 133A.5.5.3.6 Collision detection. 134A.5.5.4 One-to-many calling. 134A.5.5.4.1 Slotted responses. 134A.5.5.4.1.1 Slotted response frames. 135A.5.5.4.1.2 Slot widths. 135A.5.5.4.1.3 Slot wait time formula. 135A.5.5.4.1.4 Slotted response example. 136A.5.5.4.2 Star net calling protocol. 136A.5.5.4.2.1 Star net call. 136A.5.5.4.2.2 Star net response. 137A.5.5.4.2.3 Star net acknowledgment. 137A.5.5.4.3 Star group calling protocol. 137A.5.5.4.3.1 Star group scanning call. 137A.5.5.4.3.2 Star group leading call. 138A.5.5.4.3.3 Star group call conclusion. 138A.5.5.4.3.4 Receiving a star group call. 138A.5.5.4.3.5 Star group slotted responses. 139A.5.5.4.3.6 Star group acknowledgment. 139TABLE OF CONTENTS(continued)PARAGRAPH PAGEA.5.5.4.3.7 Star group call example. 139A.5.5.4.3.8 Multiple self addresses in group call. 139A.5.5.4.4 Allcall protocol. 140A.5.5.4.5 AnyCall protocol. 141A.5.5.4.6 Wildcard calling protocol. 142A.5.6. ALE control functions (CMDs other than AMD, DTM, and DBM). 142A.5.6.1 CRC. 144A.5.6.2 Power control (optional). 146A.5.6.3 Channel related functions. 147A.5.6.3.1 Channel designation. 147A.5.6.3.2 Frequency designation. 148A.5.6.3.3 Full-duplex independent link establishment (optional). 149A.5.6.3.4 LQA polling (optional). 149A.5.6.3.5 LQA reporting (optional). 149A.5.6.3.6 LQA scan with linking (optional). 149A.5.6.3.7 Advanced LQA (optional). 149A.5.6.4 Time-related functions. 149A.5.6.4.1 Tune and wait. 149A.5.6.4.2 Scheduling commands. 150A.5.6.4.3 Time exchange word formats. 154A.5.6.4.3.1 Command words. 154A.5.6.4.3.2 Time Is command. 154A.5.6.4.3.3 Time Request command. 154A.5.6.4.3.4 Other encodings. 154A.5.6.4.4 Coarse time word. 154A.5.6.4.5 Authentication word. 155A.5.6.4.6 Time quality. 155A.5.6.5 Mode control functions (optional). 157A.5.6.5.1 Modem negotiation and handoff. 158A.5.6.5.1.1 Modem selection CMD. 158A.5.6.5.1.2 Modem negotiating. 158A.5.6.5.2 Crypto negotiation and handoff. 159A.5.6.6 Capabilities reporting functions. 160A.5.6.6.1 Version CMD (mandatory). 160A.5.6.6.2 Capabilities function. (mandatory). 161A.5.6.6.2.1 Capabilities query. 161A.5.6.6.2.2 Capabilities report CMD. 162A.5.6.6.2.3 Data format. 162A.5.6.7 Do not respond CMD. 165A.5.6.8 Position report (optional). 165TABLE OF CONTENTS(continued)PARAGRAPH PAGEA.5.6.9 User unique functions (UUFs). 165A.5.7 ALE message protocols. 167A.5.7.1 Overview. 167A.5.7.2 AMD mode (mandatory). 167A.5.7.2.1 Expanded 64-channel subset. 167A.5.7.2.2 AMD protocol. 168A.5.7.2.3 Maximum AMD message size. 169A.5.7.3 DTM mode. 169A.5.7.4 DBM mode. 181A.5.8 AQC (optional) (NT). 194A.5.8.1 Signaling structure (NT). 194A.5.8.1.1 AQC-ALE word structure (NT). 194A.5.8.1.1.1 Packed address (NT). 194A.5.8.1.1.2 Address differentiation flag (NT). 196A.5.8.1.2 Preambles (NT). 196A.5.8.1.2.1 TO (NT). 196A.5.8.1.2.2 THIS IS (TIS) (NT). 196A.5.8.1.2.3 THIS WAS (TWAS) (NT). 196A.5.8.1.2.4 PART2 (NT). 196A.5.8.1.2.5 INLINK (NT). 197A.5.8.1.2.6 COMMAND (NT). 197A.5.8.1.2.7 DATA (NT). 197A.5.8.1.2.8 REPEAT (NT). 197A.5.8.1.3 AQC-ALE address characteristics (NT). 197A.5.8.1.3.1 Address size (NT). 197A.5.8.1.3.2 Address character set (NT). 197A.5.8.1.3.3 Support of ISDN (option) (NT). 197A.5.8.1.3.4 Over-the-air address format (NT). 197A.5.8.1.4 Address formats by call type (NT). 197A.5.8.1.4.1 Unit addresses (NT). 197A.5.8.1.4.2 StarNet addresses (NT). 198A.5.8.1.4.3 Group addresses (NT). 198A.5.8.1.4.4 AllCall address (NT). 198A.5.8.1.4.5 AnyCall address (NT). 198A.5.8.1.5 Data exchange field (NT). 198A.5.8.1.5.1 DE(1) no data available (NT). 199A.5.8.1.5.2 DE(2) number of to's left in calling cycle (NT). 199A.5.8.1.5.3 DE(3) Inlink resource list (NT). 199A.5.8.1.5.4 DE(4) local noise report (NT). 200A.5.8.1.5.5 DE(5) LQA variation (NT). 201TABLE OF CONTENTS(continued)PARAGRAPH PAGEA.5.8.1.5.6 DE(6) LQA measurement (NT). 202A.5.8.1.5.7 DE(7) number of Tis/Twas left in sounding cycle (NT). 203A.5.8.1.5.8 DE(8) inlink data definition from INLINK (NT). 203A.5.8.1.5.9 DE(9) Inlink data definition from PART2 (NT). 204A.5.8.1.6 PSK tone sequence (optional) (NT). 205A.5.8.1.6.1 PSK tone sequence placement (NT). 205A.5.8.1.6.2 PSK tone sequence generation (NT). 205A.5.8.2 AQC-ALE frame structure and protocols (NT). 205A.5.8.2.1 Calling cycle (NT). 205A.5.8.2.2 Unit call structure (NT). 207A.5.8.2.3 Star net call structure (NT). 207A.5.8.2.4 AllCall frame formats (NT). 208A.5.8.2.5 AnyCall frame formats (NT). 209A.5.8.2.6 Sounding (NT). 210A.5.8.2.7 Inlink transactions (NT). 210A.5.8.2.7.1 Inlink transaction as an acknowledgement (NT). 211A.5.8.2.7.2 CRC for Inlink event sequences (NT). 211A.5.8.2.7.3 Use of address section (NT). 212A.5.8.2.7.4 Slotted responses in an Inlink state (NT). 212A.5.8.3 AQC-ALE orderwire functions (optional) (NT). 212A.5.8.3.1 Operator ACK/NAK transaction command section (optional) (NT). 212A.5.8.3.2 AQC-ALE control message section (optional) (NT). 213A.5.8.3.2.1 AMD dictionary message (NT). 214A.5.8.3.2.2 Channel definition (NT). 217A.5.8.3.2.3 Slot assignment (NT). 218A.5.8.3.2.4 List content of database (NT). 218A.5.8.3.2.5 List database activation time (NT). 218A.5.8.3.2.6 Set database activation time (NT). 218A.5.8.3.2.7 Define database content (NT). 219A.5.8.3.2.8 Database content listing (NT) 220A.5.8.4 AQC-ALE linking protection (NT). 220
TABLE A-I. Occupancy detection probability (2G and 3G). 57TABLE A-II. Probability of linking. 59TABLE A-III. Channel memory example. 62TABLE A-IV. Self address memory example. 63TABLE A-V. ALE operational rules. 66TABLE A-VI. 2/3 majority vote decoding. 79TABLE A-VII. Majority word construction. 79TABLE OF CONTENTS(continued)PARAGRAPH PAGETABLE A-VIII. ALE word types (preambles). 81TABLE A-IX. Use of "@" utility symbol. 87TABLE A-X. Basic (38) address structures. 89TABLE A-XI. Use of "?" wildcard symbol. 92TABLE A-XII. Limits to frames. 103TABLE A-XIII. Basic BER values. 119TABLE A-XIV. Link quality analysis structure. 120TABLE A-XV. Timing. 127TABLE A-XVI. Summary of CMD functions. 143TABLE A-XVII. Cyclic redundancy check structure. 146TABLE A-XVIII. Power control CMD bits (KP1-3). 147TABLE A-XIX. Tune and wait structure. 151TABLE A-XX. Time values. 152TABLE A-XXI. Time-related CMD functions. 153TABLE A-XXII. Time quality. 156TABLE A-XXIII. Modem codes. 159TABLE A-XXIV. Crypto codes. 160TABLE A-XXV. Component selection. 161TABLE A-XXVI. Format selection. 161TABLE A-XXVII. Capabilities report data fields (ALE timing). 163TABLE A-XXVIII. Capabilities report data fields (mode settings). 163TABLE A-XXIX. Capabilities report data field (feature capabilities). 164TABLE A-XXX. User unique functions structure. 166TABLE A-XXXI. ALE message protocols. 167TABLE A-XXXII. DTM characteristics. 171TABLE A-XXXIII. DTM structure. 174TABLE A-XXXIV. DBM characteristics. 182TABLE A-XXXV. DBM structures. 188TABLE A-XXXVI. AQC address character ordinal value. 195TABLE A-XXXVII. AQC-ALE word types (and preambles). 196TABLE A-XXXVIII. Data exchange definitions. 198TABLE A-XXXIX. Inlink resource list. 200TABLE A-XL. Local noise report. 201TABLE A-XLI. Magnitude of minimum SNR from mean SNR. 202TABLE A-XLII. LQA scores. 203TABLE A-XLIII. Valid combinations of ACK-This and I'm Inlink. 204TABLE A-XLIV. DE(9) inlink transaction identifier. 205TABLE A-XLV. Scanning part duration using automated calculation. 206TABLE A-XLVI. Operator ACK/NAK command. 213TABLE A-XLVII. AQC-ALE control message section word sequences. 213TABLE OF CONTENTS(continued)PARAGRAPH PAGETABLE A-XLVIII. Lookup tables for packed AMD messages. 216TABLE A-IL. Adding spaces during AMD unpacking. 216
FIGURE A-1. Data link with ALE and FEC sublayers. 56FIGURE A-2. Occupancy detection test setup. 58FIGURE A-3. System performance measurements test setup. 58FIGURE A-4. Connectivity and LQA memory example. 64FIGURE A-5. ALE symbol library. 70FIGURE A-6. Generator matrix for (24, 12) extended Golay code. 72FIGURE A-7. Parity-check matrix for (24, 12) extended Golay code. 73FIGURE A-8. Golay word encoding example. 74FIGURE A-9. Golay FEC coding examples. 75FIGURE A-10. Word bit coding and interleaving. 77FIGURE A-11. Bit and word decoding. 78FIGURE A-12. ALE basic word structure. 80FIGURE A-13. Basic 38 subset (unshaded areas). 85FIGURE A-14. Valid word sequences. 94FIGURE A-15. Calling cycle sequence. 96FIGURE A-16. Message sequence. 99FIGURE A-17. Conclusion (terminator) sequences. 101FIGURE A-18. Valid word sequence (calling cycle section). 104FIGURE A-19. Valid word sequence (message section). 105FIGURE A-20. Valid word sequence (conclusion section). 106FIGURE A-21. Basic frame structure examples. 107FIGURE A-22. Basic sounding structure. 111FIGURE A-23. Call rejection scanning sounding protocol. 112FIGURE A-24. Call acceptance scanning sounding protocol. 113FIGURE A-25. Scanning sounding with optional handshake protocol. 116FIGURE A-26. Local noise report (optional). 121FIGURE A-27. LQA memory example. 122FIGURE A-28. Link establishment states. 125FIGURE A-29. Individual calls. 129FIGURE A-30. Response frame. 131FIGURE A-31. Acknowledgment frame. 132FIGURE A-32. Slotted responses. 135FIGURE A-33. 2G ALE slotted responses. 136FIGURE A-34. Net call. 136FIGURE A-35. Group call. 137FIGURE A-36. Power control CMD format. 147TABLE OF CONTENTS(continued)PARAGRAPH PAGEFIGURE A-37. Frequency select CMD format. 148FIGURE A-38. Time exchange CMD word. 155FIGURE A-39. Coarse time and authentication words. 156FIGURE A-40. Mode control CMD format. 157FIGURE A-41. Modem selection CMD format. 158FIGURE A-42. Crypto selection CMD format. 160FIGURE A-43. Version CMD format. 160FIGURE A-44. Capabilities query CMD format. 162FIGURE A-45. Capabilities report CMD and DATA format. 162FIGURE A-46. Expanded 64 ASCII subset (shown unshaded). 168FIGURE A-47. DTM structure example. 172FIGURE A-48. Data test message reconstruction (overlay). 177FIGURE A-49. Data test message structure and ARQ example. 184FIGURE A-50. DBM interleaver and deinterleaver. 185FIGURE A-51. DBM example. 186FIGURE A-52. AQC-ALE data exchange word. 195FIGURE A-53. Example of unit call format. 207FIGURE A-54. Example of StarNet format. 208FIGURE A-55. Example AllCall frame format. 209FIGURE A-56. Example AnyCall frame formats. 209FIGURE A-57. Example sounding frame format. 210FIGURE A-58. Example inlink transaction TRW sequences. 211FIGURE A-59. Generalized AQC-ALE control message format. 214FIGURE A-60. AQC-ALE dictionary lookup message. 215FIGURE A-61. Channel definition and meet-me function. 217FIGURE A-62. AQC-ALE slot assignment. 218FIGURE A-63. List content of database. 218FIGURE A-64. Set database activation time. 219FIGURE A-65. Define database content. 219
ANNEX A. DEFINITIONS OF TIMING SYMBOLS 221ANNEX B. TIMING 224ANNEX C. SUMMARY OF ALE SIGNAL PARAMETERS 234
This appendix provides details of the prescribed waveform, signal
structures, protocols, and performance requirements for the second
generation (2G) automatic link establishment (ALE) system.
This appendix is a mandatory part of MIL-STD-188-141 whenever
ALE is a requirement to be implemented into the high frequency
(HF) radio system. The functional capability described herein
includes automatic signaling, selective calling, automatic answering,
and radio frequency (rf) scanning with link quality analysis (LQA).
The capability for manual operation of the radio in order to
conduct communications with existing, older generation, non-automated
manual radios, shall not be impaired by implementation of these
automated features.
The documents listed in this section are specified in A.3, A.4,
and A.5 of this standard. This section does not include documents
cited in other sections of this standard or recommended for additional
information or as examples. While every effort has been made
to ensure the completeness of this list, document users are cautioned
that they must meet all specified requirements documents cited
in A.3, A.4, and A.5 of this standard, whether or not they are
listed.
The following specifications, standards, and handbooks form a
part of this document to the extent specified herein. Unless
otherwise specified, the issues of these documents are those listed
in the issue of the Department of Defense Index of Specifications
and Standards (DODISS) and supplement thereto, cited in the solicitation.
| STANDARDS | ||||
| FEDERAL | ||||
| Federal Information Processing Standards | ||||
| FIPS PUB 1-1 | Publication Code: for Information Interchange | |||
| FEDERAL STANDARDS | ||||
| FED-STD-1003 | Telecommunications: Synchronous Bit Orientation Data Link Control Procedures (Advanced Data Communications Control Procedures) | |||
| FED-STD-1037 | Telecommunications: Glossary of Telecommunications Terms | |||
| DEPARTMENT OF DEFENSE | ||||
| MIL-STD-188-110 | Interoperability and Performance Standards for HF Data Modems | |||
(Copies of Federal Information Processing Standards (FIPS) are
available at Standardization Document Order Desk, 700 Robbins
Avenue, Building #4, Section D, Philadelphia, PA 19111-5094.
Non-Department of Defense (DoD) users must request copies of
FIPS from the National Technical Information Service, 5285 Port
Royal Road, Springfield, VA 22161-2171.)
The following documents form a part of this appendix to the extent
specified:
| INTERNATIONAL STANDARDIZATION DOCUMENTS | |||
| North Atlantic Treaty Organization (NATO) Standardization Agreements (STANAGs) | |||
| STANAG 4285 | Characteristics of 1200/2400/3600 bps Single Tone Modems for HF Radio Links | ||
| STANAG 4529 | Characteristics of Single Tone Modulators/Demodulators for Maritime HF Radio Links with 1240 Hz Bandwidth | ||
| International Telecommunications Union (ITU),
Radio Regulations | |||
| ITU-R F.520-2 | Recommendation for Fixed Service, use of High Frequency Ionospheric Channel Simulators | ||
(Application for copies should be addressed to the General Secretariat,
International Organization for Standardization (ISO) 1, Rue de
Varembe, CH-1211 Geneva 20, Switzerland.)
| Other Publications | |||
| NMSU-EE-CD-001 | Wireless Network Waveform Samples | ||
(Application for copies should be addressed to New Mexico State
University, Klipsch School of Electrical and Computer Engineering,
University Park, NM 88003, Attn: Dr. E. E. Johnson.)
(Non-Government standards and other publications are normally
available from the organizations that prepare or distribute the
documents. These documents also may be available in or through
libraries or other informational services.)
Definitions of terms used in this document shall be as specified
in the current edition of
FED-STD-1037 except where inconsistent with the use in this standard.
In addition, the following definitions are applicable for the
purpose of this standard.
The abbreviations and acronyms used in this document are defined
below. Those listed in the current edition of FED-STD-1037 have
been included for the convenience of the reader.
| 2G ALE | second generation automatic link establishment | |
| 3G ALE | second generation automatic link establishment |
| ACK | acknowledge character | ||
| AQC | Alternative Quick Call | ||
| AQC-ALE | Alternative Quick Call Automatic Link Establishment | ||
| AGC | automatic gain control | ||
| ALE | automatic link establishment | ||
| AMD | automatic message display | ||
| ARQ | automatic repeat request | ||
| ASCII | American Standard Code for Information Interchange | ||
| AWGN | Additive white gaussian noise | ||
| b/s | bits per second | ||
| BCD | binary coded decimal | ||
| BER | bit error ratio | ||
| chps | channels per second | ||
| CCIR | International Radio Consultative Committee | ||
| CMD | ALE preamble word COMMAND | ||
| CRC | cyclic redundancy check | ||
| dB | Decibel | ||
| dBw | dB referred to 1 W (watt) | ||
| DBM | data block message | ||
| DC | data code | ||
| DCE | data circuit-terminating equipment | ||
| DO | design objective | ||
| DTE | data terminal equipment | ||
| DTM | data text message | ||
| e.g. | for example | ||
| FCS | frame check sequence | ||
| FEC | forward error correction | ||
| FSK | frequency shift keying | ||
| Hz | hertz | ||
| HF | high frequency | ||
| HFNC | high frequency node controller | ||
| ID | identification | ||
| IFF | if and only if | ||
| ISDN | Integrated Services Digital Network | ||
| kHz | Kilohertz | ||
| LP | linking protection | ||
| LQA | link quality analysis | ||
| LSB | (1) lower sideband
(2) least significant bit | ||
| ms | millisecond | ||
| NATO | North Atlantic Treaty Organization | ||
| ITU | International Telecommunications Union | ||
| ISO | Organization of Standardization | ||
| FIPS | Federal Information Processing Standards | ||
| DODISS | Department of Defense Index of Specifications and Standards | ||
| DoD | Department of Defense | ||
| AQC | Alternative Quick Call | ||
| MF | medium frequency | ||
| MHz | megahertz | ||
| MP | multipath | ||
| MSB | most significant bit | ||
| NAK | negative-acknowledge character | ||
| NT | Not Tested | ||
| PL | probability of linking | ||
| PPM | parts per million | ||
| rf | radio frequency | ||
| REP | ALE preamble word REPEAT | ||
| RX | receive | ||
| s | second | ||
| SCTY | Security | ||
| SINAD | signal-plus-noise-plus-distortion to noise-plus-distortion ratio | |
| SN | Slot Number |
| SNR | signal to noise ratio | ||
| SPS | symbols per second | ||
| SSB | single-sideband [transmission] | ||
| TDMA | time-division multiple access | ||
| TIS | ALE preamble word THIS IS | ||
| TOD | time of day | ||
| TWAS | ALE preamble word THIS WAS | ||
| TX | transmit | ||
| UI | unique index | ||
| UUF | user unique function | ||
| UUT | units under test | ||
| WRTT | wait for response and tune timeout | |
| WS | AQC-ALE Word Sync word |
The abbreviations and acronyms used for timing symbols are contained
in annex A to this appendix.
The techniques specified in this appendix employ a robust modem
and forward error correction coding and constitutes a digital
ALE data link. The exchange of such ALE words according to the
specified protocols supports channel evaluation, selective calling,
and passing data messages and constitute an ALE data link layer.
(The ALE modem, radio, coupler, antenna, and so on constitute
the corresponding physical layer.)
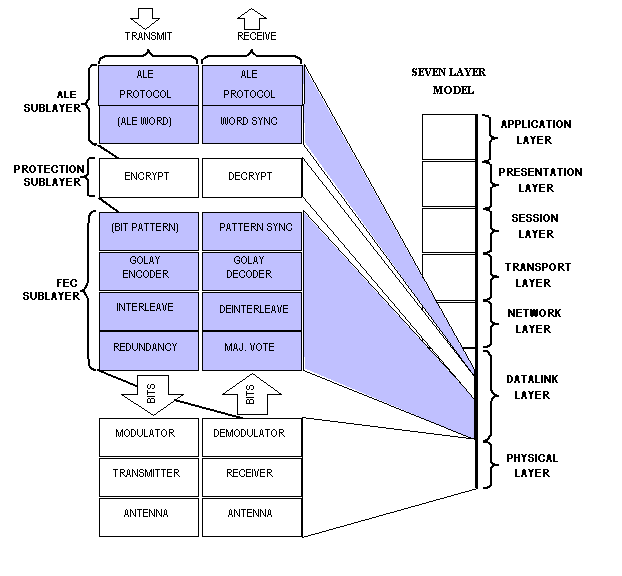
The ALE data link layer contains three sublayers, as shown in
figure A-1: a lower sublayer concerned with error correction
and detection (forward error correction [FEC] sublayer), an upper
sublayer containing the ALE protocol (ALE sublayer), and a linking
protection (LP) sublayer between. Within the FEC sublayer are
redundancy and majority voting, interleaving, and Golay coding
applied to the 24-bit ALE words which constitute the (FEC sublayer)
service-data-unit, in terms of the Seven Layer Reference Model.
The ALE sublayer specifies protocols for link establishment,
data communication, and rudimentary LQA based on the capability
of exchanging ALE words. The shaded area of figure A-1 indicates
the contents of this appendix.
The following paragraphs specify the general
requirements for ALE operation.
Stations designed to this appendix shall employ the addressing
structure specified in A.5.2.4 to identify individual stations
and collections of stations (nets and groups).
The radio system shall be capable of repeatedly scanning selected channels stored in memory (in the radio or controller) under either manual control or under the direction of any associated automated controller. The radio shall stop scanning and wait on the most recent channel upon the occurrence of any of the following selectable events:
The scanned channels should be selectable by groups (often called
"scan lists") and also individually within the groups,
to enable flexibility in channel and network scan management.

Upon request by the operator or an external automated controller,
the radio system shall execute the appropriate calling protocol
specified in A.5.5.
The radio system shall be capable of automatically transmitting
ALE sounding transmissions in accordance with A.5.3, and shall
automatically measure the signal quality of ALE receptions in
accordance with A.5.4.1.
Stations designed to this appendix shall demonstrate an overall
system performance equal to or exceeding the following requirements.
Stations designed to this appendix shall incorporate selectable
scan rates of two and five channels per second, and may also incorporate
other scan rates (design objective (DO): 10 channels per second).
In the optional AQC-ALE protocol, the system shall be capable
of variable dwell rates while scanning such that traffic can be
detected in accordance with table A-II Probability of Linking.
Radios equipped with the optional AQC-ALE shall provide scanning
at scan rates of two channels per second or five channels per
second for backward compatibility to non-AQC-ALE networks.
Stations designed to this appendix shall achieve at least the following probability of detecting the specified waveforms (See A.5.4.7) under the indicated conditions, with false alarm rates of no more than 1 percent. The channel simulator shall provide additive white gaussian noise (AWGN) without fading or multipath (MP). See table A-I.
| Waveform | SNR (dB in 3 kHz) | Dwell Time (s) | Detection Prob |
| ALE | 0 | 2.0 | 0.80 |
| 6 | 2.0 | 0.99 | |
| SSB Voice | 6 | 2.0 | 0.80 |
| 9 | 2.0 | 0.99 | |
| MIL-STD-188-110 | 0 | 2.0 | 0.80 |
| (Serial Tone PSK) | 6 | 2.0 | 0.99 |
| STANAG 4529 | 0 | 2.0 | 0.80 |
| 6 | 2.0 | 0.99 | |
| STANAG 4285 | 0 | 2.0 | 0.80 |
| 6 | 2.0 | 0.99 |
Baseband Signal Source | Baseband HF Channel Simulator | Rx Audio | ALE Controller UUT | |||
NOTES:
| ||||||
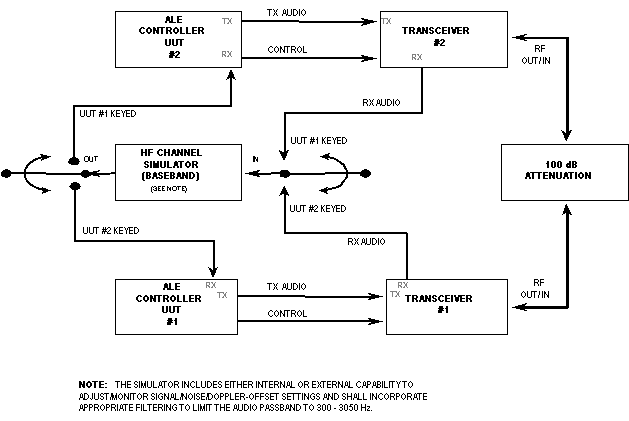
Linking attempts made with a test setup configured as shown in
figure A-3, using the specified ALE signal created in accordance
with this appendix, shall produce a probability of linking as
shown in table A-II.
| Signal-to-noise ratio (dB in 3 kHz) | |||
| Probability of
Linking (Pl) | Gaussian Noise Channel | Modified
CCIR Good Channel | Modified
CCIR Poor Channel |
| ³ 25%
³ 50% ³ 85% ³ 95% | -2.5
-1.5 -0.5 0.0 | +0.5
+2.5 +5.5 +8.5 | +1.0
+3.0 +6.0 +11.0 |
| Multipath (millisecond)
Doppler spread (Hertz) | 0.0
0.0 | 0.52
0.10 | 2.2
1.0 |
The receive audio input to the ALE controller shall be used to
simulate the three channel conditions. The modified International
Radio Consultative Committee (CCIR) good channel shall be characterized
as having 0.52 millisecond (ms) (modified from 0.50ms) MP delay
and a fading (two sigma) bandwidth of 0.1 hertz (Hz). The modified
CCIR poor channel, normally characterized as consisting of a circuit
having 2.0 ms MP delay with a fading (two sigma) bandwidth of
1.0 Hz, shall be modified to have 2.2 ms MP delay and a fading
(two sigma) bandwidth of 1.0 Hz. Doppler shifts of +60
Hz shall produce no more than a 1.0 decibel (dB) performance degradation
from the requirements of table A-II for the modified CCIR good
and poor channels.
NOTE: This modification is necessary due to the fact that the
constant 2-ms MP delay (an unrealistic fixed condition) of the
CCIR poor channel results in a constant nulling of certain tones
of the ALE tone library. Other tone libraries would also have
some particular MP value, which would result in continuous tone
cancellation during simulator testing.
Each of the signal-to-noise (SNR) ratio values shall be measured in a nominal 3-kiloHertz (kHz) bandwidth. Performance tests of this capability shall be conducted in accordance with ITU-R F.520-2 Use of High Frequency Ionospheric Channel Simulators employing the C.C. Watterson Model. This test shall use the individual scanning calling protocol described in A.5.5.3. The time for performance of each link attempt shall be measured from the initiation of the calling transmission until the successful establishment of the link. Performance testing shall include the following additional criteria:
a. The protocol used shall be the individual scanning calling protocol with only TO and TIS preambles.
b. Addresses used shall be alphanumeric, one word (three characters) in length from the 38-character basic American Standard Code for Information Interchange (ASCII) subset.
c. Units under test (UUTs) shall be scanning 10 channels at two channels per second, and repeated at five channels per seconds.
d. Call initiation shall be performed with the UUT transmitter stopped and tuned to the calling frequency.
e. Maximum time from call initiation (measured from the start
of UUT rf transmission -- not from activation of the ALE protocol)
to link establishment shall not exceed 14.000 seconds, plus simulator
delay time. The call shall not exceed 23 redundent words, the
response three redundent words and the acknowledgment three redundent
words. (See A.5.2.2.4 and Annex A).
NOTE: Performance at the higher scan rates shall also meet the
foregoing requirements and shall meet or exceed the probability
of linking as shown in table A-II.
When the optional AQC-ALE protocol is implemented, the probability of linking shall conform to table A-II with the following additional criteria:
a. The protocol used shall be quick AQC individual calling protocol with no message passing.
b. Addresses shall be one to six characters in the 38-character basic ASCII subset.
c. Units being called shall be scanning 10 channels.
d. Call initiation shall be performed with the UUT transmitter stopped and tuned to the calling frequency.
e. The initial call probe shall not exceed 10 Trw,
the call response shall not exceed 4Trw, and the acknowledgment
shall not exceed 2 Trw.
AQC-ALE linking performance shall not be degraded in LP level
1 or 2. Scan rates of two or five channels per second may degrade
performance because insufficient redundent words are emitted during
the call probe.
The equipment shall be capable of storing, retrieving, and employing
at least 100 different sets of information concerning channel
data to include receive and transmit frequencies with associated
mode information. See table A-III. The channel data storage
shall be nonvolatile.
The mode information normally includes:
Any channel (a) shall be capable of being recalled manually or
under the direction of any associated automated controller, and
(b) shall be capable of having its information altered after recall
without affecting the original stored information settings.
The radio shall be capable of storing, retrieving, and employing at least 20 different sets of information concerning self addressing. The self-address information storage shall be nonvolatile. These sets of information include self (its own personal) address(es), valid channels which are associated for use, and net addressing. Net addressing information shall include (for each "net member" self address, as necessary) the net address and the associated slot wait time (in multiples of Tw). See table A-IV and A.5.5.4.1. The slot wait time values are Tswt(slot number (SN)) from the formula, Tswt (SN) = Tsw x SN . Stations called by their net call address shall respond with their associated self (net member) address with the specified delay (Tswt(SN)). For example, the call is "GUY," thus the response is "BEN." Stations called individually by one of their self addresses (even if a net member address) shall respond immediately and with that address, as specified in the individual scanning calling protocol. Stations called by one of their self addresses (even if a net member address) within a group call shall respond in the derived slot, and with that address, as specified in the star group scanning protocol. If a station is called by one of its net addresses and has no associated net member address, it shall pause and listen but shall not respond (unless subsequently called separately with an available self or net member address), but shall enter the linked state.
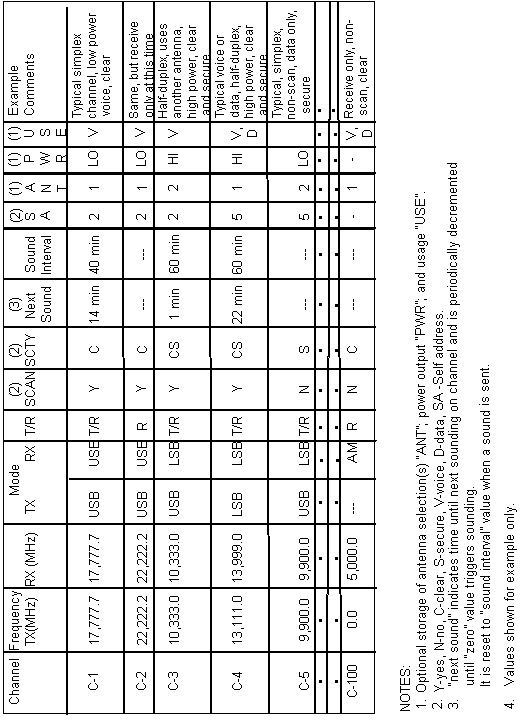
Index | Self (or Net Member) Address | Net Address | Tswt(SN)=
Slot Wait Time (Tw) | (4)
Valid Channels | Example Comments |
| SA1 | SAM | -- | -- | All | simple individual address, 1-word, all channels |
| SA2 | BOBBIE | -- | -- | C1,2,3 | simple individual address, 2-word, limited channels |
| SA3 | JIM | -- | -- | C7 | simple individual address, 1-word, single channel |
| SA4 | BEN | GUY | 14 | All | net and individual addresses, 1-word, all channels, preset slot unit time (slot 1) |
| SA5 | CLAUDETTE | GAL | 80 | C3-C7 | net and 3-word individual addresses, limited channels, preset slot wait-time (slot 4) |
| SA6 | JOE | PEOPLE | 17 | C1-C9 | 2-word net and 1-word individual addresses, limited channels preset slot wait-time |
| × | × | × | × | × | |
| × | × | × | × | × | |
| × | × | × | × | × | |
| SA20 | -- | PARTY | -- | C5-C12 | 2-word net only address, therefore receive only if called |
NOTES:
| |||||
The radio shall be capable of storing, retrieving, and employing
at least 100 different sets of information concerning the addresses
of other stations and nets, channel quality data to those stations
and nets (measurements or predictions), and equipment settings
specific to links with each station or net.
DO: any excess capacity which is not programmed with preplanned
other station information should be automatically filled with
any addresses heard on any of the scanned or monitored channels.
When the excess capacity is filled, it should be kept current
by replacing the oldest heard addresses with the latest ones heard.
This information should be used for call initiation to stations
(if needed), and for activity evaluation.
Individual station addresses shall be stored in distinct table
entries, and shall be associated with a specific wait for reply
time (Twr) if not the default value. Net information
shall include own net and net member associations, relative slot
sequences, and own net wait for reply times (Twrn)
for use when calling. See figure A-4. The storage for addresses
and settings shall be nonvolatile.
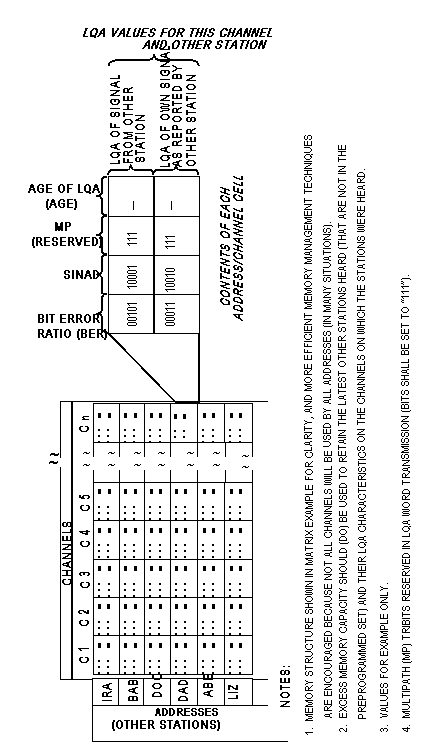
The equipment shall be capable of storing, retrieving, and employing
at least 4000 (DO: 10,000) sets of connectivity and LQA information
associated with the channels and the other addresses in an LQA
memory. The connectivity and LQA information storage shall be
retained in memory for not less than one hour during power down
or loss of primary power. The information in each address/channel
"cell" shall include as a minimum, bilateral SINAD values
of (a) the signals received at the station, and (b) the station's
signals received at, and reported by, the other station. It shall
also include either an indicator of the age of the information
(for discounting old data), or an algorithm for automatically
reducing the weight of data with time, to compensate for changing
propagation conditions. (DO: the cells of the LQA memory should
also include bilateral bit-error ratio (BER) and bilateral MP
information derived by suitably equipped units.) The information
within the LQA memory shall be used to select channels and manage
networks as stated in this document. See figure A-4.
DO: Equipment settings for use in linking with specific stations
or nets should be stored in nonvolatile memory. Such settings
may include antenna selection and azimuth, channels authorized
for that station or net, power limits for the relevant net, and
so on.
The following ALE operating parameters shall be programmable by
the operator or an external automated controller. Complete definitions
of the parameters are provided in Appendix H.
| ScanRate | RequestLQA | OtherAddr | LqaStatus |
| MaxScanChan | AutoPowerAdj | OtherAddrStatus | LqaAge |
| MaxTuneTime | SelfAddrTable | OtherAddrNetMembers | LqaMultipath |
| TurnAroundTime | SelfAddrEntry | OtherAddrValidChannels | LqaSINAD |
| ActivityTimeout | SelfAddr | OtherAddrAnt | LqaBER |
| ListenTime | SelfAddrStatus | OtherAddrAntAzimuth | ScanSet |
| AcceptAnyCall | NetAddr | OtherAddrPower | ConnectionTable |
| AcceptAllcall | SlotWaitTime | LqaMatrix | ConnectionEntry |
| AcceptAMD | SelfAddrValidChannels | LqaEntry | ConnectedAddr |
| AcceptDTM | OtherAddrTable | LqaAddr | ConnectionStatus |
| AcceptDBM | OtherAddrEntry | LqaChannel |
Storage for preprogrammed, operator entered, and incoming messages
shall be provided in the equipment. This storage shall be retained
in memory for not less than one hour during power down or loss
of primary power. Storage for at least 12 messages (DO: 100
messages), and a total capacity of at least 1000 characters (DO:
10,000 characters) shall be provided.
The ALE system shall incorporate the basic operational rules listed
in table A-V. Some of these rules may not be applicable in certain
applications. For example, "always listening" is not
possible while transmitting with a transceiver or when using a
common antenna with a separate transmitter and receiver.
| 1) Independent ALE receive capability (in parallel with other modems and simular audio receivers) (critical). |
| 2) Always listening (for ALE signals) (critical). |
| 3) Always will respond (unless deliberately inhibited). |
| 4) Always scanning (if not otherwise in use). |
| 5) Will not interfere with active channel carrying detectable traffic in accordance with table A-I (unless this listen call function is overriden by the operator or other controller). |
| 6) Always will exchange LQA with other stations when requested (unless inhibited), and always measures the signal quality of others. |
| 7) Will respond in the appropriate time slot to calls requiring slotted responses. |
| 8) Always seek (unless inhibited) and maintain track of their connectivities with others. |
| 9) Linking ALE stations employ highest mutual level of capability. |
| 10) Minimize transmit and receive time on channel. |
| 11) Automatically minimize power used (if capable). |
|
NOTE : Listed in order of precedence. |
This feature may be implemented in addition to the basic ALE functionality
described in this appendix. The AQC-ALE provides a link establishment
technique that requires significantly less time to link than the
baseline ALE system. This is accomplished by some additional
technology and trading-off some of the lesser used functions of
the baseline system, for a faster linking process. The AQC-ALE
shall always be listening for the baseline ALE call and shall
automatically respond and operate in that
mode when called.
The AQC-ALE format employs the following characteristics:
a. Packs three address characters (21 bits) into a 16-bit value
b. Addresses are reduced from a maximum of 15 characters to 6 characters
c. Six (6) address characters are sent in every transaction
d. Replaces two seldom used preambles as follows:
e. Isolates station addresses from message portion of the signaling structure:
f. Easy separation of second generation basic ALE and AQC-ALE protocols:
g. Provides at least eight information bits per transmission
The following basic ALE features are fully implemented using the
AQC-ALE protocol.
NOTE: A station operating in AQC-ALE can respond to any call type, but a station equipped with only second generation basic ALE will not respond to AQC-ALE protocol forms.
a. Linking protection levels 0, 1, 2, 3
b. Unit calls
c. Star Net calls
d. Allcalls
e. AnyCalls
f. LQA Exchange as part of the call handshake
g. Supports Orderwire and Relay features while in a link:
h. Sound:
a. Group call. As an alternative, a controller can use the calling protocol to add on additional members. Behavior of the system is more akin to setting up a call and then conferencing in a third party.
b. AMD, DTM, DBM are not provided during link set up. Primary focus of AQC-ALE is to establish a link between two or more stations as rapidly as possible. Once linked, information can be exchanged in the most efficient manner as is common between stations.
c. Early identification of transmitter's address during orderwire
traffic or additional addressing identification for relay addresses.
The need for this is eliminated because the call setup is significantly
reduced. Orderwire messages are not allowed during the call setup.
The ALE waveform is designed to pass through the audio passband
of standard SSB radio equipment. This waveform shall provide
for a robust, low-speed, digital modem capability used for multiple
purposes to include selective calling and data transmission.
This section defines the waveform including the tones, their meanings,
the timing and rates, and their accuracy.
The waveform shall be an 8-ary frequency shift-keying (FSK) modulation with eight orthogonal tones, one tone (or symbol) at a time. Each tone shall represent three bits of data as follows (least significant bit (LSB) to the right):
The transmitted bits shall be encoded and interleaved data bits
constituting a word, as described in paragraphs A.5.2.2 and A.5.2.3.
The transitions between tones shall be phase continuous and shall
be at waveform maxima or minima (slope zero).
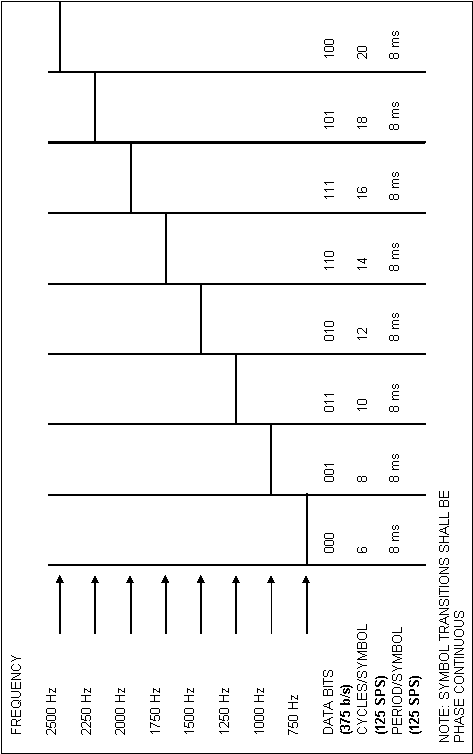
The tones shall be transmitted at a rate of 125 tones (symbols)
per second, with a resultant period of 8 ms per tone. Figure
A-5 shows the frequency and time relationships. The transmitted
bit rate shall be 375 bits per second (b/s). The transitions
between adjacent redundant (tripled) transmitted words shall coincide
with the transitions between tones, resulting in an integral
49 symbols (or tones) per redundant (tripled) word. The resultant
single word period (Tw) shall be 130.66... ms (or 16.33...
symbols), and the triple word (basic redundant format) period
(3 Tw) shall be 392 ms.
At baseband audio, the generated tones shall be within +1.0
Hz. At rf, all transmitted tones shall be within the range of
2.0 dB in amplitude. Transmitted symbol timing, and therefore,
the bit and word rates shall be within ten parts per million.
This section provides definition of the ALE signal structure.
Included are: forward error correction, word structure, addressing,
frame structure, and synchronization. Also described in this
section are: addressing, signal quality analysis, and the functions
of the standard word preambles associated with the signal structure.
The effective performance of stations, while communicating over
adverse rf channels, relies on the combined use of forward error
correction, interleaving, and redundancy. These functions shall
be performed within the transmit encoder and receive decoder.
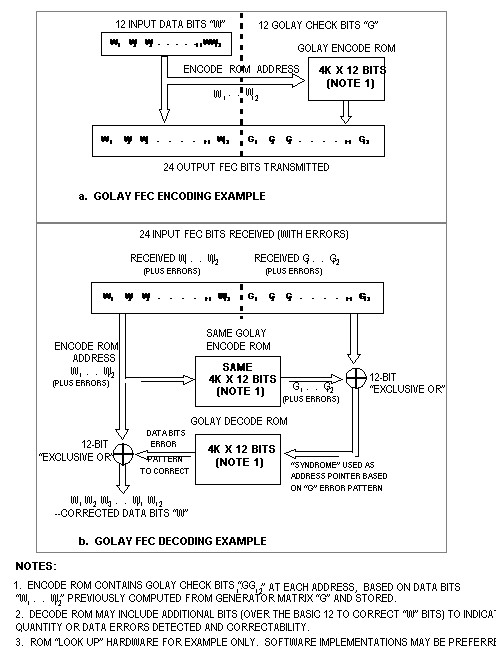
The generator matrix G, derived from g(x), shall contain an identity
matrix I12 and a parity matrix P as shown in figure
A-6. The corresponding parity check matrix H shall contain a
transposed matrix pT and an identity matrix I12
as shown in figure A-7.
where y = x + e is a received vector which is the modulo-2 sum
of a code word x and an error vector e, s is a vector of "n
- k" bits called the syndrome. See figure A-9. See figure
A-7 for the value of H. Each correctable/detectable error vector
e results in a unique vector s. Because of this, s is computed
according to the equation above and is used to index a look-up
of the corresponding e, which is then added modulo-2 to y to give
the original code word x. Flags are set according to the number
of errors being corrected. The uses of the flags are described
in A.5.2.6. If s is not equal to 0 and e contains more ones than
the number of errors being corrected by decoding mode, a detected
error is indicated and the appropriate flag is set.
| I12 | P | |||||||||
| 100 | 000 | 000 | 000 | : | 101 | 011 | 100 | 011 | ||
| 010 | 000 | 000 | 000 | : | 111 | 110 | 010 | 010 | ||
| 001 | 000 | 000 | 000 | : | 110 | 100 | 101 | 011 | ||
| 000 | 100 | 000 | 000 | : | 110 | 001 | 110 | 110 | ||
| 000 | 010 | 000 | 000 | : | 110 | 011 | 011 | 001 | ||
| 000 | 001 | 000 | 000 | : | 011 | 001 | 101 | 101 | ||
| G= | 000 | 000 | 100 | 000 | : | 001 | 100 | 110 | 111 | |
| 000 | 000 | 010 | 000 | : | 101 | 101 | 111 | 000 | ||
| 000 | 000 | 001 | 000 | : | 010 | 110 | 111 | 100 | ||
| 000 | 000 | 000 | 100 | : | 001 | 011 | 011 | 110 | ||
| 000 | 000 | 000 | 010 | : | 101 | 110 | 001 | 101 | ||
| 000 | 000 | 000 | 001 | : | 010 | 111 | 000 | 111 | ||
| PT | I12 | |||||||||
|
| ||||||||||
| 111 | 110 | 010 | 010 | : | 100 | 000 | 000 | 000 | ||
| 011 | 111 | 001 | 001 | : | 010 | 000 | 000 | 000 | ||
| 110 | 001 | 110 | 110 | : | 001 | 000 | 000 | 000 | ||
| 011 | 000 | 111 | 011 | : | 000 | 100 | 000 | 000 | ||
| 110 | 010 | 001 | 111 | : | 000 | 010 | 000 | 000 | ||
| H= | 100 | 111 | 010 | 101 | : | 000 | 001 | 000 | 000 | |
| 101 | 101 | 111 | 000 | : | 000 | 000 | 100 | 000 | ||
| 010 | 110 | 111 | 100 | : | 000 | 000 | 010 | 000 | ||
| 001 | 011 | 011 | 110 | : | 000 | 000 | 001 | 000 | ||
| 000 | 101 | 101 | 111 | : | 000 | 000 | 000 | 100 | ||
| 111 | 100 | 100 | 101 | : | 000 | 000 | 000 | 010 | ||
| 101 | 011 | 100 | 011 | : | 000 | 000 | 000 | 001 | ||
| 12 Bits To Encode | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Bit Numbers | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| *See note 2
NOTES:
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
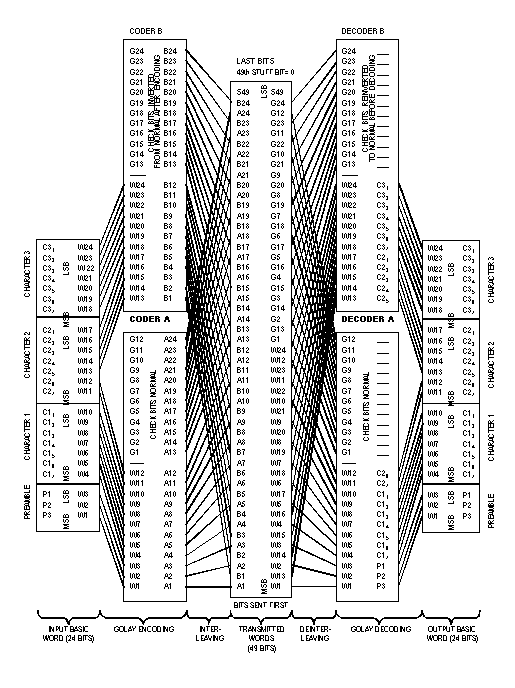
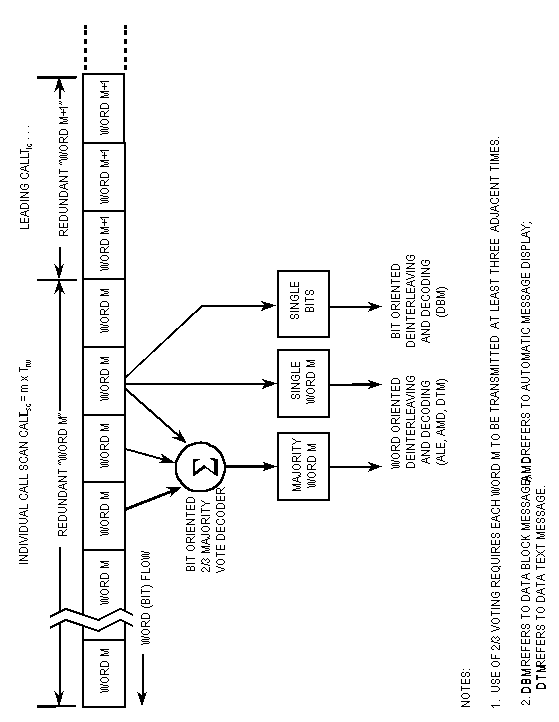
Each of the transmitted 49-bit (or 16-1/3 symbol) (Tw)
words shall be sent redundantly (times 3) to reduce the effects
of fading, interference, and noise. An individual (or net) routing
word (TO...), used for calling a scanning (multichannel)
station (or net), shall be sent redundantly as long as required
in the scan call (Tsc) to ensure receipt, as described
in A.5.5.2. However, when the call is a non-net call to multiple
scanning stations (a group call, using THRU and REPEAT
(REP) alternately), the first individual routing word
(THRU) and all the subsequent individual routing words
(REP, THRU, REP,...) shall be sent three
adjacent times (Trw). These triple words for the individual
stations shall be rotated in group sequence as described in A.5.5.3.
See figure A-11. At bit time intervals (approximately Tw/49),
the receiver shall examine the present bit and past bit stream
and perform a 2/3 majority vote, on a bit-by-bit basis, over a
span of three words. See tables A-VI and A-VII. The resultant
48 (ignoring the 49th bit) most recent majority bits constitute
the latest majority word and shall be delivered to the deinterleaver
and FEC decoder. In addition, the number of unanimous votes of
the 48 possible votes associated with this majority word are temporarily
retained for use as described in A.5.2.6.
The basic ALE word shall consist of 24 bits of information, designated
W1 (MSB) through W24 (LSB). The bits shall be designated as shown
in figure A-12.
Received Bit R | Received Time | Eight Possible Bit Combinations | |||||||
| R (n) (now) | T | 0 | 0 | 0 | 0 | 1 | 1 | 1 | 1 |
| R(n-49) (Tw old) | T-130.66... ms | 0 | 0 | 1 | 1 | 0 | 0 | 1 | 1 |
| R(n-98) (2 Tw old) | T-261.33... ms | 0 | 1 | 0 | 1 | 0 | 1 | 0 | 1 |
| Resultant majority bit M: | 0 | 0 | 0 | 1 | 0 | 1 | 1 | 1 | |
| Possible error flag: | 0 | 1 | 1 | 1 | 1 | 1 | 1 | 0 | |
| 0 = error unlikely
1 = error likely | |||||||||
Relative Time | Received Bits R (Time) for 2/3 Voting | Majority Words Bit M | Used as Decoder Bits | ||
| Stuff bits
Recent (LSB) Older (MSB) | R(n)
R(n-1) R(n-2) R(n-3) R(n-4)
R(n-46) R(n-47) R(n-48) | R(n-49)
R(n-50) R(n-51) R(n-52) R(n-53)
R(n-95) R(n-96) R(n-97) | R(n-98)
R(n-99) R(n-100) R(n-101) R(n-102)
R(n-144) R(n-145) R(n-146) | M(n)
M(n-1) M(n-2) M(n-3) M(n-4)
M(n-46) M(n-47) M(n-48) | S49 ignored
B24 (LSB) A24 B23 A23
A2 B1 A1 (MSB) |
NOTES:
| |||||
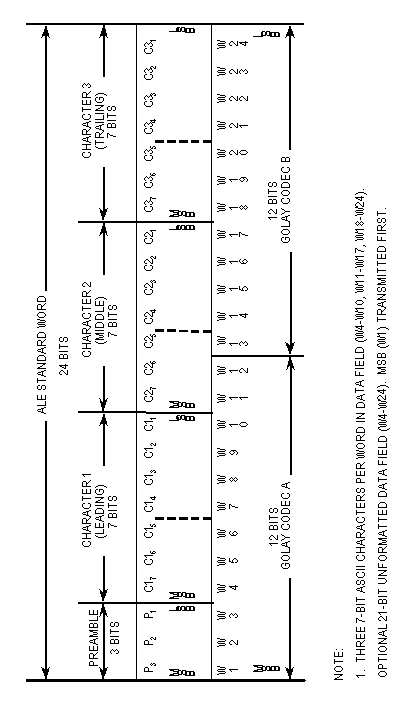
The leading three bits, W1 through W3, are designated preamble
bits P3 through P1, respectively. These preamble bits shall be
used to identify one of eight possible word types.
Optional AQC-ALE preambles are defined in A.5.8.1.2.
| Word
Type | Code Bits | Functions | Significance | ||
| THRU | 001 | multiple (and indirect routing | present multiple direct destinations for group calls (and future indirect relays, reserved) | ||
| TO | 010 | direct routing | present direct destination for individual and net calls | ||
| CMD | 110 | orderwire control and status | ALE system-wide station (and operator) orderwire for coordination, control, status, and special functions | ||
| FROM | 100 | identification (and indirect routing) | identification of present transmitter without termination (and past originator and relayers, reserved) | ||
| TIS | 101 | terminator and identification continuing | identification of present transmitter, signal terminations, protocol continuation | ||
| TWAS | 011 | terminator and identification quitting | identification of present transmitter, signal and protocol termination | ||
| DATA | 000 | extension and information | extension of data field of the previous ALE work, or information defined by the previous CMD | ||
| REP | 111 | duplication and information | duplication of the previous preamble, or information defined by the previous CMD | ||
| P3
MSB W1 | P2 W2 | P1
LSB W3 | |||
The TIS word (101) shall be used as a routing designator
which shall indicate the address of the present calling (or sounding)
station which is directly transmitting the call (or sound). Except
for the use of TWAS, TIS shall be used in all ALE
protocols to terminate the ALE frame and transmission. It shall
indicate the continuation of the protocol or handshake, and shall
direct, request, or invite (depending on the specific protocol)
responses or acknowledgments from other called or receiving stations.
The TIS shall be used to designate the call acceptance
sound. The TIS word itself shall contain the first three
characters of the calling stations address. For extended addresses,
the additional address words (and characters) shall be contained
in alternating DATA and REP words which shall immediately
follow, exactly as described for whole addresses using the TO
word and sequence. The entire address (and the required portion
of the TIS, DATA, REP, DATA, REP
sequence, as necessary) shall be used only in the conclusion section
of the ALE frame (or shall constitute an entire sound). TWAS
shall not be used in the same frame as TIS, as they are
mutually exclusive.
The THRU word (001) shall be used in the scanning call
section of the calling cycle only with group call protocols.
The THRU word shall be used alternately with REP,
as routing designators, to indicate the address first word of
stations that are to be directly called. Each address first word
shall be limited to one basic address word (three characters)
in length. A maximum of five different address first words shall
be permitted in a group call. The sequence shall only be alternations
of THRU, REP. The THRU shall not be used
for extended addresses, as it will not be used within the leading
call section of the calling cycle. When the leading call starts
in the group call, the entire group of called stations shall be
called with their whole addresses, which shall be sent using the
TO preambles and structures, as described in A.5.2.3.2.1.
NOTE: 1. The THRU word is also reserved for future implementation
of indirect and relay protocols, in which cases it may be used
elsewhere in the ALE frame and with whole addresses and other
information. Stations designed in compliance with this nonrelay
standard should ignore calls to them which employ their address
in a THRU word in other than the scanning call.
NOTE: 2. The THRU preamble value is also reserved for
the AQC-ALE protocol.
NOTE: 1. The FROM word is also reserved for future implementation
of indirect and relay protocols, in which cases it may be used
elsewhere in the ALE frame and with multiple addresses and other
information. Stations designed in compliance with this nonrelay
standard should ignore sections of calls to them that employ FROM
words in any other sequence than immediately before the CMD
word.
NOTE: 2. The FROM preamble value is also reserved for
the AQC-ALE protocol.
All message words (orderwire messages) begin with a word with
the CMD preamble.
The CMD word (110) is a special orderwire designator which
shall be used for system-wide coordination, command, control,
status, information, interoperation, and other special purposes.
CMD shall be used in any combination between ALE stations
and operators. CMD is an optional designator which is used
only within the message section of the ALE frame, and it shall
have (at some time in the frame) a preceding call and a following
conclusion, to ensure designation of the intended receivers and
identification of the sender. The first CMD terminates
the calling cycle and indicates the start of the message section
of the ALE frame. The orderwire functions are directed with the
CMD itself, or when combined with the REP and DATA
words. See A.5.6 for message words (orderwire messages) and functions.
The DATA word (000) is a special designator which shall
be used to extend the data field of any previous word type (except
DATA itself) or to convey information in a message. When
used with the routing designators TO, FROM, TIS,
or TWAS, DATA shall perform address extension from
the basic three characters to six, nine, or more (in multiples
of three) when alternated with REP words. The selected
limit for address extension is a total of 15 characters. When
used with CMD, its function is predefined as specified
in A.5.6 for message words (orderwire messages) and functions.
The REP word (111) is a special designator which shall
be used to duplicate any previous preamble function or word meaning
while changing the data field contents (bits W4 through W24).
See table A-VIII. Any change of words or data field bits requires
a change of preamble bits (P3 through P1)
to preclude uncertainty and errors. If a word is to change, even
if the data field is identical to that in the previous word, the
preamble shall be changed, thereby clearly designating a word
change. When used with the routing designator TO, REP
performs address expansion, which enables more than one address
to be specified. See A.5.2.3.2.4 for use with THRU. With
DATA, REP may be used to extend and expand address,
message, command, and status fields. REP shall be used
to perform these functions, and it may directly follow any other
word type except for itself, and except for TIS or TWAS,
as there cannot be more than one transmitter for a specific call
at a given time.
NOTE 1. REP is used in Tsc of group calls directed
to units with different first word addresses.
NOTE 2. REP is not used in Tsc of calls directed
to groups with same first word addresses. Also REP is
not used in Tsc of calls directed to individuals and
nets.
The ALE system deploys a digital addressing structure based upon the standard 24-bit (three character) word and the Basic 38 character subset. As described below, ALE stations have the capability and flexibility to link or network with one or many prearranged or as-needed single or multiple stations. All ALE stations shall have the capacity to store and use at least 20 self addresses of up to 15 characters each in any combination of individual and net calls. There are three basic addressing methods which will be presented:
NOTE: Certain alphanumeric address combinations may be interpreted
to have special meanings for emergency or specific functions,
such as "SOS," "MAYDAY," "PANPAN,"
"SECURITY," "ALL," "ANY," and "NULL."
These should be carefully controlled or restricted.
The ALE basic address structure is based on single words which,
in themselves, provide multiples of three characters. The quantity
of available addresses within the system, and the flexibility
of assigning addresses, are significantly increased by the use
of address character stuffing. This technique allows address
lengths that are not multiples of three to be compatibly contained
in the standard (multiple of three characters) address fields
by "stuffing" the empty trailing positions with the
utility symbol "@." See table A-IX. "Stuff-1"
and "Stuff-2" words shall only be used in the last word
of an address, and therefore should appear only in the leading
call (Tlc) of the calling cycle (Tcc).
NOTE: As an example of proper usage, a call to the address "MIAMI"
would be structured "TO MIA," "DATA
MI@."
The fundamental address element in the ALE system is the single
routing word, containing three characters, which forms the basic
individual station address. This basic address word, used primarily
for intranet and slotted operations, may be extended to multiple
words and modified to provide increased address capacity and flexibility
for internet and general use. An address which is assigned to
a single station (within the known or used network) shall be termed
an "individual" address. If it consists of one word
(that is, no longer than three characters) it shall be termed
a "basic" size, and if it exceeds one word, it shall
be termed an "extended" size.
| TO
A B C | "Standard" three character address structure "ABC" | Any position in address and sequences | ||
| TO
A B @ | "Stuff-1" reduced address fields; adds characters "A, B" | Only last word in address; anywhere in sequences | ||
| TO
A @ @ | "Stuff-2" reduced address fields; adds character "A" | Only last word in address; anywhere in sequences | ||
| TO
@ ? @ | "Allcall" global address; all stop and listen (unless inhibited), none respond | Exclusive member of calling cycle; single TO only | ||
| TO REP
@ A @ @ B @ (option) | "Selective AllCall;" global address; all with same last character "A" (or "B") stop and listen (unless inhibited), none respond | Alone, or with additional different AllCall selections, for "group selective AllCall;" only in calling cycle; must use TO, REP alternately never DATA, if more than one* | ||
| TO
@ @ ? | "AnyCall" global address; all stop and respond in PRN slots (unless inhibited), none respond | Exclusive member of calling cycle; single TO only | ||
| TO REP
@ @ A @ B@ (option) | "Selective AnyCall;" all with same last character(s) "A" (or "B") stop and respond in PRN slots (unless inhibited), using own addresses | Alone or with additional different AnyCall selections, for "group selective AnyCall;" only in calling cycle; must use TO, REP alternately (never DATA), if more than one* | ||
| TO REP
@ A B @ C D (option) | "Double selective AnyCall;" all with same last characters "AB" (or "CD") stop and respond in PRN slots (unless inhibited), using own addresses | Alone or with additional different AnyCall selections, for "group selective AnyCall;" only in calling cycle; must use TO, REP alternately (never DATA), if more than one* | ||
| TO
@ @ @ | "Null" address; all ignore, test and maintenance use, or extra "buffer" slot | Any position in address sequence (omit from Tsc if group call) except never in conclusion (terminator), or REP, only if following TO | ||
NOTES:
* THRU, REP in Tsc if group call. | ||||
The basic address word shall be composed of a routing preamble
(TO, or possibly a REP which follows a TO,
in Tlc of group call, or a TIS or TWAS)
plus three address characters, all of which shall be alphanumeric
numbers of the Basic 38 subset. The three characters in the basic
individual address provide a Basic 38-address capacity of 46,656,
using only the 36 alphanumerics. This three-character single
word is the minimum structure. In addition, all ALE stations
shall associate specific timing and control information with all
own addresses, such as prearranged delays for slotted net responses.
As described in A.5.5, the basic individual addresses of various
station(s) may be combined to implement flexible linking and networking.
NOTE: All ALE stations shall be assigned at least one (DO: several)
single-word address for automatic use in one-word address protocols,
such as slotted (multistation type) responses. This is a mandatory
user requirement, not a design requirement. However, nothing
in the design shall preclude using longer addresses.
Extended addresses provide address fields which are longer than
one word (three characters), up to a maximum system limit of five
words (15 characters). See table A-X. This 15-character capacity
enables Integrated Services Digital Network (ISDN) address capability.
Specifically, the ALE extended address word structure shall be
composed of an initial basic address word, such as TO or
TIS, as described above, plus additional words as necessary
to contain the additional characters in the sequence DATA,
REP, DATA, REP, for a maximum total of five
words. All address characters shall be the alphanumeric members
of the Basic 38 subset.
NOTE 1: All ALE stations shall be assigned at least one (DO:
several) two-word address(es) for general use, plus an additional
address(es) containing the station's assigned call sign(s). This
is a mandatory user requirement, not a design requirement. However,
nothing in the design shall preclude using longer addresses.
NOTE 2: The recommended standard address size for intranet, internet,
and general non-ISDN use is two words. Any requirement to operate
with address sizes larger than six characters must be a network
management decision. As examples of proper usage, a call to "EDWARD"
would be "TO EDW," "DATA ARD,"
and a call to "MISSISSIPPI" would be "TO
MIS," "DATA SIS," "REP
SIP," "DATA PI@."
Words | Address
Characters | Types |
|
| B | 1 | 1 | Stuff-2 |
| A | |||
| S | 1 | 2 | Stuff-1 |
| I | |||
| C | 1 | 3 | Basic |
|
E X T E N D E
D |
2
2
2
3
3
3
4
4
4
5
5 5 (limit) |
4
5
6
7
8
9
10
11
12
13
14 15 (limit) |
Basic +
Stuff-2 Basic +
Stuff-1
2 Basic 2 Basic +
Stuff-2 2 Basic +
Stuff-1
3 Basic 3 Basic +
Stuff-2 3 Basic +
Stuff-1
4 Basic 4 Basic +
Stuff-2 4 Basic +
Stuff-1 5 Basic (limit) |
NOTES:
| |||
The purpose of a net call is to rapidly and efficiently establish
contact with multiple prearranged (net) stations (simultaneously
if possible) by the use of a single net address, which is an additional
address assigned to all net members in common. When a net address
type function is required, a calling ALE station shall use an
address structure identical to the individual station address,
basic or extended as necessary. For each net address at a net
member's station, there shall be a response slot identifier, plus
a slot width modifier if directed by the specific standard protocol.
As described in paragraphs A.5.5.3 and A.5.5.4, additional information
concerning the assigned response slots (and size) must be available,
and the mixing of individual, net, and group addresses and calls
is restricted
The purpose of a group call is to establish contact with multiple
nonprearranged (group) stations (simultaneously if possible) rapidly
and efficiently by the use of a compact combination of their own
addresses which are assigned individually. When a group address
type function is required, a calling ALE station shall use a sequence
of the actual individual station addresses of the called stations,
in the manner directed by the specific standard protocol. A station's
address shall not appear more than once in a group calling sequence,
except as specifically permitted in the group calling protocols
described in A.5.5.4.
NOTE: The group feature is not available
in the AQC-ALE protocol.
An "AllCall" is a general broadcast that does not request
responses and does not designate any specific address. This mechanism
is provided for emergencies ("HELP!"), broadcast data
exchanges, and propagation and connectivity tracking. The global
AllCall address is "@?@." The AllCall protocol
is discussed in A.5.5.4.4. As a variation on the AllCall, the
calling station can organize (or divide) the available but unspecified
receiving stations into logical subsets, using a selective AllCall
address. A selective AllCall is identical in structure, function,
and protocol to the AllCall except that it specifies the last
single character of the addresses of the desired subgroup of receiving
stations (1/36 of all). By replacing the "?" with an
alphanumeric, the selective AllCall special address pattern is
"TO @A@" (or possibly "THRU
@A@" and "REP @B@" if more
than one subset is desired), where "A" (and "B,"
if applicable) in this notation represents any of the 36 alphanumerics
in the Basic-38 subset. "A" and "B" may represent
the same or different character from the subset, and specifically
indicate which character(s) must be last in a station's address
in order to stop scan and listen.
NOTE: For ACQ-ALE, the Part2 address portion shall contain
the same three characters used in the TO word of the call.
An "AnyCall" is a general broadcast that requests responses without designating any specific addressee(s). It is required for emergencies, reconstitution of systems, and creation of new networks. An ALE station may use the AnyCall to generate responses from essentially
unspecified stations, and it thereby can identify new stations
and connectivities. The global AnyCall address is "@@?."
The AnyCall protocol is discussed in A.5.5.4.5. If too many
responses are received to an AnyCall, or if the caller must organize
the available but unspecified responders into logical subsets,
a selective AnyCall protocol is used. The selective AnyCall address
is identical in structure, function, and protocol to the global
AnyCall, except that it specifies the last single character of
the addresses of the desired subset of receiving station (1/36
of all). By replacing the "?" with an alphanumeric,
the global AnyCall becomes a selective AnyCall whose special address
pattern is "TO @@A."
If even narrower acceptance and response criteria are required,
the double selective AnyCall should be used. The double selective
AnyCall is an operator selected general broadcast which is identical
to the selective AnyCall described above, except that its special
address (using "@AB" format) specifies the last
two characters that the desired subset of receiving stations must
have to initiate a response.
NOTE: For ACQ-ALE, the Part2 address portion shall contain
the same three characters used in the TO word of the call.
A "wildcard" is a special character that the caller
uses to address multiple-station addresses with a single-call
address. The receivers shall accept the wildcard character as
a substitute for any alphanumeric in their self addresses in the
same position or positions. Therefore, each wildcard character
shall substitute for any of 36 characters (A to Z, 0 to 9) in
the Basic 38-character subset. The total lengths of the calling
(wildcard) address, and the called addresses shall be the same.
The special wildcard character shall be "?"
(0111111). It shall substitute for any alphanumeric in the Basic
38-character subset. It shall substitute for only a single-address
character position in an address, per wildcard character. See
table A-XI for examples of acceptable patterns.
For self test, maintenance, and other purposes, stations shall
be capable of using their own self addresses in calls. When a
self-addressing type function is required, ALE stations shall
use the following self-addressing structures and protocols. Any
ALE calling structures and protocols permissible within this standard,
and containing a specifically addressed calling cycle (such as
"TO ABC," but not AllCall or AnyCall),
shall be acceptable, except that the station may substitute (or
add) any one (or several) of its own calling addresses into the
calling cycle.
For test, maintenance, buffer times, and other purposes, the station
shall use a null address that is not directed to, accepted by,
or responded to by any station. When an ALE station requires
a null address type function, it shall use the following null
address protocol. The null address special address pattern shall
be "TO @@@," (or "REP @@@"),
if directly after another TO. The null address shall only
use the TO (or REP), and only in the calling cycle
(Tcc). Null addresses may be mixed with other addresses
(group call), in which case they shall appear only in the leading
call (Tlc), and not in the scanning call (Tsc).
Nulls shall never be used in conclusion (terminator) (TIS
or TWAS). If a null address appears in a group call, no
station is designated to respond in the associated slot; therefore,
it remains empty (and may be used as a buffer for tune-ups, or
overflow from the previous slot's responder, etc.).
The inlink address feature is used by a system to denote that
all members in the established link are to act upon the information
sent in the frame containing the inlink address. The inlink address
shall be '?@?'. When a radio enters the linked condition with
one or more stations, the radio shall expand the set of recognized
self addresses to include the inlink address ('?@?'). When a
frame is transmitted by any member of the link using the inlink
address, all members are thus addressed publicly and are to use
the frame information. Thus, if a linked member sent an AMD message,
all members would present that message to their user. If the
member sent a frame terminated with a TWAS preamble, then all
members would note that the transmitting station just 'left' the
link. Short messages of 'to-F?@?, to-?@?, tis-TALKINGMEMBER'
would act as a keep-alive function and cause the receiving radio
to extend any link termination timer.
All ALE transmissions are based on the tones, timing, bit, and
word structures described in paragraphs A.5.1 and A.5.2.3. All
calls shall be composed of a "frame," which shall be
constructed of contiguous redundant words in valid sequence(s)
as described in figure A-14, as limited in table A-VII, and in
formats as described in A.5.5. There are three basic frame sections:
calling cycle, message, and conclusion. See A.5.2.5.5 for basic
frame structure examples.
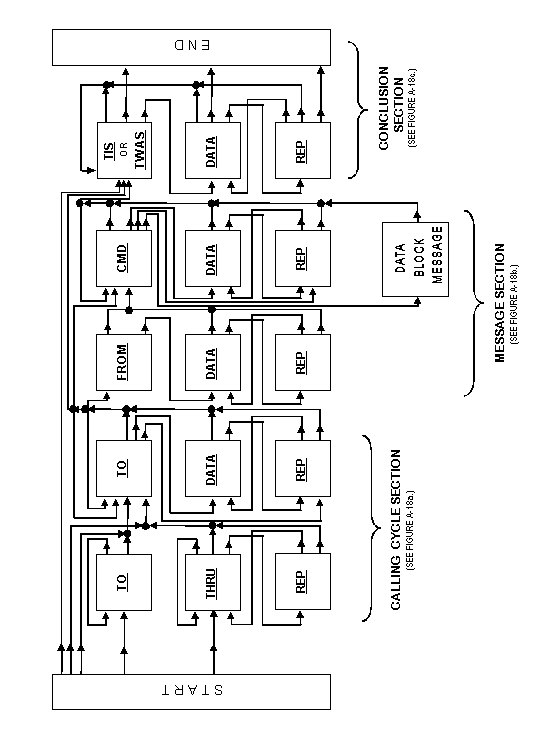
The initial section of all frames (except sounds) is termed a
calling cycle (Tcc), and it is divided into two parts:
a scanning call (Tsc) and a leading call (Tlc).
The scanning call shall be composed of TO words if an
individual or net call (or THRU and REP words, alternating,
if a group call), which contain only the first word(s) of the
called station(s) or net address. The leading call shall be composed
of TO (and possibly DATA and REP) words containing
the whole address(es) for the called station(s), from initiation
of the leading call until the start of the message section or
the conclusion (thus the end of the calling cycle). See figure
A-15. The use of REP and DATA is described in A.5.2.4.
The set of different address first words (Tcl) may
be repeated as necessary for scanning calling (Tsc),
to exceed the scan period (Ts). There is no unique
"flag word" or "sync word" for frame synchronization
(as discussed below). Therefore, stations may acquire and begin
to read an ALE signal at any point after the start. The transmitter
shall have reached at least 90 percent of the selected rf power
within 2.5 ms of the first tone transmission following call initiation.
The end of the calling cycle may be indicated by the start of
the optional quick-ID, which occupies the first words in the message
section, after the leading call and before the start of the rest
of the message (or conclusion, if no message) section.
NOTE 1: The frame time may need to be delayed (equipment manufacturer
dependent) to avoid loss of the leading words if the transmitter
attack time is significantly long. Alternatively, the modem may
transmit repeated duplicates of the scanning cycle (set of) first
word(s) to be sent (not to be counted in the frame) as the transmitter
rises to full power (and may even use the ALE signal momentarily
instead of a tuning tone for the tuner), and then start the frame
when the power is up.
NOTE 2: The 2.5-ms permissible delay of the first ALE tone, after
the transmitter has reached 90 percent of selected power, is in
addition to the allowable attack time delay specified in 5.3.5.1.
NOTE 3: Non-compliance with the 90 percent of power parameter
will impact the probability of linking. Compliance testing for
this can be construed to be met if the probability of linking
criteria is met (see table A-I).
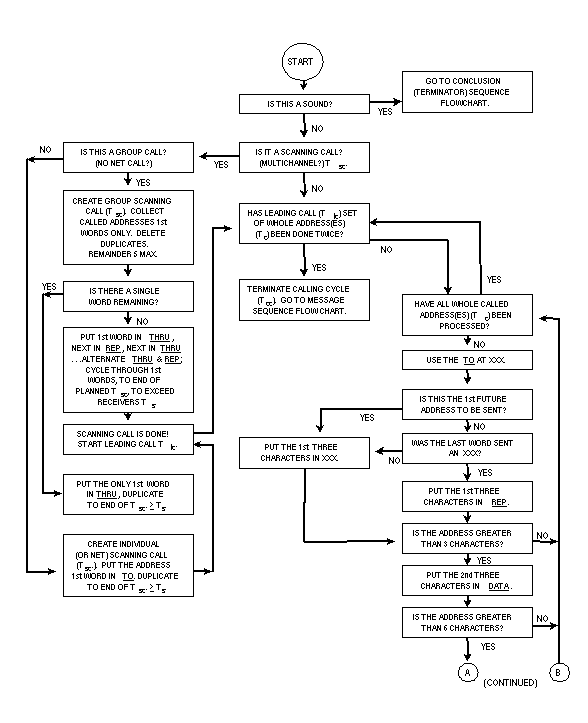
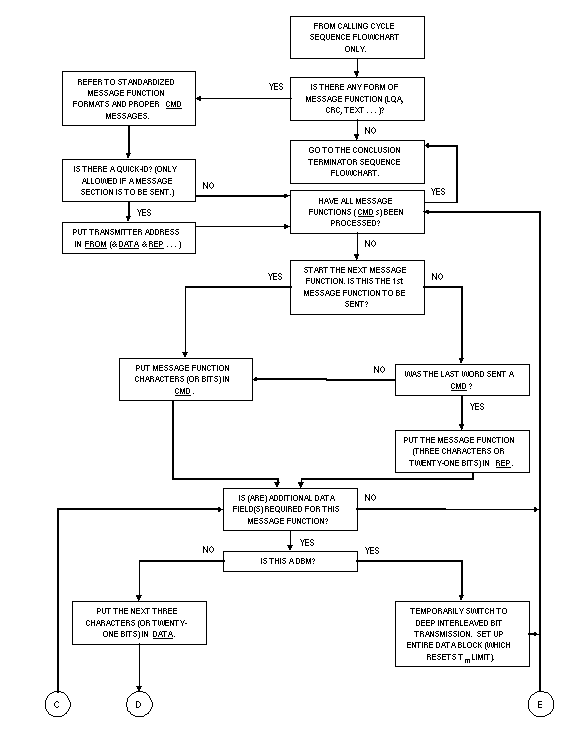
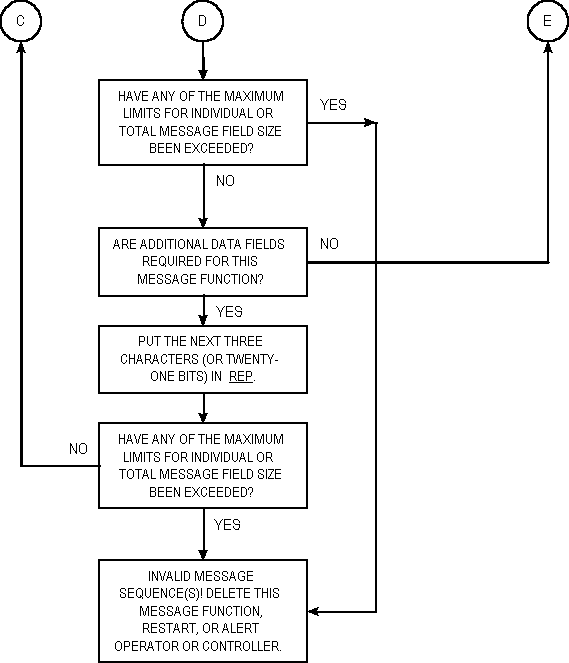
The second and optional section of all frames (except sounds)
is termed a "message." Except for the quick-ID, it
shall be composed of CMD (and possibly REP and DATA)
words from the end of the calling cycle until the start of the
conclusion (thus the end of the message). The optional quick-ID
shall be composed of FROM (and possibly REP and
DATA) word(s), containing the transmitter's whole address.
It shall only be used once at the start of the CMD message
section sequences. The quick-ID enables prompt transmitter identification
and should be used if the message section length is a concern.
It is never used without a following (CMD...) message(s).
The message section shall always start with the first CMD
(or FROM with later CMD(s)) in the call. See figure
A-16. The use of REP and DATA is described in A.5.7.3.
The message section is not repeated within the call (although
messages or information itself, within the message section, may
be).
For AQC-ALE, the message section in AQC-ALE is available when
in a link. The acknowledgement leg (third leg) of a call may
be used as an inlink entry condition. See A.5.8.2.3.
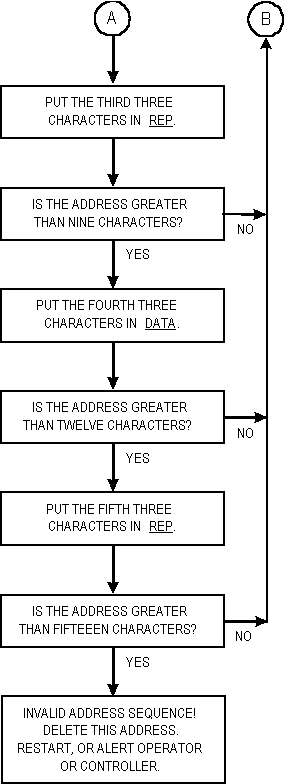
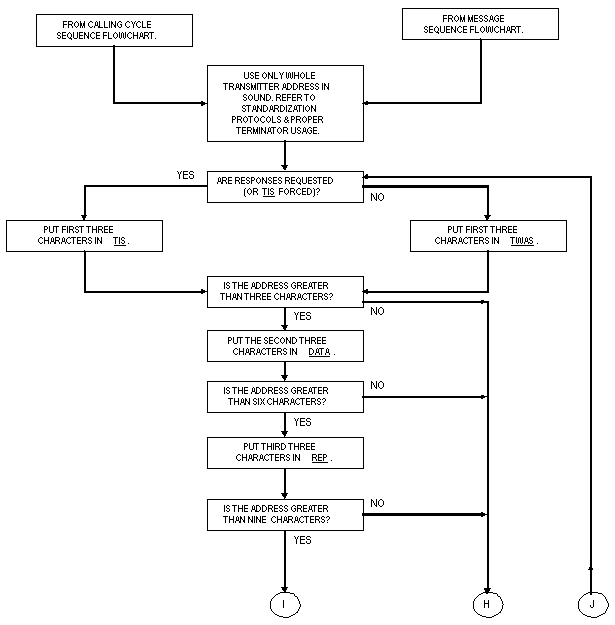
The third section of all frames is termed a "conclusion."
It shall be composed of either TIS or TWAS (but
not both) (and possibly DATA and REP) words, from
the end of the message (or calling cycle sections, if no message)
until the end of the call. See figure A-17. Sounds and exception
shall start immediately with TIS (or TWAS) words
as described in A.5.3. REP shall not immediately follow
TIS or TWAS. Both conclusions and sounds contain
the whole address of the transmitting station.
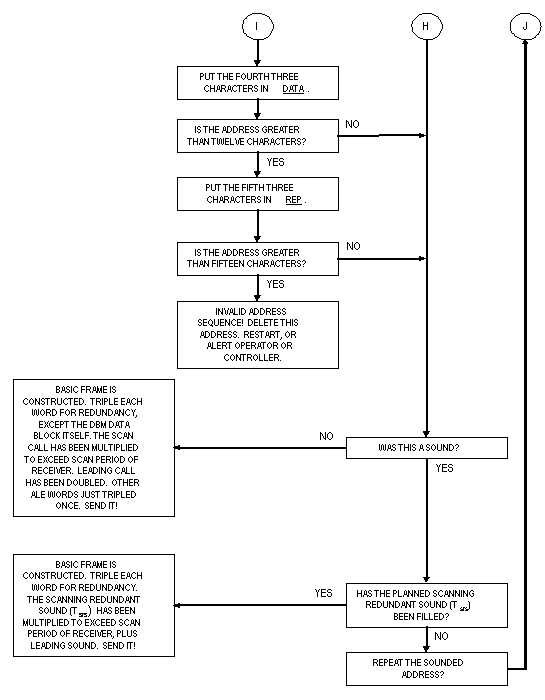
The eight ALE words types that have been described shall be used
to construct frames and messages only as permitted in figures
A-18, A-19, and A-20. The size and duration of ALE frames, and
their parts, shall be limited as described in table A-XII.
| Calls | Limit |
| Address size (5 words) (Ta max)
Call time maximum Tc
(one-half of Tlc = 12 words max)
Scan period (Ts max)
Message section basic time (Tm max basic) (unless modified by AMD extension, or by CMD such as DTM or DBM)
Message section, time limit of AMD (90 characters) (Tm max AMD) Message section time, DTM (1053
characters) (Tm max DTM) Message section time, DBM (37377 characters) (Tm max DBM) | 1960 ms
4704 ms
50 s
11.76 s
11.76 s 2.29 min
(entire data block) 23.26 min (entire deeply interleaved block) |
Contained in figure A-21 are basic examples (does not include
the optional message section) of frame construction. Included
are single-word and multiple-word examples of either single or
multiple called station address(es) for non-scan (single-channel)
and scanning (multiple-channel) use in individual, net, or group
calls.
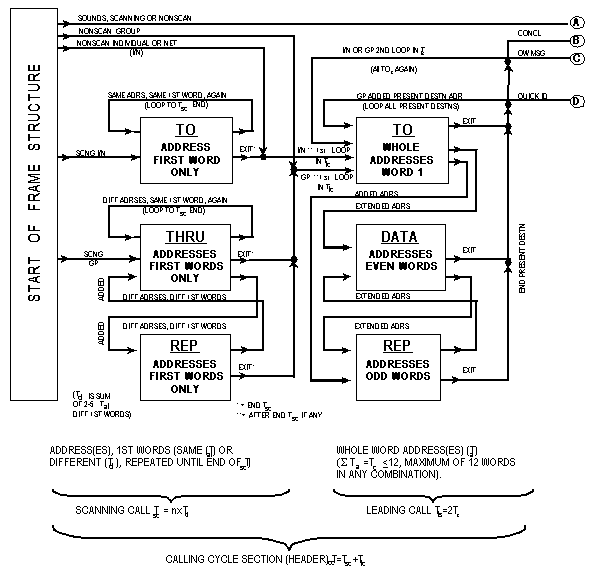
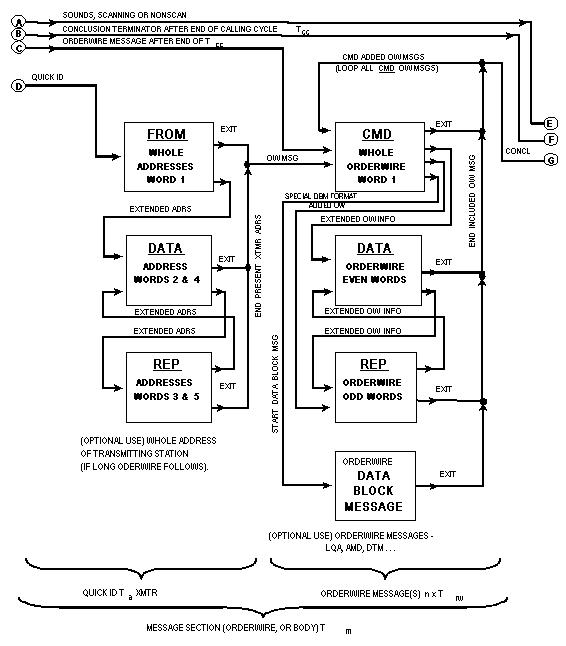
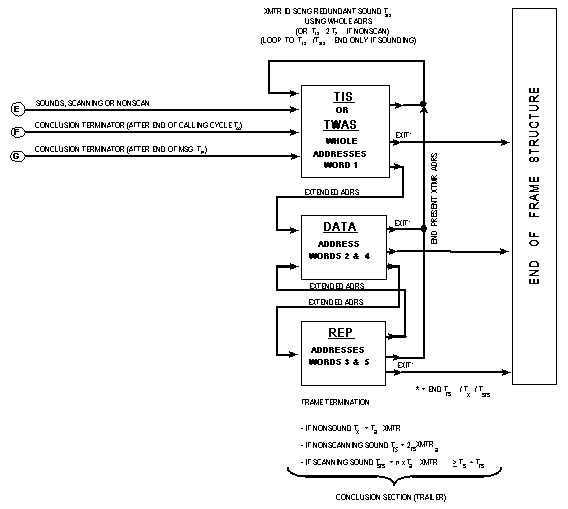
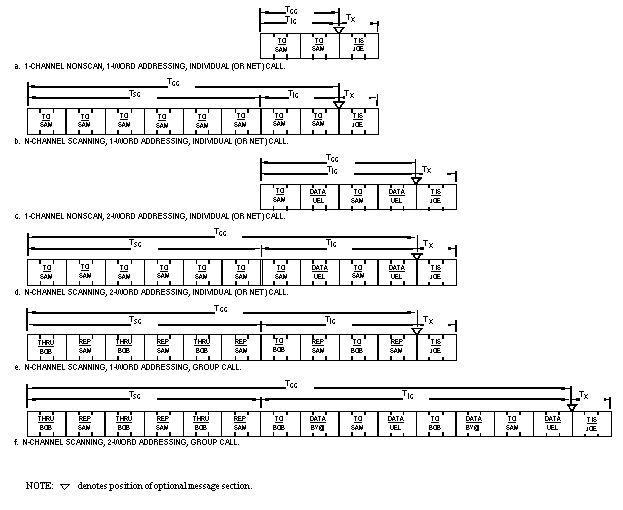
The ALE system is inherently asynchronous and does not require
any form of system synchronization, although it is compatible
with such techniques. Within a frame, the imbedded timing and
structure of the system provide the necessary "hooks"
for achieving and maintaining word synchronization (word sync)
during linking, orderwire, and anti-interference functions, as
described herein.
The ALE transmit modulator accepts digital data from the encoder
and provides modulated baseband audio to the transmitter. The
signal modulation is strictly timed as described in A.5.1.3 and
A.5.1.4. After the start of the first transmission by a station,
the ALE transmit modulator shall maintain a constant phase relationship,
within the specified timing accuracy, among all transmitted triple
redundant words at all times until the final frame in the transmission
is terminated. Specifically,
where T( ) is the event time of a given triple redundant
word within any frame, Trw is the period of three words
(392 ms), and n is any integer.
NOTE: Word phase tracking will only be implemented within a transmission
and not between transmissions.
The internal word phase reference of the transmit modulator shall
be independent of the receiver (which tracks incoming signals)
and shall be self timed (within its required accuracy). See A.5.1.4.
NOTE: In some applications, a single transmission may contain
several frames.
The receive demodulator accepts baseband audio from the receiver;
acquires, tracks, and demodulates ALE signals; and provides the
recovered digital data to the decoders. See figure
A-11. In data block message (DBM) mode, the receive demodulator
shall also be capable of reading single data bits for deep deinterleaving
and decoding.
The decoder accepts digital data from the receive demodulator and performs deinterleaving, decoding, FEC, and data checking. During initial and continuing synchronization, all of the following criteria should be used to discriminate and read every ALE word:
The number of unanimous votes provides an easily adjustable BER
signal quality discrimination, and the threshold should be chosen
by the manufacturer to optimize performance. A successful Golay
decode indicates that all detected bit errors were corrected within
the power of the FEC code; that is, the errors were within correctable
limits and therefore, the uncorrectable error flag(s) did not
occur. The correction power (mode) of the Golay code should be
chosen by the manufacturer to optimize performance using any of
the four modes: (3/4, 2/5, 1/6, 0/7) where n/m indicates up to
"n" errors detected and corrected, or up to "m"
errors detected but not correctable. Acceptable preambles, as
described here and defined in A.5.2.3.1.3, refer to those preambles
which are within the limits of this standard. As a DO, automatic
adjustment of the unanimous vote threshold and Golay mode should
be provided to optimize performance under varying conditions.
NOTE: The application of each preamble is dependent on the recent
signaling history of the stations heard, the active status of
the machine, the handshake(s) expected, and the protocol being
used, if any. For example, an uncommitted station, awaiting calls,
would accept TO if individual or net call (and possibly
THRU or REP if group call) as valid preambles for
calls to it. It would reject CMD as being irrelevant (because
it missed the preceding and required calling cycle Tcc).
It might also reject TIS or TWAS (unless collecting
sounding information). Acceptable characters means that each
character is within the appropriate ASCII subset. Note that all
criteria, together, must be satisfied to accept a word. For example,
all three characters would have to be within the Basic 38 subset
if a routing preamble such as a TO was decoded. Likewise,
any bit combination would be conditionally acceptable if an initial
REP was received, but in most cases, without the necessary
knowledge of the previous word, it would be considered irrelevant
and should be rejected.
The structure of the sound is virtually identical to that of the
basic call; however, the calling cycle is not needed and there
is no message section. It is only necessary to send the conclusion
(terminator) that identifies the transmitting station. See figure
A-22. The type of word, either TIS or TWAS (but
never both), indicates whether potential callers are encouraged
or ignored, respectively. The minimum redundant sound time (Trs)
is equal to the standard one-word address leading call time (Tlc)=784
ms. Described below are both single-channel and multiple-channel
protocols, plus detailed timing and control information, for designing
stations.
The fundamental capability to automatically sound on a channel
shall be in accordance with the sounding protocol as shown in
figure A22. As an option, stations may employ this protocol
for single-channel sounding, connectivity tracking, and the broadcast
of their availability for calls and traffic. The basic protocol
consists of only one part: the sound. The sound contains its
own address ("TIS A"). If "A" is encouraging
calls and receives one, "A" shall follow the sound with
the optional handshake protocol described in A.5.3.4. If "A"
plans to ignore calls, it shall use the TWAS, which advises
"B" and the others not to attempt calls, and then "A"
shall immediately return to normal "available." In
some systems it is necessary for a multichannel station "A"
to periodically sound to a single-channel network, usually to
inform them that he is active and available on that channel, although
scanning. Upon receipt of "A's" sound, "B"
(see figure A-23) and the other stations shall display "A's"
address as a received sound and, if they have an LQA and connectivity
memory, they shall store the connectivity information.
Sounding must be compatible with the scanning timing. All stations
shall be capable of performing the scanning sounding protocols
described herein, even if operating on a fixed frequency. See
figures A-22, A-23, and A-24. These protocols establish and positively
confirm unilateral connectivity between stations on any available
mutually scanned channel, and they assist in establishment of
links between stations waiting for contact. Stations shall employ
these protocols for multichannel sounding, connectivity tracking,
and the broadcast of their availability for calls and traffic.
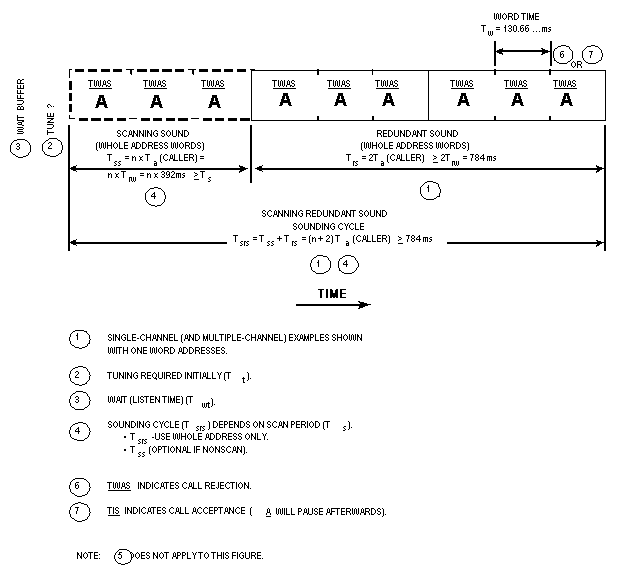
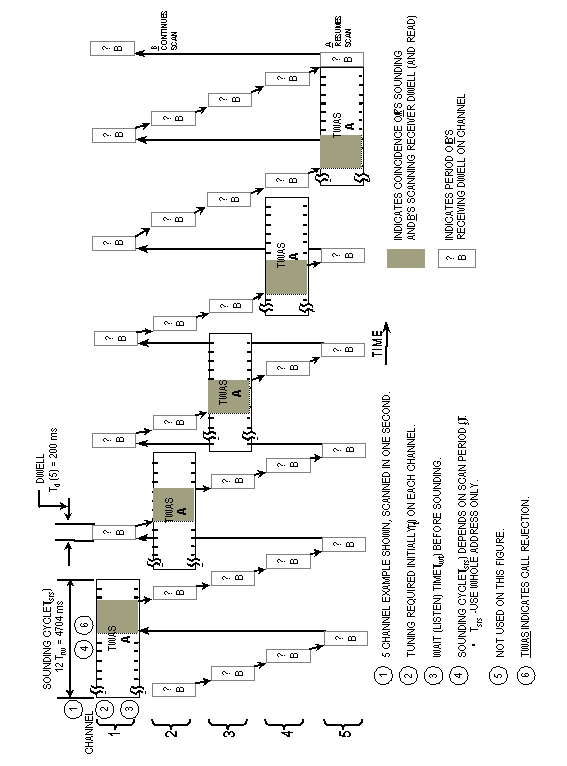
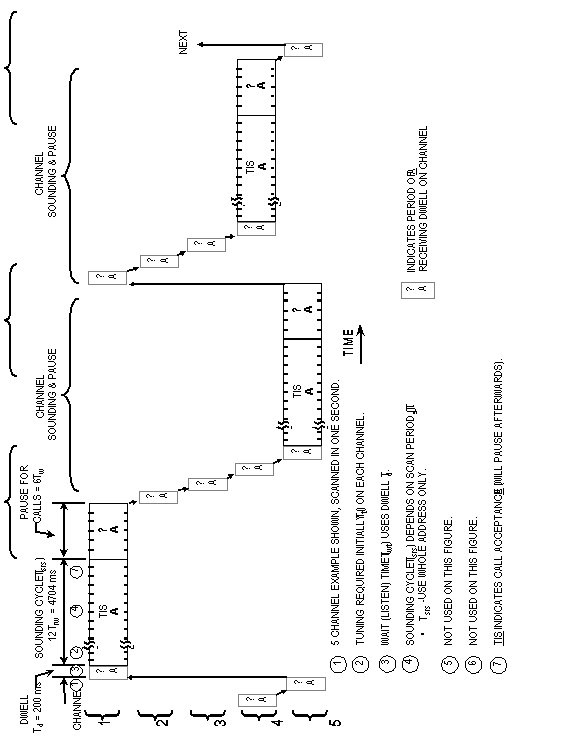
All timing considerations and computations for individual scanning
calling shall apply to scanning sounding, including sounding cycle
times and (optional) handshake times.
NOTE: The scanning sound is identical to the single-channel sound
except for the extension of the redundant sound time (Trs)
by adding words to the scan sounding time (Tss) to
form a scanning redundant sound time (Tsrs); that is
Tsrs = Tss + Trs. The scan sounding
time (Tss) is identical in purpose to the scan calling
time (Tsc) for an equivalent scanning situation, but
it only uses the whole address of the transmitter.
The channel-scanning sequences and selection criteria for individual
scanning calling shall also apply to scanning sounding. The channels
to be sounded are termed a "sound set," and usually
are identical to the "scan set" used for scanning.
See figure A-23. In this illustration, station "A"
is sounding and station "B" is scanning normally. If
a station "A" plans to ignore calls (from "B"),
which may follow "A's" sound, the following call rejection
scanning sounding protocol shall be used. In a manner identical
to the previously described individual scanning call, "A"
lands on the first channel in the scan set (1), waits (Twt)
to see if the channel is clear (3), tunes (Tt) its
coupler, comes to full power, and initiates the frame of the scanning
redundant sound times (Tsrs). This scanning sound
is computed to exceed "B's" (and any others) scan period
(Ts) by at least a redundant sound time (Trs),
which will ensure an available detection period exceeding Tdrw
= 784 ms. In this five-channel example, with "B" scanning
at 5 chps, "A" sounds for at least 12 Trw
(4704 ms). "A" also uses "TWAS A,"
redundantly to indicate that calls are not invited. Upon completion
of the scanning sounding frame transmission, "A" immediately
leaves the channel and goes to the next channel in the sound set.
This procedure repeats until all channels have been sounded,
or skipped if occupied. When the calling ALE station has exhausted
all the prearranged sound set channels, it shall automatically
return to the normal "available" receive scan mode.
As shown in figure A-23, the timing of both "A" and
"B" have been prearranged to ensure that "B"
has at least one opportunity, on each channel, to arrive and "capture"
"A's" sound. Specifically, "B" arrives, detects
sounds, waits for good words, reads at least three (redundant)
"TWAS A" (in 3 to 4 Tw), stores the
connectivity information (if capable), and departs immediately
to resume scan.
There are several specific protocol differences when station "A"
plans to welcome calls after the sound. See figure A-24. In
this illustration, "A" is sounding and "B"
is scanning normally. If station "A" plans to welcome
calls (from "B"), which may follow his sound, the following
call acceptance scanning sounding protocol shall be used. In
this protocol, "A" sounds for the same time period as
before. However, since "A" is receptive to calls, he
shall use his normal scanning dwell time (Td) or his
preset wait before transmit time (Twt), whichever is
longer, to listen for both channel activity and calls before sounding.
If the channel is clear, "A" shall initiate the scanning
sound identically to before, but with "TIS A."
At the end of the sounding frame, "A" shall wait for
calls identically to the wait for reply and tune time (Twrt)
in the individual scanning calling protocol, in this case shown
to be 6 Tw (for fast-tuning stations). During this
wait, "A" shall (as always) be listening for calls that
may coincidentally arrive even though unassociated with "A's"
sound, plus any other sound heard, which "A" shall store
as connectivity information if polling-capable. If no calls are
received, "A" shall leave the channel.
In the previous descriptions, one alternative action is the implementation
of an optional handshake with a station immediately after its
sound. This protocol is identical in all regards to the single
channel individual call protocol, except that it is manually or
automatically (operator or controller) triggered by acquisition
of connectivity from the station that is to be called. See figure
A-25. In this illustration, "A" is scanning sounding
and is receptive to calls, and "B" is receive scanning
(or waiting in ambush on a channel) and requires contact with
"A" if heard. "A" uses the standard call
acceptance scanning sound, including the "TIS A"
and the pause for calls. In this case "B" calls "A."
When ALE stations are scanning sounding and receptive to calls,
or required contact with such a station, the optional handshake
protocol should be used. The calling station should immediately
initiate the call upon the determination that the station to be
called has terminated its transmission. A wait time before transmit
time is not required. Therefore, if "B" hears "A's"
sound and is seeking "A," "B" calls immediately
using the simple single-channel call. Also, if "B's"
operator or controller identifies "A's" address it can
attempt the optional handshake.
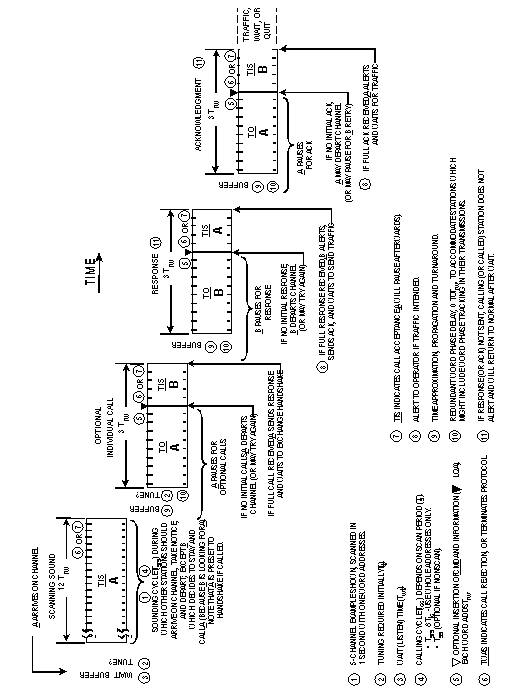
Channel selection is based on the information stored within the
LQA memory (such as BER, SINAD, and MP) and this information is
used to speed connectivity and to optimize the choice of quality
channels. When initiating scanning (multichannel) calling attempts,
the sequence of channels to be tried shall be derived from information
in the LQA memory with the channel(s) with the "best score(s)"
being tried first (unless otherwise directed by the operator or
controller) until all the LQA scored channels are tried. However,
if LQA or other such information is unavailable (or it has been
exhausted and other valid channels remain available and untried)
the station shall continue calling on those channels until successful
or until all the remaining (untried valid) channels have been
tried.
LQA data shall be used to score the channels and to support selection
of a "best" (or an acceptable) channel for calling and
communication. LQA shall also be used for continual monitoring
of the link(s) quality during communications that use ALE signaling.
The stored values shall be available to be transmitted upon request,
or as the network manager shall direct. Unless specifically and
otherwise directed by the operator or controller, all ALE stations
shall automatically insert the CMD LQA word (t) in the
message section of their signals and handshakes when requested
by the handshaking station(s), when prearranged in a network,
or when specified by the protocol. See A.5.4.2. If an ALE station
requires, and is capable of using LQA information (polling-capable),
it may request the data from another station by setting the control
bit KA1 to "1" in the CMD LQA word. If an ALE
station, which is sending CMD LQA in response to a request
is incapable of using such information itself (not polling-capable),
it shall set the control bit KA1 to "0." It will be
a network management decision to determine if the LQA is to be
active or passive. For human factor considerations, LQA scores
that may be presented to the operator should have higher (number)
scores for better channels.
Analysis of the BER on rf channels, with respect to poor channels
and the 8-ary modulation, plus the design and use of both redundancy
and Golay FEC, shows that a coarse estimate of BER may be obtained
by counting the number of non-unanimous (2/3) votes (out of 48)
in the majority vote decoder. The range of this measure is 0
through 48. Correspondence to actual BER values is shown in table
A-XIII.
After an ALE receiver achieves word synchronization (see A.5.2.6.2), all received words in a frame shall be measured, and a linear average BER/LQA shall be computed as follows:
At the end of the transmission, the total shall be divided by
the number of words received, and the total shall be stored in
the Link Quality Memory as the most current BER code for the station
sending the measured transmission and the channel that carried
it.
The signal to noise and distortion measurement shall be a SINAD
measurement ((S+N+D)/(N+D)) averaged over the duration of each
received ALE signal. The SINAD values shall be measured on all
ALE signals.
Measurement of MP using received ALE signals is optional.
Display of SINAD values shall be in dB.
This mandatory function is designed to support the exchange of
current LQA information among ALE stations. The CMD LQA
word shall be constructed as shown in table A-XIV The preamble
shall be CMD (110) in bits P3 through P1 (W1 through W3).
The first character shall be "a" (1100001) in bits
C1-7 through C1-1 (W4 through W10), which shall identify the LQA
function "analysis." It carries three types of analysis
information (BER, SINAD, and MP) which are separately generated
by the ALE analysis capability. Note that when the control bit
KA1 (W11) is set to "1," the receiving station shall
respond with an LQA report in the handshake. If KA1 is set to
"0," the report is not required.
Measurement and reporting of BER is mandatory. The BER field
in the LQA CMD shall contain five bits of information,
BE5 through BE1 (W20 through W24). Refer to table A-XIII for
the assigned values.
SINAD shall be reported in the CMD LQA word as follows.
The SINAD is represented as five bits of information SN5 through
SN1 (W15 through W19). The range is 0 to 30 dB in 1-dB steps.
00000 is 0 dB or less, and 11111 is no measurement.
If implemented, MP measurements shall be reported in CMD LQA words in the three bits, MP3 through MP1 (W12 through W14). The measured value in ms shall be reported rounded to the nearest integer, except that values greater than 6 ms shall be reported as 6 (110). When MP is not measured, the reported MP value shall be 7 (111).
Average 2/3 Votes Counted | LQA Transmission Bits MSB LSB | Approximate BER | ||||
| BE5 | BE4 | BE3 | BE2 | BE1 | ||
| 0 | 0 | 0 | 0 | 0 | 0 | 0.0 |
| 1 | 0 | 0 | 0 | 0 | 1 | 0.006993 |
| 2 | 0 | 0 | 0 | 1 | 0 | 0.01409 |
| 3 | 0 | 0 | 0 | 1 | 1 | 0.02129 |
| 4 | 0 | 0 | 1 | 0 | 0 | 0.02860 |
| 5 | 0 | 0 | 1 | 0 | 1 | 0.03602 |
| 6 | 0 | 0 | 1 | 1 | 0 | 0.04356 |
| 7 | 0 | 0 | 1 | 1 | 1 | 0.05124 |
| 8 | 0 | 1 | 0 | 0 | 0 | 0.05904 |
| 9 | 0 | 1 | 0 | 0 | 1 | 0.06699 |
| 10 | 0 | 1 | 0 | 1 | 0 | 0.07508 |
| 11 | 0 | 1 | 0 | 1 | 1 | 0.08333 |
| 12 | 0 | 1 | 1 | 0 | 0 | 0.09175 |
| 13 | 0 | 1 | 1 | 0 | 1 | 0.1003 |
| 14 | 0 | 1 | 1 | 1 | 0 | 0.1091 |
| 15 | 0 | 1 | 1 | 1 | 1 | 0.1181 |
| 16 | 1 | 0 | 0 | 0 | 0 | 0.1273 |
| 17 | 1 | 0 | 0 | 0 | 1 | 0.1368 |
| 18 | 1 | 0 | 0 | 1 | 0 | 0.1464 |
| 19 | 1 | 0 | 0 | 1 | 1 | 0.1564 |
| 20 | 1 | 0 | 1 | 0 | 0 | 0.1667 |
| 21 | 1 | 0 | 1 | 0 | 1 | 0.1773 |
| 22 | 1 | 0 | 1 | 1 | 0 | 0.1882 |
| 23 | 1 | 0 | 1 | 1 | 1 | 0.1995 |
| 24 | 1 | 1 | 0 | 0 | 0 | 0.2113 |
| 25 | 1 | 1 | 0 | 0 | 1 | 0.2236 |
| 26 | 1 | 1 | 0 | 1 | 0 | 0.2365 |
| 27 | 1 | 1 | 0 | 1 | 1 | 0.2500 |
| 28 | 1 | 1 | 1 | 0 | 0 | 0.2643 |
| 29 | 1 | 1 | 1 | 0 | 1 | 0.2795 |
| 30 (or more) | 1 | 1 | 1 | 1 | 0 | 0.3 (or more) |
| - - | 1 | 1 | 1 | 1 | 1 | no value available |
| LQA Bits | Word Bits | |||
| CMD
Preamble | MSB | P3=1
P2=1 P1=0 | MSB | W1
W2 W3 |
| First
Character "a" | MSB LSB | C1-7=1
C1-6=1 C1-5=0 C1-4=0 C1-3=0 C1-2=0 C1-1=1 | W4
W5 W6 W7 W8 W9 W10 | |
| Control | KA1 | W11 | ||
| MP
Bits | MSB LSB | MP3
MP2 MP1 | W12
W13 W14 | |
| SINAD
Bits | MSB LSB | SN5
SN4 SN3 SN2 SN1 | W15
W16 W17 W18 W19 | |
| BER
Bits | MSB LSB | BE5
BE4 BE3 BE2 BE1 | LSB | W20
W21 W22 W23 W24 |
NOTES:
| ||||
See MIL-STD-187-721.
The Local Noise Report CMD provides a broadcast alternative
to sounding that permits receiving stations to approximately predict
the bilateral link quality for the channel carrying the report.
An example application of this optional technique is networks
in which most stations are silent but need to have a high probability
of linking on the first attempt with a base station. A station
receiving a Local Noise Report can compare the noise level at
the transmitter to its own local noise level, and thereby estimate
the bilateral link quality from its own LQA measurement of the
received noise report transmission. The CMD reports the
mean and maximum noise power measured on the channel in the past
60 minutes.
The Local Noise Report CMD shall be formatted as shown
in figure A-26. Units for the Max and Mean fields are dB relative
to 0.1 µV 3 KHz noise. If the local noise measurement to
be reported is 0 dB or less, a 0 is sent. For measured noise
ratios of 0 dB to +126 dB, the ratio in dB is rounded to an integer
and sent. For noise ratios greater than +126 dB, 126 is sent.
The code 127 (all 1s) is sent when no report is available for
a field. By comparing the noise levels reported by a distant
station on several channels, the station receiving the noise reports
can select a channel for linking attempts based upon knowledge
of both the propagation characteristics and the interference situation
at that destination.
| Noise Report (ASCII 'n') | Max | Mean | |
| 1101110 |
All stations shall be capable of selecting the (recent) best channel
for calling or listening for a single station based on
the values in the LQA memory.
When selecting a channel for a two-way link, link quality measurements
for both directions on each frequency must be considered. Figure
A-27 represents a simple LQA memory example. For each address/channel
cell, the measured LQA (upper section) and reported LQA values
(lower section) are stored. Bilateral (handshake) scores in this
example are the sum of the two LQA values.
NOTE 1: For operator viewing, LQA values for better channels
should be displayed as higher numbers, and values for poorer channels
should be displayed as lower numbers.
NOTE 2: In the example shown in figure A-27, if a handshake is
required with station "B," channel C3 would be the best
because the "round trip" (bilateral) score would be
5 (1+4), thus the lowest, channel C4 is next best with a score
of 6 (3+3), the C5 with 7, C2 with 12, and C6 with 18. Linking
attempts should be made in that order (C3, C4, C5, C2, and C6).
C1 is left until last because of the "x", which indicates
that a recent attempted handshake on that channel failed to link.
Similarly, an attempt to call "A" would yield the sequence
C3(3), C5(12), C2(12), C1(24), C6(26), and C4(x). In this case,
C5 was equal to C2 (both are 12), but C5 was chosen first because
the paths were more balanced (LQA values were more equal).
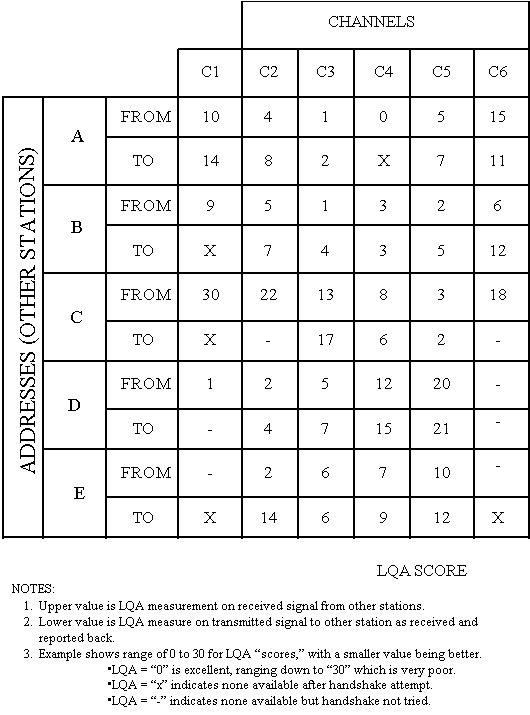
If only a one-way transmission to a station is required instead
of a handshake, the scores reported by the destination station
(TO section in figure A-27) should be given greater weight than
the scores measured on transmissions from that station.
NOTE: In the example, to reach "B," the sequence would
be C4(3), C3(4), C5(5), C2(7), C6(12), and C1(x) as a last resort.
When selecting a channel to listen for another station, the scores
measured on transmissions from that station (FROM section in figure
A-27) should be given greater weight than the scores reported
by the destination station.
NOTE: In the example, to listen for "A," channel C4(0)
would be best, and if only three channels were to be scanned,
they should be C4, C3, and C2.
A station shall also be capable of selecting the (recent) best
channel to call or listen for multiple stations, based on the
values in the LQA memory.
NOTE: In the example shown in figure A-27, if a multiple-station
handshake is required with stations "B" and "C,"
C5 is the best choice as the total score is 12 (2+5+3+2), followed
by C4 (20) and C3 (35). Next would be C2 (34+) and C6 (36+),
this ranking being due to their unknown handshake capability (which
had not been tried). C1(x) is the last to be tried because recent
handshake attempts had failed for both "B" and "C."
To call the three stations "A," "B," and
"C," the sequence would be C5 (24), C3 (38), C2 (46+),
C6 (62+), C4 (one x) (recently failed attempt), and finally C1
(two x).
If an additional selection factor is used, it will change the
channel selection sequence.
NOTE: In the example, to call "D" and "E,"
the sequence would be C2, C3, C4, C5, C1, and C6. If a maximum
limit of LQA < 14 is imposed on any path (to achieve
a minimum circuit quality), only C2 and C3 would be initially
selected for the linking attempt. Further, if the LQA limit was
"lowered" to 10, C3 would be selected before C2 for
the linking attempt.
If a broadcast to multiple stations is required, the TO section
("to" the station) scores are given priority.
NOTE: In the example, to broadcast to "B" and "C,"
the sequence would be C5(7), C4(9), C3(21), C2(7+), C6(12+), and
C1(two x).
To select channels for listening for multiple stations, the FROM
section ("from" the station) scores are given priority.
NOTE: In the example, to listen for "A" and "B,"
channel C2 (2) would be best, and if only four channels could
be scanned, they should be C2, C3, C4, and C5.
Before initiating a call or a sound on a channel, an ALE controller
shall listen for a programmable time (Twt) for other
traffic, and shall not transmit on that channel if traffic is
detected. Normally, a sound aborted due to detected traffic will
be rescheduled, while for a call another channel shall be selected.
The duration of the listen-before-transmit pause shall be programmable
by the network manager. When the selected channel is known to
be used only for ALE transmissions, the listen-before-transmit
delay need be no longer than 2 Trw. For other channels,
at least 2 seconds shall be used. When an ALE controller was
already listening on the channel selected for a transmission,
the time spent listening on the channel may be included in the
listen-before-transmit time.
The listen-before-transmit function shall detect traffic on a
channel in accordance with A.4.2.2. This may be accomplished
using any combination of internal signal detection and external
devices that provide a channel busy signal to the ALE controller.
The operator shall be able to override both the listen-before-transmit
pause and the transmit lockout (for emergency use).
An ALE controller shall control an attached HF SSB radio to support
both manual and automatic link operation as described in the following
paragraphs.
The ALE controller shall support emergency control by the operator.
Each ALE controller shall provide a manual control capability
to permit an operator to directly operate the basic SSB radio
in emergency situations. At all other times, the radio shall
be under automated control, and the operator should operate the
radio through its associated controller. The ALE controller's
receiving and passive collection capability to be "always
listening," such as monitoring for sounding signals or alerting
the operator, shall not be impaired.
NOTE: This does not abrogate the manual push-to-talk operation
required by 4.2.2.
The fundamental protocol exchange for link establishment shall
be the three-way handshake (see Appendix I for overview of Selective
Calling). A three-way handshake is sufficient to establish a
link between a calling station and a responding station. With
the addition of slotted responses (described in A.5.5.4.2), the
same call/response/acknowledgment sequence can also link a single
calling station to multiple responding stations.
An ALE controller may be referred to as being in one of three
conceptual "states." See figure
A-28.
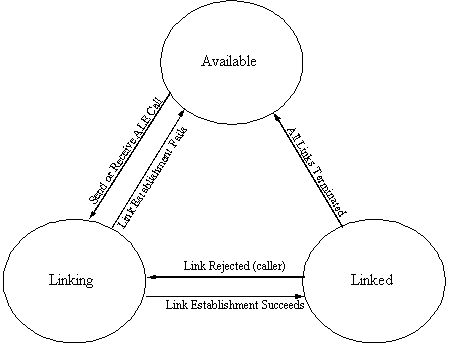
A scanning calling station shall send ALE calls on its scanned
channels in the order dictated by its channel selection algorithm.
It shall link on the first channel it tries that supports a handshake
with the called station(s).
If a channel is rejected after linking by the operator or controller
as unsuitable, the ALE controller shall terminate the link in
accordance with A.5.5.3.5 and shall update LQA data using measurements
obtained during linking.
During the scanning-calling cycle, a caller may encounter occupied
channels and shall skip them to avoid interference to traffic
and activity. After all available channels have been tried, if
no contact has been successful, the caller should revisit the
previously occupied channels and, if they are free, attempt to
call.
If a calling station has exhausted all of its prearranged scan
set channels and failed to establish a link, it shall immediately
return to normal receive scanning (the available state). It shall
also alert the operator (and networking controller if present)
that the calling attempt was unsuccessful.
ALE controllers shall identify the end of a received ALE signal by the following methods. The controller shall search for a valid conclusion (TIS or TWAS, possibly followed by DATA and REP for a maximum of five words, or Tx max). The conclusion must maintain constant redundant word phase within itself (if a sound) and with associated previous words. The controller shall examine each successive redundant word phase (Trw) following the TIS (or TWAS) for the first (of up to four) non-readable or invalid word(s). Failure to detect a proper word (or detection of an improper word) or detection of the last REP, plus the last word wait delay time, (Tlww or Trw), shall indicate the end of the received transmission. The maximal acceptable terminator sequence is TIS (or TWAS), DATA, REP, DATA, REP.
| NOTE: Refer to annex A and annex B for details. |
| Basic system timing |
|
|
|
|
|
|
Ta = 392 ms to 1960 ms |
|
| System timing limits |
|
|
|
|
|
|
|
|
|
|
| If an ALE (orderwire) protocol such as AMD, DTM, or DBM is used to extend the basic message section, it shall start no later than the start of the 30th word (11.368 s). Such extension of the message section shall be determined by the length of the extended ALE protocol, and the message section shall terminate at the end of the orderwire without additional extension. The conclusion shall start at the end of the message section. |
| Individual calling |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Trw = 1176 ms |
| Sounding |
|
|
|
| Star calling |
|
|
|
|
m=SN-1 S Ta(m) (called)] m=1 |
|
|
|
|
|
|
| Programmable timing parameters: typical values |
|
|
|
|
The protocol for establishing a link between two individual stations
shall consist of three ALE frames: a call, a response, and an
acknowledgment. The sequence of events, and the timeouts involved,
are discussed in the following paragraphs using a calling station
SAM and a called station JOE.
After selecting a channel for calling, the calling station (SAM)
shall begin the protocol by first listening on the channel to
avoid "disturbing active channels," and then tuning.
If the called station (JOE) is known to be listening on
the chosen channel (not scanning), the calling station shall transmit
a single-channel call that contains only a leading call and a
conclusion (see upper frame in figure A-29). Otherwise, it shall
send a longer calling cycle that precedes the leading call with
a scanning call of sufficient length to capture the called station's
receiver as it scans (lower frame in figure A-29). The duration
of this scanning call shall be 2 Trw for each channel
that the called station is scanning. The scanning call section
shall contain only the first word of the called station address,
using a TO preamble, and repeated as necessary until the
end of the scanning call section.
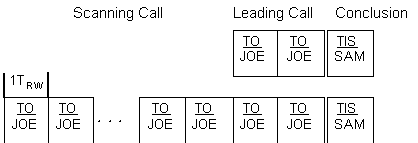
The entire called station address shall be used in the leading
call section, and shall be sent twice (see figure A-29) using
a TO preamble each time the first word is sent and DATA
and REP as required for additional words.
Any message section CMDs shall be sent immediately following
the leading call, followed by a conclusion containing the complete
calling station address ("TIS SAM").
The calling station shall then wait a preset reply time to start
to receive the called station's response. In the single-channel
case, the wait for reply time shall be Twr, which includes
anticipated round trip propagation delay and the called station's
turnaround time. In the multi-channel case, the calling station
shall wait through a wait for reply and tune time (Twrt),
which also includes time for the called station to tune up on
the chosen channel.
If the expected reply from the called station does not start to
arrive within the preset wait for reply time (Twr)
or wait for reply and tune time (Twrt), the linking
attempt on this channel has failed. At this point, if other channels
in the scan set have not been tried, the linking attempt will
normally start over on a new channel. Otherwise, the ALE controller
shall return to the available state, and the calling station's
operator or networking controller shall be notified of the failed
linking attempt.
When the called station (JOE) arrives on channel, sometime
during its scan period Ts, and therefore during the
calling station SAM's longer scan calling time Tsc,
the called station shall attempt to detect ALE signaling within
its dwell time. If ALE signaling is detected, and the controller
achieves word sync, it shall examine the received word to determine
the appropriate action.
If JOE reads "TO JOE" (or an acceptable equivalent according to protocols), the ALE controller shall stop scan, enter the linking state, and continue to read ALE words while waiting a preset, limited time Twce for the calling cycle to end and the message or conclusion to begin.
While reading a call in the linking state, the called station shall evaluate each new received word. The controller shall immediately abort the handshake and return to its previous state upon the occurrence of any of the following:
If a quick-ID or a message section starts within Twce,
the called station, (JOE) shall attempt to read one or
more complete messages within a new preset, limited time Tmmax
If a frame conclusion starts "TIS SAM,"
the called station shall wait and attempt to read the calling
station's address (SAM) within a new preset, limited time
Txmax.
If an acceptable conclusion sequence with TIS is read,
the called station shall start a "last word wait" timeout
Tlww = Trw while searching for additional
address words (if any) and the end of the frame (absence of a
detected word), which shall trigger its response. The called
station will also expect the calling station to continue the handshake
(with an acknowledgment) within the called station's reply window,
Twr, after its response. If TWAS is read instead,
the called station shall not respond but shall return to its previous
state immediately after reading the entire calling station address.
If all of the above criteria for responding are satisfied, the
called station shall initiate an ALE response immediately after
detecting the end of the call, unless otherwise directed by the
operator or controller.
Upon receipt of a call that is addressed to one of its own self
addresses (JOE), and which contains a valid calling station
address in a TIS conclusion (SAM), the called station
shall listen for other traffic on the channel. If the channel
is not in use, the station shall tune up, send a response (figure
A-30), and start its own reply timer Twr. (The longer
Twrt timeout is not necessary unless the calling station
will send its acknowledgment on a different channel than the one
carrying the call, requiring re-tuning.) If the channel is in
use, the ALE controller shall ignore the call and return to its
previous state unless otherwise programmed.

If the calling station (SAM) successfully reads the beginning of an appropriate response ("TO SAM") starting within its timeout (either Twr or Twrt), it shall process the rest of the frame in accordance with the checks and timeouts described above for the call until it either aborts the handshake or receives the appropriate conclusion, which in this example is "TIS JOE."
Specifically, the calling station shall immediately abort the handshake upon the occurrence of any of the following:
After aborting a handshake for any of the above reasons, the calling
station will normally restart the calling protocol, usually on
another channel.
If the calling station receives the proper conclusion from the
called station ("TIS JOE") starting within
Tlc (plus Tm max, if message
included), it shall set a last word wait timeout as above and
prepare to send an acknowledgment. If, instead, "TWAS
JOE" is received, the called station has rejected
the linking attempt, the calling station ALE controller shall
abort the linking attempt and inform the operator of the rejected
attempt.
If all of the above criteria for an acceptable response are satisfied,
and if not otherwise directed by the operator or networking controller,
the calling station ALE controller shall alert its operator that
a correct response has been received, send an ALE acknowledgment
(see figure A-31), enter the linked state with the called station
(JOE), and unmute the speaker.
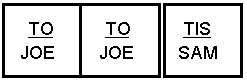
A "wait for activity" timer Twa shall be
started (with a typical timeout of 30 seconds) that shall cause
the link to be dropped if the link remains unused for extended
periods (see A.5.5.3.5).
If the called station (JOE) successfully reads the beginning of an appropriate acknowledgment ("TO JOE") starting within its Twr timeout, it shall process the rest of the frame in accordance with the checks and timeouts described above for the response until it either aborts the handshake or receives the appropriate conclusion, which in this example is "TIS SAM" or "TWAS SAM."
Specifically, the calling station shall immediately abort the handshake upon the occurrence of any of the following:
If the handshake is aborted for any of the above reasons, the
handshake has failed, and the called station ALE controller shall
return to its pre-linking state. The called station shall notify
the operator or controller of the failed linking attempt.
Otherwise, the called station shall enter the linked state with
the calling station ("SAM"), alert the operator
(and network controller if present), unmute the speaker, and set
a wait-for-activity timeout Twa.
NOTE 1: Although SAM's acknowledgment to JOE appears
identical to a single-channel individual call from SAM
to JOE, it does not cause JOE to provide another
response to the acknowledgment (resulting in an endless "ping-pong"
handshake) because SAM's acknowledgment arrives within
a narrow time window (Twr) after JOE's response,
and an acknowledge (ACK) from SAM is expected within this
window. If SAM's acknowledgment arrives late (after Twr),
however, then JOE must treat it as a new individual call
(and shall therefore send a new response, if SAM concludes
the frame with TIS).
NOTE 2: A typical one-to-one scanning call three-way handshake
takes between 9 and 14 seconds.
Termination of a link after a successful linking handshake shall
be accomplished by sending a frame concluded with TWAS
to any linked station(s) which is (are) to be terminated. For
example, "TO JOE, TO JOE, TWAS
SAM" (when sent by SAM) shall terminate the
link between stations SAM and JOE. JOE shall
immediately mute and return to the available state, unless it
still retains a link with any other stations on the channel.
Likewise, SAM shall also immediately mute and return to
the available state, unless it retains a link with any other stations
on the channel.
A means shall be provided for operators to manually reset a station,
which shall mute the speaker(s), return the ALE controller to
the available state, and send a link terminating (TWAS)
transmission, as specified above, to all linked stations, unless
this latter feature is overridden by the operator. (DO: provide
a manual disconnect feature that drops individual links while
leaving others in place.)
If no voice, data, or control traffic is sent or received by a
station within a preset time limit for activity (Twa),
the ALE controller shall automatically mute the speaker, terminate
the linked state with any linked stations, and return to the available
state. The wait for the activity timer is mandatory, but shall
also be capable of being disabled by the operator or network manager.
This timed reset is not required to cause a termination (TWAS)
transmission, as specified above. However, it is recommended
that a termination be sent to reset the other linked stations(s)
to immediately return them to the available state.
Termination during a handshake or protocol by the use of TWAS
(or a timer) should cause the receiving (or timed-out) station
to end the handshake or protocol, terminate the link with that
station, re-mute, and immediately return to the available state
unless it still retains a link with another station.
While receiving an ALE signal, it is possible for the continuity
of the received signal to be lost (due to such factors as interference
or fading) as indicated by failure to detect a good ALE word at
a Trw boundary. When one or both Golay words of a
received ALE word contain uncorrectable errors, the ALE controller
shall attempt to regain word sync, with a bias in favor of words
that arrive with the same word phase as the interrupted frame.
If word sync is reacquired but at a new word phase, this indicates
that a collision has occurred. The interrupted frame shall be
discarded, and the interrupting signal processed as a new ALE
frame.
NOTE: Stations should be able to read interfering ALE signals,
as they may contain useful (or critical) information, for which
the station is "always listening."
One station may simultaneously establish a multi-way link with
multiple other stations using the protocols described in the following
subparagraphs.
The simple three-way handshake used for individual links cannot
be used for one-to-many calling because the responses from the
called stations would collide with each other. Instead, a time-division
multiple access (TDMA) scheme is used. Each responding station
shall send its response in an assigned or computed time slot as
described later for the particular one-to-many protocol.
At the end of a one-to-many call frame, the following events shall take place:
As each station's slot wait timer expires, it shall send its response
and continue to await the expiration of its WRTT. Should that
timer expire before the start of an acknowledgment from the calling
station, the called station shall abort the linking attempt, and
return to its pre-linking state.
Slotted response frames shall be formatted identically to responses
in the one-to-one calling protocol (see figure A-32), including
a leading call, an optional message section, and a frame conclusion.
A responding station shall conclude its response with TIS
to accept the call, or TWAS to reject it. When the calling
and responding addresses are one-word (as shown), slots are each
14 Tw, or about 1.8 seconds.
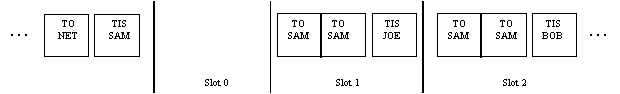
Unless otherwise specified, all slots shall be 14 Tw in duration, which allows response frames with single-word addresses to propagate to and from the other side of the globe and use commonly available HF transceivers and tuners. When any slot is extended, all following slots shall be delayed commensurately.
The general formula for determining the correct timing for slotted
responses in nonminimum or nonuniform cases is as follows for
a selected slot number denoted SN:
Tswt(SN) = SN x [5 Tw + 2 Ta (caller) + (optional message) Tm] + Ta (caller) +
m = SN-1
S Ta (m) (called)
m=1
Where Ta (caller) is the address length (an integer multiple of Trw) of the calling station,
(optional message)Tm is an optional message section
(same size for all slots), present if and only if requested in
the call. Ta(m) (called) is the address length of
the station that will respond in slot m. (Note that the length
of slot 0 is determined by using the address length of the calling
station.) The formula for the calling station wait for net reply
timeout (Twrn) is
where NS is the total number of slots; one is added to include
slot zero.
The formula for the called station acknowledgment timer is
The slotted response example is shown in figure
A-33.
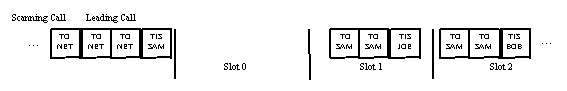
A net address is assigned to a set of net member stations, as
described in A.5.2.4.4. The slot number and address to be used
by each net member are preassigned and known to all net members.
A star net call is identical to a one-to-one call, except that
the called station address is a net address, as shown in figure
A-34. The calling station address shall be an individual station
address (not a net or other collective address).
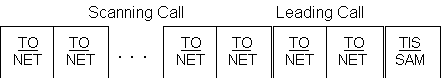
When an ALE controller receives a call that is addressed to a
net address that appears in its self address memory (see A.4.3.2),
it shall process the call using the same checks and timeouts as
an individual call (see A.5.5.3.2). If the call is acceptable,
it shall respond in accordance with A.5.5.4.1 using its assigned
net member address and slot number for the net address that was
called.
A star net acknowledgment is identical to a one-to-one acknowledgment,
except that the called station address is a net address.
An ALE controller that has responded to a net call shall process
the acknowledgment from the calling station in accordance with
A.5.5.3.4, except that the wait-for-response timeout value shall
be the Twan timeout from A.5.5.4.1.3. A TWAS
acknowledgment from the calling station shall return the called
ALE controller to its pre-linking state. If a TIS acknowledgment
is received from the calling station, the called ALE controller
shall enter the linked state with the calling station (SAM
in this example), alert the operator (and network controller if
present), unmute the speaker, and set a wait-for-activity timeout
Twa.
The group calling protocol extends the power of one-to-many calling to ad hoc collections of stations that have not been preprogrammed as a net. Nothing need be known about the stations except their individual addresses and scanned frequencies. Because a group is not set up in advance, stations must be able to derive group membership and slot parameters on the fly. Group membership is limited as follows:
A group address is produced by combining individual addresses
of the stations that are to form the group. During a scanning
call, only the first word(s) of addresses shall be sent, just
as for individual or net calls. The set of unique first address
words for the group members shall be sent repeatedly in rotation
until the end of Tsc. These address words shall alternate
between THRU and REP preambles (see figure A-35
for a sample group consisting of BOB, EDGAR, and
SAM).
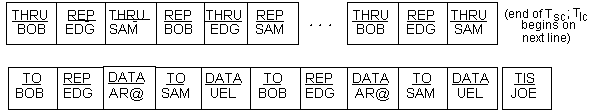
When group member addresses share a common first word, that word
shall be sent only once during Tsc. A limit of five
unique first words may be sent in rotation during Tsc.
During Tlc, the complete addresses of the prospective
group members shall be sent, using TO preambles as usual.
Up to 12 address words total are allowed for the full addresses
of group members, so Tlc in a group call may last up
to 24 Trw. Note in figure A-34 that when a TO
word would follow another TO word, a REP preamble
must be used, but when a TO follows any other word it shall
remain a TO.
The optional message section and the conclusion of a star group
call shall be in accordance with A.5.2.5.
Slots shall be derived for group call responses by noting the order in which individual addresses appear in the call.
a. When an ALE controller pauses on a channel carrying a group scanning call, it will read either a THRU or a REP preamble. If the address word in this first received word matches the first word of one of its individual addresses, the ALE controller shall stay to read the leading call. Otherwise, it shall continue to read first address words until it finds:
(In the latter two cases, the station is not being called and
the ALE controller shall return to the available or linked state
as appropriate.)
b. When Tlc starts, an ALE controller potentially addressed in the scanning call shall watch for its complete address. If found, a slot counter shall be set to 1 and incremented for each address that follows it. If that address is found again (as it should be, because the address list is repeated in Tlc), the counter shall be then reset to 1, and incremented for each following address as before. The number of words in each following address shall also be noted for use in computing Tswt.
c. The message section (if any) and the frame conclusion shall
processed in accordance with A.5.5.3.2.
In the event that an addressed ALE controller arrives on channel
too late to identify the size of the called group, it will be
unable to compute the correct Twan. In this situation,
it shall use a default value for Twan, which is equal
to the longest possible group call of twelve one-word addresses.
It will, however, have computed its correct slot number because
to have received its own address it must also have received the
addresses that followed that self address in the leading call.
Slotted responses shall be sent and checked in accordance with
A.5.5.4.1, using the derived slot numbers and the self address
contained in the leading call.
An ALE controller that responded to a group call shall await acknowledgment and process an incoming acknowledgment in accordance with A.5.5.3.4, with the following exceptions:
An ALE controller that responded but was not named in the acknowledgment shall return to its pre-linking state. An ALE controller that is addressed in the acknowledgment shall proceed as follows:
In the example group call in figure A-35, SAMUEL will respond
in slot 1, with Tswt = 14 Tw (the one-word
address JOE causes slot 0 to be 14 Tw). EDGAR
will respond in slot 2, with Tswt = 14 +
17 Tw = 31 Tw (slot 1 is 17 Tw
because of SAMUEL's two-word address). BOB will
respond in slot 3, with Tswt = 48 Tw. JOE
will send an acknowledgment after 62 Tw.
If a station is addressed multiple times in a group call, even
by different addresses, it shall properly respond to at least
one address.
NOTE: The fact that the called station has multiple addresses
may not be known to the caller. In some cases, it would be confusing
or inappropriate to respond to one but not another address. Redundant
calling address conflicts can be resolved after successful linking,
if there is a problem.
An AllCall requests all stations hearing it to stop and listen,
but not respond. The AllCall special address structure(s) (see
A.5.2.4.7) shall be the exclusive member(s) of the scanning call
and the leading call, and shall not be used in any other address
field or any other part of the handshake. The global AllCall
address shall appear only in TO words. Selective AllCalls
with more than one selective AllCall address, however, shall be
sent using group addressing, using THRU during the scanning
call and TO during the leading call.
An AllCall pertains to an ALE controller when it is a global AllCall, or when a selective AllCall specifies a character that matches the last character of any self address assigned to that station. Upon receipt of a pertinent AllCall, an ALE controller shall temporarily stop scanning and listen for a preset limited time, Tcc max.
If a pertinent AllCall frame is successfully received and is concluded
with a TIS, the controller shall enter the linked state,
alert the operator, unmute its speaker and start a wait-for-activity
timeout. If an AllCall is successfully received with a TWAS
conclusion, the called controller shall automatically resume scanning
and not respond (unless otherwise directed by the operator or
controller).
If a station receiving an AllCall desires to attempt to link with
the calling station, the operator may initiate a handshake within
the pause after a TIS conclusion. Note that in all handshakes
(the initial AllCall does not constitute a handshake), the AllCall
address shall not be used. To minimize possible adverse effects
resulting from overuse or abuse of AllCalls, controllers shall
have the capability to ignore AllCalls. Normally AllCall processing
should be enabled.
An AnyCall is similar to an AllCall, but it instead requests responses.
Use of the AnyCall special address structures is identical to
that for the AllCall special address structures. Upon receipt
of a pertinent AnyCall, an ALE controller shall temporarily stop
scanning and examine the call identically to the procedure for
AllCalls, including the Tcc max, Tm
max, and Tx max limits.
If the AnyCall is successfully received, and is concluded with TIS, the controller shall enter the linking state and automatically generate a slotted response in accordance with A.5.5.4.1 and the following special procedure:
In this protocol, collisions are expected and tolerated. The
station sending the AnyCall shall attempt to read the best response
in each slot.
Upon receipt of the slotted responses, the calling station shall
transmit an ACK to any subset of stations whose responses were
read, using an individual or group address. The AnyCall special
address shall not be used in the acknowledgment. The caller
selects the conclusion of its ACK to either maintain the link
for additional interoperation and traffic with the responders
(TIS), or return everyone to scan (TWAS), as appropriate
to the caller's original purpose.
An ALE controller that responded to an AnyCall shall await and
process the acknowledgment in accordance with A.5.5.4.3.6.
To minimize possible adverse effects resulting from overuse or
abuse of AnyCalls, controllers shall have the capability to ignore
AnyCalls. Normally AnyCall processing should be enabled.
Wildcard addresses shall be the exclusive members of a calling
cycle in a call, and shall not be used in any other address sequence
in the ALE frame or handshake. The span (number of cases possible)
of the wildcard(s) used should be minimized to only the essential
needs of the user(s).
Calls to wildcard addresses that conclude with TWAS shall
be processed identically to the AllCall protocol.
Responses to wildcard calls that conclude with TIS shall
be sent in pseudorandomly-selected slots in accordance with the
AnyCall protocol.
As in both the AllCall and AnyCall, the controller shall be programmable
to ignore wildcard calls, but wildcard call processing should
normally be enabled.
In addition to automatically establishing links, stations shall
have the capability to transfer information within the orderwire,
or message, section of the frame. This section describes these
messages, including data, control, error checking, networking,
and special purpose functions. Table A-XVI provides a summary
of the CMD functions.
NOTE: For critical orderwire messages that require increased protection from interference and noise, several ALE techniques are available. Any message may be specially encoded off-line and then transmitted using the full 128 ASCII CMD data DTM mode (which also accepts random data bits). Larger blocks of information may be Golay FEC coded and deeply interleaved using the CMD DBM mode. Both modes have an automatic repeat request (ARQ) error-control capability. Integrity of the data may be ensured using the CMD cyclic redundancy check (CRC) mode (see A.5.6.1). In addition, once a link has been established, totally separate equipment, such as heavily coded and robust modems, may be switched onto the rf link in the normal circuit (traffic-bearing) mode.
| First Character | Second Character | Function | |||||||||||
| Any of the extended-64 character set AMD | |||||||||||||
| " | 1100000 | Advanced LQA | |||||||||||
| a | 1100001 | LQA | |||||||||||
| b | 1100010 | Data block analysis | |||||||||||
| c | 1100011 | Channels | |||||||||||
| d | 1100100 | DTM | |||||||||||
| f | 1100110 | Frequency | |||||||||||
| m | 1101101 | Mode selection commands | |||||||||||
| a | 1100001 | Analog port Selection | |||||||||||
| c | 1100011 | Crypto negotiation | |||||||||||
| d | 1100100 | Data port selection | |||||||||||
| n | 1101110 | Modem negotiation | |||||||||||
| q | 1110001 | Digital squelch | |||||||||||
| n | 1101110 | Noise report | |||||||||||
| p | 1110000 | Power control | |||||||||||
| r | 1110010 | LQA report | |||||||||||
| t | 1110100 | Scheduling commands | |||||||||||
| a | 1100001 | Adjust slot width | |||||||||||
| b | 1100010 | Station busy | |||||||||||
| c | 1100011 | Channel busy | |||||||||||
| d | 1100100 | Set dwell time | |||||||||||
| h | 1101000 | Halt and wait | |||||||||||
| l | 1101100 | Contact later | |||||||||||
| m | 1101101 | Meet me | |||||||||||
| n | 1101110 | Poll operator (default NAK) | |||||||||||
| o | 1101111 | Request operator ACK | |||||||||||
| p | 1110000 | Schedule periodic function | |||||||||||
| q | 1110001 | Quiet contact | |||||||||||
| r | 1110010 | Respond and wait | |||||||||||
| s | 1110011 | Set sounding interval | |||||||||||
| t | 1110100 | Tune and wait | |||||||||||
| w | 1110111 | Set slot width | |||||||||||
| x | 1111000 | Do not respond | |||||||||||
| y | 1111001 | Year and date | |||||||||||
| z | 1111010 | Zulu time | |||||||||||
| v | 1110110 | c | 1100011 | Capabilities | |||||||||
| s | 1110011 | Versions | |||||||||||
| x | 1111000 | CRC* | |||||||||||
| y
z { | 1111001
1111010 1111011 | CRC*
CRC* CRC* | |||||||||||
| | | 1111100 | User-unique functions | |||||||||||
| ~ | 1111110 | Time exchange | |||||||||||
| *(16-bit CRC overflows into the two least-significant bits of the first two character) | |||||||||||||
This special error-checking function is available to provide data
integrity assurance for any form of message in an ALE call.
NOTE: The CRC function is optional, but mandatory when used with
the DTM or DBM modes.
The 16-bit frame check sequence (FCS) and method as specified
by FED-STD 1003 shall be used herein. The FCS provides a probability
of undetected error of 2-16, independent of the number
of bits checked. The generator polynomial is
and the sixteen FCS bits are designated
(MSB) X15, X14, X13, X12...X1,
X0 (LSB)
The ALE CRC is employed two ways: within the DTM data words,
and following the DBM data field, described in paragraphs A.5.7.3
and A.5.7.4, respectively. The first, and the standard, usages
are described in this section.
The CMD CRC word shall be constructed as shown in table
A-XVII. The preamble shall be CMD (110) in bits P3 through
P1 (W1 through W3). The first character shall be "x"
(1111000), "y" (1111001), "z" (1111010), or
"{" (1111011) in bits C1-7 through C1-1 (W4 through
W10). Note that four identifying characters result from FCS bits
X15 and X14 which occupy C1-2 and C1-1 (W9
and W10) in the first character field respectively. The conversion
of FCS bits to and from ALE CRC format bits shall be as described
in table A-XVII where X15 through X0 correspond
to W9 through W24.
The CMD CRC message should normally appear at the end of the message section of a transmission, but it may be inserted within the message section (but not within the message being checked) any number of times for any number of separately checked messages, and at any point except the first word (except as noted below). The CRC analysis shall be performed on all ALE words in the message section that precede the CMD CRC word bearing the FCS information, and which are bounded by the end of the calling cycle, or the previous CMD CRC word, whichever is closest. The selected ALE words shall be analyzed in their non-redundant and unencoded (or FEC decoded) basic ALE word (24-bit) form in the bit sequence (MSB) W1, W2, W3, W4...W24 (LSB), followed by the unencoded bits W1 through W24 from the next word sent (or received), followed by the bits of the next word, until the first CMD CRC is inserted (or found). Therefore, each CMD CRC inserted and sent in the message section ensures the data integrity of all the bits in the previous checked ALE words, including their preambles. If it is necessary to check the ALE words in the calling cycle (TO) preceding the message section, an optional calling cycle CMD CRC shall be used as the calling cycle terminator (first FROM or CMD), shall therefore appear first in the message section, and shall analyze the calling cycle words in their simplest (Tc), nonredundant and nonrotated form. If it is necessary to check the words in a conclusion (TIS or TWAS), an optional conclusion CRC shall directly precede the conclusion portion of the call, shall be at the end of the message section, and shall itself be directly preceded by a separate CMD CRC (which may be used to check the message section or calling cycle, as described herein). Stations shall perform CRC analysis on all received ALE transmissions and shall be prepared to compare analytical FCS values with any CMD CRC words which may be received. If a CRC FCS comparison fails, an ARC (or operator initiated) or other appropriate procedure may be used to correct the message.
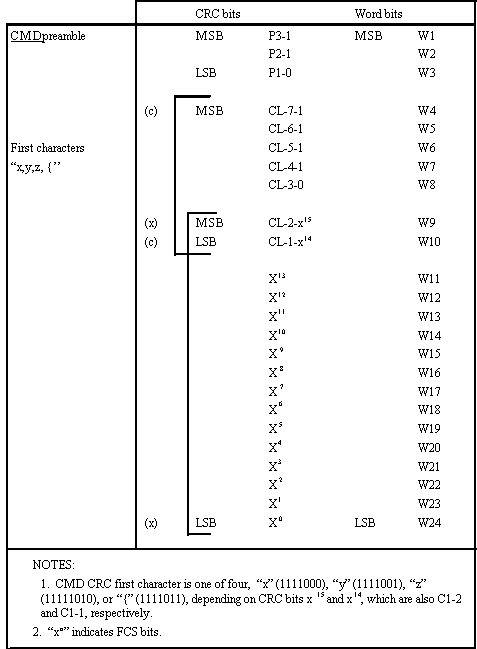
The power control orderwire function is used to advise parties
to a link that they should raise or lower their rf power for optimum
system performance. The power control CMD word format
shall be as shown in figure A-36. The KP control bits shall be
used as shown in table XVIII.
|
CMD | 1110000
('p': power control) | KP1-3 | Power |
(reserved) |
| Bit | Value | Meaning |
| KP3 (MSB)
KP2 KP1 (LSB) | 1
0 1 0 1 0 | Request to adjust power
Report of current power level Relative Power (in dB) Absolute Power (in dBW) Relative Power (dB) is positive Relative Power (dB) is negative |
The procedure shall be:
a. When KP3 is set to 1, the power control command is a request to adjust the power from the transmitter. If KP2 is 1, the adjustment is relative to the current operating power, i.e., to raise (KP1 = 1) or lower (KP1 = 0) power by the number of dB indicated in the relative power field. If KP2 is 0, the requested power is specified as an absolute power in dBW.
b. When KP3 is set to 0, the power control command reports the current power output of the transmitter, in dB relative to nominal power if KP2 is 1, or in absolute dBW if KP2 is 0.
c. KP1 shall be set to 0 whenever KP2 is 0.
d. Normally, a station receiving a power control request (KP3
= 1) should approximate the requested effect as closely
as possible, and respond with a power report (KP3 =
0) indicating the result of its power adjustment.
When two or more stations need to explicitly refer to channels
or frequencies other than the one(s) in use for a link, the following
encodings shall be used. A frequency is designated using binary-coded-decimal
(BCD). The standard frequency designator is a five-digit string
(20 bits), in which the first digit is the 10 megahertz (MHz)
digit, followed by 1 MHz, 100 kilohertz (kHz), 10 kHz, and 1 kHz
digits. A frequency designator is normally used to indicate an
absolute frequency. When a bit in the command associated with
a frequency designator indicates that a frequency offset is specified
instead, the command shall also contain a bit to select either
a positive or a negative frequency offset.
A channel differs from a frequency in that a channel is a logical
entity that implies not only a frequency (or two frequencies for
a full-duplex channel), but also various operating mode characteristics,
as defined in A.4.3.1. As in the case of frequency designators,
channels may be specified either absolutely or relatively. In
either case, a 7-bit binary integer shall be used that is interpreted
as an unsigned integer in the range 0 through 127. Bits in the
associated command shall indicate whether the channel designator
represents an absolute channel number, a positive offset, or a
negative offset.
a. The frequency select CMD word shall be formatted as
shown in figure A-37. A frequency designator (in accordance with
A.5.6.3.1) is sent in a DATA word immediately following
the frequency select CMD; bit W4 of this DATA word
shall be set to 0, as shown.
| CMD | 1100110
('f': frequency) | Control | 100 Hz | 10 Hz |
|
DATA | 0 | Frequency Designator | ||||||
| 10 MHz | 1 MHz | 100 kHz | 10 kHz | 1 kHz | ||||
b. The 100 Hz and 10 Hz fields in the frequency select CMD
word contain BCD digits that extend the precision of the standard
frequency designator. These digits shall be set to 0 except when
it is necessary to specify a frequency that is not an even multiple
of 1 kHz (e.g., when many narrowband modem channels are allocated
within a 3 kHz voice channel).
c. The control field shall be set to 000000 to specify a frequency absolutely, to 100000 to specify a positive offset, or to 110000 to specify a negative offset.
d. A station receiving a frequency select CMD word shall
make whatever response is required by an active protocol on the
indicated frequency.
Full duplex independent link establishment is an optional feature; however, if this option is selected the transmit and receive frequencies for use on a link shall be negotiated independently as follows:
a. The caller shall select a frequency believed to be propagating to the distant station (the prospective responder) and places a call on that frequency. The caller embeds a frequency select CMD word in the call to ask the responder to respond on a frequency chosen for good responder-to-caller propagation (probably from sounding data in the caller's LQA matrix).
b. If the responder hears the call, it shall respond on the second frequency, asking the caller to switch to a better caller-to-responder frequency by embedding a frequency select CMD word in its response (also based upon sounding data).
c. The caller shall send an acknowledgment on the frequency chosen
by the responder (the original frequency by default), and the
full duplex independent link is established.
See MIL-STD-187-721.
See MIL-STD-187-721.
See MIL-STD-187-721.
The CMD tune and wait special control function directs
the receiving station(s) to perform the initial parts of the handshake,
up through tune-up, and wait on channel for further instructions
during the specified time limit. The time limit timer is essentially
the WRTT as used in net slotted responses where its value Twrn
is set by the timing information in the special control instruction,
and it starts from the detected end of the call. The CMD
tune and wait instruction shall suppress any normal or preset
responses. Except for the tune-up itself, the receiving station(s)
shall make no additional emissions, and they shall quit the channel
and resume scan if no further instructions are received.
NOTE: This special control function enables very slow tuning
stations, or stations that must wait for manual operator interaction,
to effectively interface with automated networks.
The CMD tune and wait shall be constructed as follows and
as shown in table A-XIX. The preamble shall be CMD (110)
in bits P3 through P1 (W1 through W3). The first character (C1)
shall be "t" (1110100) in bits C1-7 through C1-1 (W4
through W10) and "t" (1110100) in bits C2-7 through
C2-1 (W11 through W17), for "time, tune-up." The "T"
time bits TB7 through TB1 (W18 through W24) shall be values selected
from table A-XX, and limited as shown in table A-XXI. The lowest
value (00000) shall cause the tuning to be performed immediately,
with zero waiting time, resulting in immediate return to normal
scan after tuning.
These special control functions permit the manipulation of timing in the ALE system. They are based on the standard "T" time values, presented in table A-XX, which have the following ranges based on exact multiples of Tw (130.66...ms) or Trw (392 ms).
There are several specific functions that utilize these special timing controls. All shall use the CMD (110) preamble in bits P3 through P1 (W1 through W3). The first character is "t" (1110100) for "time." The second character indicates the function as shown in table A-XXI. The basic structure is the same as in table A-XIX.
| Tune and Wait Bits | Word Bits | |||
| CMD
Preamble | MSB LSB | P3 = 1
P2 = 1 P1 = 0 | MSB | W1
W2 W3 |
| First
Character "t" | MSB LSB | C1-7 = 1
C1-6 = 1 C1-5 = 1 C1-4 = 0 C1-3 = 1 C1-2 = 0 C1-1 = 0 | W4
W5 W6 W7 W8 W9 W10 | |
| Second
Character "t" | MSB LSB | C2-7 = 1
C2-6 = 1 C2-5 = 1 C2-4 = 0 C2-3 = 1 C2-2 = 0 C2-1 = 0 | W11
W12 W13 W14 W15 W16 W17 | |
| Time Bits
"T" | MSB LSB | TB7
TB6 TB5 TB4 TB3 TB2 TB1 | LSB | W18
W19 W20 W21 W22 W23 W24 |
NOTES:
| ||||
| MULTIPLIER: MSBs | ||||||||||||||||||||
| MSB
TB7 (W18) | TB6
(W19) | Exact
increment |
| Approximate
range of "T" values | ||||||||||||||||
| 0 | 0 | Tw 130.66 . . ms | 0 - 4 seconds | |||||||||||||||||
| 0 | 1 | 3 Trw 1176 ms | 0 - 36 seconds | |||||||||||||||||
| 1 | 0 | 153 Trw 59.976 sec | 0 - 31 minutes | |||||||||||||||||
| 1 | 1 | 9184 Trw 60.002min | 0 - 29 hours | |||||||||||||||||
| INDEX: Least significant Bits (LSBs) | ||||||||||||||||||||
| TB5
(W20) | TB4
(W21) | TB3
(W22) | TB2
(W23) | LBS
TB1 (W24) | INDEX
VALUE | "T"
VALUE FOR MSB=00 | "T"
VALUE FOR MSB=01 | "T"
VALUE FOR MSB=10 | "T"
VALUE FOR MSB=11 | |||||||||||
| 0 | 0 | 0 | 0 | 0 | 0 | 0(1) | 0 | 0 | 0 | |||||||||||
| 0 | 0 | 0 | 0 | 1 | 1 | 130.66
ms | 1.176 s | 1.00 min | 1.00 hr | |||||||||||
| 0 | 0 | 0 | 1 | 0 | 2 | 261.33
ms | 2.352 s | 2.00 min | 2.00 hr | |||||||||||
| 0 | 0 | 0 | 1 | 1 | 3 | 392.0 ms | 3.528 s | 3.00 min | 3.00 hr | |||||||||||
| 0 | 0 | 1 | 0 | 0 | 4 | 523.66
ms | 4.204 s | 4.00 min | 4.00 hr | |||||||||||
| 0 | 0 | 1 | 0 | 1 | 5 | 653.33
ms | 5.880 s | 5.00 min | 5.00 hr | |||||||||||
| 1 | 1 | 1 | 0 | 1 | 29 | 3789.3
ms | 34.10 s | 29.0 min | 29.0 hr | |||||||||||
| 1 | 1 | 1 | 1 | 0 | 30 | 3920.0
ms | 35.28 s | 30.0 min | (3) | |||||||||||
| 1 | 1 | 1 | 1 | 1 | 31 | 4050.7
ms | 36.46 s | 31.0 min | (2) | |||||||||||
NOTES:
| ||||||||||||||||||||
Identification | First
Character | Second
Character | Function |
| Adjust Slot Width | "t" | "a" (1100001) | Add T to width of all slots for this response. TB=0, normal. TB7=0 as 36 second limit. |
| Halt and Wait | "t" | "h" (1101000) | Stop scan on channel, do not tune or respond, wait T for instruction; quit and resume scan if nothing. TB=0, quit after call. TB7=0 as 36 second limit. |
| Operator NAK | "t" | "n" (1101110) | Same as "t,o" operator ACK, except that at T, if no input, automatic tune-up and respond NAK (TIS), in slots if any. TB=0, NAK now. |
| Operator ACK | "t" | "o" (1101111) | Stop scan, alert operator to manually input ACK (or NAK), which causes tune-up (if needed) and ACK response TWAS, or TIS; if no input by operator by T, simply quit. TB=0, ACK now. TB7=0 as 36 second time limit. TB=1111111, do at date/time following. |
| Respond and Wait | "t" | "r" (1110010) | Stop scan, tune-up and respond as normal, wait T for instructions, quit and resume scan if nothing. TB=0, quit after response. TB7=0 as 36 second limit. TB=1111111, do at date/time following. |
| Tune and Wait | "t" | "t" (1110100) | Stop scan, tune-up, do not respond, wait T for Instructions, quit and resume scan if nothing. TB=0, quit after tune-up. TB7=0 as 36 second limit. |
| Width of Slots | "t" | "w" (1110111) | Set all slots to T wide for this response. TB=0, no responses. TB7=0 as 36 second limit. |
|
NOTES:
| |||
The mandatory time protocols employ the following three types
of ALE words: (1) command words, (2) coarse time words, and,
(3) authentication words, in the formats listed below.
Time exchange command words Time Is and Time Request
that are used to request and to provide time of day (TOD) data,
shall be formatted as shown in figure A-38. The three most-significant
bits (W1-3) shall contain the standard CMD preamble (110).
The next seven bits (W4-10) shall contain the ASCII character
'~'(1111110), indicating the magnitude of time uncertainty at
the sending station in accordance with A.5.6.4.6.
The Time Is command word carries the fine time current
at the sending station as of the start of transmission of the
word following the Time Is command word, and is used in
protected time requests and all responses. In a Time Is
command word, the seconds field shall be set to the current number
of seconds elapsed in the current minute intervals which have
elapsed in the current second (0-24). The time quality shall
reflect the sum of the uncertainty of the local time and the uncertainty
of the time of transmission of the Time Is command, in
accordance with table A-XXII and A.5.6.4.6. When a protocol requires
transmission of the Time Is command word, but no time value
is available, a NULL Time Is command word shall be sent,
containing a time quality of 7 and the seconds and ticks fields
both set to all 1s.
The Time Request command word shall be used to request
time when no local time value is available, and is used only in
non-protected transmissions. In a Time Request command
word, time quality shall be set to 7, the seconds field to all
1s, and the ticks field set to 30 (11110).
All encodings of the seconds and ticks fields not specified here
are reserved, and shall not be used until standardized.
Coarse time words shall be formatted as shown in figure A-39,
and shall contain the coarse time current as of the beginning
of that word.
| Time Service Example | ||||
| Date=8 May | ||||
| Time=15:57:34:12 | ||||
| Time Quality=4 | ||||
| CMD | Time Exchange | Time Quality | Seconds | 40 ms ticks |
| 110 | 1111110 | 100 | 100010 | 00011 |
| "TIME IS" Command |
Authentication words, formatted as shown in figure A-39, shall be used to authenticate the times exchanged using the time protocols. The 21-bit authenticator shall be generated by the sender as follows:
a. All 24-bit words in the time exchange message preceding the authentication word (starting with the Time Is or Time Request command word which begins the message) shall be exclusive-or'd.
b. If the message to be authenticated is in response to a previous time exchange message, the authenticator from that message shall be exclusive-or'd with the result of (1).
c. The 21 least significant bits of the final result shall be
used as the authenticator.
Every time exchange command word transmitted shall report the current uncertainty in TOD at the sending station, whether or not time is transmitted in the command word. The codes listed in table A-XXII shall be employed for this purpose. The time uncertainty windows on the table are upper bounds on total uncertainty (with respect to coordinated universal time).
| NOTE: Time quality "0" shall be used only by UTC time standard stations. | |
| Time Service Example | |||||||||||||||||
| Date = 8 May | |||||||||||||||||
| Time = 15:57:34:12 | |||||||||||||||||
| Time Quality = 4 | |||||||||||||||||
| DATA | 0 | Month | Day | Minute | |||||||||||||
| 000 | 0 | 0101 | 01000 | 011101111101 | |||||||||||||
| Coarse Time Word | |||||||||||||||||
| 21 | |||||||||||||||||
| REP | Authenticator | ||||||||||||||||
| 111 | 110101110011111111110 | ||||||||||||||||
| Authenticator Word | |||||||||||||||||
| (over CMD and Coarse Time Words) | |||||||||||||||||
For example, an uncertainty of ±6 seconds is 12 seconds total and requires a transmitted time quality value of 6. Stations shall power up from a cold start with a time quality of 7. Time uncertainty is initialized when time is entered (see B.5.2.2.1) and shall be maintained thereafter as follows:
a. The uncertainty increases at a rate set by oscillator stability (e.g., 72 ms per hour with a ±10 parts per million (ppm) time base).
b. Until the uncertainty is reduced upon the acceptance of time
with less uncertainty from an external source after which the
uncertainty resumes increasing at the above rate.
A station accepting time from another station shall add its own
uncertainty due to processing and propagation delays to determine
its new internal time uncertainty. For example, if a station
receives time of quality 2, it adds to the received uncertainty
of 100 ms (±50 ms) its own processing delay uncertainty of,
say ±100 ms, and a propagation delay bound of ±35 ms,
to obtain a new time uncertainty of ±185 ms, or 370 ms total,
for a time quality of 3. With a ±10 ppm time source, this
uncertainty window would grow by 72 ms per hour, so after two
hours, the uncertainty becomes 514 ms, and the time quality has
dropped to 4. If a low-power clock is used to maintain time while
the rest of the unit is powered off, the quality of this clock
shall be used to assign time quality upon resumption of normal
operation. For example, if the backup clock maintains an accuracy
of ±100 ppm under the conditions expected while the station
is powered off, the time uncertainty window shall be increased
by 17 seconds per day. Therefore, such a radio, which has been
powered-off for much over three days, shall not be presumed to
retain even coarse sync, despite its backup clock, and may require
manual entry of time.
If any of these features are selected, however, they shall be
implemented in accordance with this standard. Many of the advanced
features of an ALE controller are "modal" in the sense
that when a particular option setting is selected, that selection
remains in effect until changed or reset by some protocol event.
The mode control CMD is used to select many of these operating
modes, as described in the following paragraphs. The CMD
word shall be formatted as shown in figure A-40. The first character
shall be 'm' to identify the mode control command; the second
character identifies the type of mode selection being made; the
remaining bits specify the new setting for that mode.
|
CMD | 1101101
('m': mode control) | Mode ID | Mode Selection |
An ALE data link can be used to negotiate a modem to be used for
data traffic by exchanging modem negotiation messages. A modem
negotiation message shall contain one modem selection command.
NOTE: This function may best be implemented in a high frequency
node controller (HFNC) to avoid retrofit to existing ALE controllers,
and for the greater flexibility inherent in network management
information bases.
The modem selection CMD word shall be formatted as shown
in figure A-41, and may be followed by one or more DATA
words, as described below. The defined modem codes are listed
in table A-XXIII. Codes not defined are reserved, and shall not
be used until standardized.
|
CMD | 1101101
('m': mode control) | 1101110
('n': modem select) | Modem Code |
Modem negotiating shall employ modem negotiation messages in the following protocol:
a. The station initiating the negotiation will send a modem selection CMD word containing the code of the modem it wants to use.
b. The responding station(s) may either accept this modem selection or suggest alternatives. A station accepting a suggested modem shall send a modem selection CMD word containing the code of that modem.
c. A station may negotiate by sending a modem selection CMD word containing all 1s in the modem code field, followed by one or more DATA words containing the codes of one or more suggested modems. Modem codes shall be listed in order of preference in the DATA word(s). Unused positions in the DATA word(s) shall be filled with the all 1s code.
d. The negotiation is concluded when the most recent modem negotiation
message from all participating stations contains an identical
modem selection CMD word with the same modem code (not
all 1s). When this occurs, the station that initiated the negotiation
will normally begin sending traffic using the selected modem.
| Code | Modem Type |
| 0000000 | (Reserved) |
| 0000001 | ALE modem |
| 0000010 | Serial-tone HF data modem (MIL-STD-188-110) |
| 0000011 | 16-tone DPSK HF data modem (MIL-STD-188-110) |
| 0000100 | 39-Tone HF data modem (MIL-STD-188-110) |
| 0000101 | ANDVT |
| 0000110 | FSK 170 Hz shift (MIL-STD-188-110) |
| 0000111 | FSK 850 Hz shift (MIL-STD-188-110) |
| Short intlv (010xxxx) long intlv | STANAG 4285 |
| 0100000 0101000 | 75 b/s |
| 0100001 0101001 | 150 b/s |
| 0100010 0101010 | 300 b/s |
| 0100011 0101011 | 600 b/s |
| 0100100 0101100 | 1200 b/s |
| 0100101 0101101 | 2400 b/s |
| 0100110 0101110 | 4800 b/s |
| (011xxxx) | STANAG 4529: |
| 0110000 0111000 | 75 b/s |
| 0110001 0111001 | 150 b/s |
| 0110010 0111010 | 300 b/s |
| 0110011 0111011 | 600 b/s |
| 0110100 0111100 | 1200 b/s |
| 0110101 0111101 | 2400 b/s |
| 0110110 0111110 | 4800 b/s |
| 1111111 | Reserved to indicate no modem code. (All others reserved until defined) |
When crypto negotiation and handoff are required, the following applies:
a. An ALE data link can also be used to negotiate an encryption
device to be used for voice or data traffic by exchanging crypto
negotiation messages. The crypto selection CMD word is
formatted as shown in figure A-42. The defined crypto codes are
listed in table A-XXIV. Codes not defined are reserved, and shall
not be used until standardized.
NOTE: This function may best be implemented in an HFNC to avoid
retrofit to existing ALE controllers, and for the greater flexibility
inherent in network management information bases.
|
CMD | 1101101
('m': mode control) | 1100011
('c': crypto select) | Crypto Code |
| Code | Crypto Type |
| 0000000
1111111 | No encryption
Reserved to indicate no crypto code (All others reserved until defined) |
b. Crypto negotiation shall employ crypto negotiation messages
in the protocol described above for modem negotiation.
The version CMD function is used to request ALE controller
version identification. The first character is 'v' to indicate
the version family of ALE CMD word functions. The second
character shall be set to 's' to select a summary report.
NOTE: The capabilities function in A.5.6.6.2 is a variant of this function that provides more detailed information.
a. The response to a version CMD is a printable ASCII message
in manufacturer-specific format that indicates a manufacturers'
identification, the version(s) of hardware, operating firmware
and software, and/or management firmware and software of the responding
ALE controller, as requested by control bits KVC1-3
of the version CMD format (see figure A-43 and table A-
XXV).
|
CMD | 1110110
('v': version CMD) | 1110011
('s': summary) | Comps
(KVC) | Formats
(KVF) |
| Bit | Component whose version is requested when bit set to 1 |
| KVC3 (MSB)
KVC2 KVC1 (LSB) | ALE controller hardware
ALE controller operating firmware ALE controller network management firmware (i.e., HNMP) |
b. The requesting station specifies acceptable formats for the response in control bits KVF1-4 in accordance with table A-XXVI. A controller responding to a version function shall attempt to maximize the utility of its response and:
| Bit | Reporting format desired when bit set to 1 |
| KVF4 (MSB)
KVF3 KVF2 KVF1 (LSB) | Reserved (always set to 0)
DBM DTM AMD Message |
The capabilities function is used to obtain a compact representation
of the features available in a remote ALE controller. This function
uses a variant of the version CMD word, as shown in figures
A-44 and A-45.
The capabilities query, shown in figure A-44, consists of a single
ALE CMD word. The second character position shall be set
to 'c' to select a full capabilities report (rather than a summary
as in the version CMD). The third character position shall
be set to 'q' in a capabilities query to request a capabilities
report.
|
CMD | 1110110
('v': version CMD) | 1100011
('c': capability) | 1110001
('q': query) |
The capabilities report shall consist of a CMD word followed
by five DATA words, as shown in figure A-45. The second
character position of the capabilities report CMD word
shall be set to 'c' and the third character position shall be
set to 'r'. (The DATA preamble in the second and fourth
DATA words shall be replaced by REP for transmission,
as required by the ALE protocol).
|
|
| ||||
|
|
| ||||
|
|
| ||||
| ||||||
| Scheduling
(SCH1-21) | ||||||
The format of the DATA words in a capabilities report is
constant, regardless of the capabilities reported, to simplify
the software that implements the capabilities command. The data
fields of the capabilities report shall be encoded in accordance
with tables A-XXVII, A-XXVIII, and A-XXIX. The values encoded
shall represent the current operational capabilities of the responding
ALE controller, i.e., the timing or functions currently programmed.
All timing fields shall be encoded as unsigned integers.
Group | Field | Value |
Units | Parameter from
table A-XV "Timing" |
| ALE Timing | SR1-5
CS1-8 TT1-8 TTA1-4 TWA1-4 TWT1-3 | Scan rate
Chan. scanned Max tune time Turnaround time Activity timeout Listen time | Channels/s
100 ms 100 ms log2 s 1 s | 1/Td
C Tt Tta Twa* Twt |
* Twa=log2 n where n is the number of seconds of no detected activity before timeout. | ||||
| Group | Bit | Set to 1 if and only if (iff) | Cross Ref: MIL-STD |
| ALE
Protocols | VAP7 (MSB)
VAP6
VAP5 VAP4 VAP3 VAP2 VAP1 (LSB) | Accepting ALL calls
Accepting ANY calls
Accepting AMD 2msgs Accepting DTM msgs Accepting DBM msgs DTM capabilities DBM capabilities | 188-141 (Allcalls)
188-141 (AnyCalls) 188-141 (AMD mode) 188-141 (DTM mode) 188-141 (DBM mode) 188-141 (DTM mode) 188-141 (DBM mode) |
| LP Levels | LPL5 (MSB)
LPL4 LPL3 LPL2 LPL1 (LSB) | Capable of other LP
Capable of AL-4 LP Capable of AL-3 LP Capable of AL-2 LP Capable of AL-1 LP | 188-141 Appendix B 188-141 Appendix B 188-141 Appendix B 188-141 Appendix B |
| Time Exchange | LPT6 (MSB)
LPT5 LPT4 LPT3 LPT2 LPT1 (LSB) | Acting as time server
Active time acq. enable Passive time acq. enable Will send time broadcasts Time iteration capable Precision time capable | 188-141 (Time service response, Time service response (non-protected)
188-141 (Active time acquisition (protected), Active time acquisition (non-protected) 188-141 (Passive time acquisition) 188-141 (Time broadcast) (not yet standardized) (not yet standardized) |
| Group | Bit | Set to 1 iff Feature Implemented | Cross Ref: MIL-STD (paragraph) |
| Polling | PP5 (MSB)
PP4 PP3
PP2 PP1 (LSB) | Full Net Poll
Full Group Poll
Channel Scan CMD LQA Report Local Noise Report | 187-721 (Full Net Poll)
187-721 (Full Group Poll) 187-721 (Two Station- Multiple Channel Polling) 187-721 (LQA Report Protocol) 188-141 (Local Noise Report) |
| ALQA | ALQA8 (MSB)
ALQA7 ALQA6 ALQA5 ALQA4 ALQA3 ALQA2 ALQA1 (LSB) | Reserved (always set to 0)
ALQA SINAD ALQA PBER ALQA AI ALQA SD ALQA EFI ALQA AVQ ALQA ADC | 187-721 (SINAD and PBER) 187-721 (SINAD and PBER) 187-721 (Articulation Index) 187-721 (Spectral Distortion) 187-721 (Error-free Interval) 187-721 (Achievable Voice Quality) 187-721 (Available Data Capacity) |
| Orderwire | OW8 (MSB)
OW7
OW6 OW5 OW4 OW3 OW2 OW1 (LSB) | Frequency Select CMD
Channel Select CMD
Modem Negotiation Crypto Negotiation Analog Port Selection Data Port selection Digital Squelch Power Control | 187-721 (Frequency Select Command)
(not yet standardized) 188-141 (Modem Negotiation and Handoff) 188-141 (Crypto Negotiation and handoff) 187-721 (Analog Port Selection) 187-721 (Data Port Selection) 187-721 (Digital Squelch) 188-141 (Power Control) |
| Scheduling | SCH21 (MSB)
SCH20 SCH19 SCH18 SCH17 SCH16 SCH15 SCH14 SCH13 SCH12 SCH11 SCH10 SCH9 SCH8 SCH7 SCH6 SCH5 SCH4 SCH3 SCH2 SCH1 (LSB) | Reserved (always set to 0)
Adjust Slot Width Station Busy Channel Busy Set Dwell Time Halt and Wait Contact Later Meet Me Poll Operator (default NAK) Request Operator ACK Schedule Periodic Function Quiet Contact Respond and Wait Set Sounding Interval Tune and wait Set Slot Width Year and Date Zulu Time Do Not Respond Reserved (always set to 0) Reserved (always set to 0) | 187-721 (Adjust Slot Width) 187-721 (Station Busy) 187-721 (Channel Busy) 187-721 (Set Dwell Time) 187-721 (Halt and Wait) 187-721 (Contact Later) 187-721 (Meet Me) 187-721 (Poll Operator(default NAK)) 187-721 (Request Operator ACK) 187-721 (Schedule Periodic Function) 187-721 (Quiet Contact) 187-721 (Respond and Wait) 187-721 (Set Sounding Interval) 187-721 (Tune and Wait) 187-721 (Set Slot Width) 187-721 (Year and Date) 187-721 (Zulu Time)
188-141 (Do Not Respond) |
When an ALE controller receives this CMD in a transmission,
it shall not respond unless a response is specifically required
by some other CMD in the transmission (e.g., an LQA request
or a DTM or DBM with ARQ requested). In a Do Not Responds CMD,
no three-way ALE handshake needs to be completed.
See MIL-STD-187-721.
UUFs are for special uses, as coordinated with specific users
or manufacturers, which use the ALE system in conjunction with
unique, nonstandard, or non-ALE, purposes. There are 16384 specific
types of CMD UUF codes available, as indicated by a 14-bit
(or two-character) unique index (UI). Each unique type of special
function that employees a UUF shall have a specific UI assigned
to it to ensure interoperability, compatibility, and identification.
The UI shall be assigned for use before any transmission of the
UUF or the associated unique activity, and the ALE UUF shall always
include the appropriate UI when sent.
The UUF shall be used only among stations that are specifically
addressed and included within the protocol, and shall be used
only with stations specifically capable of participating in the
UUF activity, and all other (non-participating) stations should
be terminated. There are two exceptions for stations that are
not capable of participating in the UUF and are required to be
retained in the protocol until concluded. They shall be handled
using either of the two following procedures. First, the calling
station shall direct all the addressed and included stations to
stay linked for the duration of the UUF, to read and use anything
that they are capable of during that time, and to resume acquisition
and tracking of the ALE frame and protocol after the UUF ends.
To accomplish this, and immediately before the CMD UUF,
the sending station shall send the CMD STAY, which shall
indicate the time period (T) for which the receiving stations
shall wait for resumption of the frame and protocol. Second,
the sending station shall use any standard CMD function
to direct the non-participating stations to wait or return later,
or do anything else appropriate and controllable through the standard
orderwire functions.
If a CMD UUF is included within an ALE frame, it shall
only be within the message section. The UUF activity itself should
be conducted completely outside of the frame and should not interfere
with the protocols. If the UUF activity itself must be conducted
within the message section, will occupy time on the channel, and
is incompatible with the ALE system, that activity shall be conducted
immediately after the CMD UUF and it shall be for a limited
amount of time (T). A CMD STAY shall precede the UUF instruction,
as described herein, to indicate that time (T). The sending station
shall resume the same previous redundant word phase when the frame
and protocol resumes, to ensure synchronization. The STAY function
preserves maintenance of the frame and link. It instructs the
stations to wait, because the amount of time occupied by the UUF
activity or its signaling may conflict with functions such as
the wait-for-activity timer (Twa). This may interfere
with the protocols or maintenance of the link. In any case, the
users of the UUF shall be responsible for noninterference with
other stations and users, and also for controlling their own stations
and link management functions to avoid these conflicts.
| User Unique
Function Bits | Word Bits | |||
| CMD Preamble | MSB
LSB | P3=1
P2=1 P1=0 | MSB | W1
W2 W3 |
| First Character ¦ | MSB LSB | C1 (bit-7) =1
C1 (bit-6)=1 C1 (bit-5) =1 C1 (bit-4) =1 C1 (bit-3) =1 C1 (bit-2) =0 C1 (bit-1) =0 | W4
W5 W6 W7 W8 W9 W10 | |
| First UI Character | MSB LSB | UI-1-7
UI-1-6 UI-1-5 UI-1-4 UI-1-3 UI-1-2 UI-1-1 | W11
W12 W13 W14 W15 W16 W17 | |
| Second UI Character | MSB LSB | UI-2-7
UI-2-6 UI-2-5 UI-2-4 UI-2-3 UI-2-2 UI-2-1 | LSB | W18
W19 W20 W21 W22 W23 W24 |
NOTES:
| ||||
Three message protocols are available for carrying user data using
the ALE waveform and signal structure. The characteristics of
these three protocols are summarized in the table A-XXXI. All
ALE controllers complying with this appendix shall implement the
AMD protocol.
| Protocol | Mandatory | Character Set | Peak Throughput | ARQ |
| AMD | Y | Expanded 64 | 55 b/s | N |
| DTM | N | unrestricted | 61 b/s | Opt |
| DBM | N | unrestricted | 187 b/s | Opt |
The operators and controllers shall be able to send and receive
simple ASCII text messages using only the existing station equipment.
The expanded 64 ASCII subset shall include all capital alphabetics
(A-Z), all digits (0-9), the utility symbols "@" and
"?," plus 26 other commonly used symbols. See figure
A-46. The expanded 64 subset shall be used for all basic orderwire
message functions, plus special functions as may be standardized.
For orderwire message use, the subset members shall be enclosed
within a sequence of DATA (and REP) words and shall
be preceded by an associated CMD (such as DTM). The CMD
designates the usage of the information that follows, and shall
also be preceded by a valid and appropriate calling cycle using
the Basic 38 ASCII subset addressing. Digital discrimination
of the expanded 64 ASCII subset may be accomplished by examination
of the two MSBs (b7 and b6), as all of the
members within the "01" and "10" MSBs are
acceptable. No parity bits are transmitted because the integrity
of the information is protected by the basic ALE FEC and redundancy
and may be ensured by optional use of the CMD CRC as described
in A.5.6.1. The station shall have the capability to both send
and receive AMD messages from and to both the operator and the
controller. The station shall also have the capability to display
any received AMD messages directly to the operator and controller
upon arrival, and to alert them. The operator and controller
shall have the capability to disable the display and the alarm
when their functions would be operationally inappropriate.
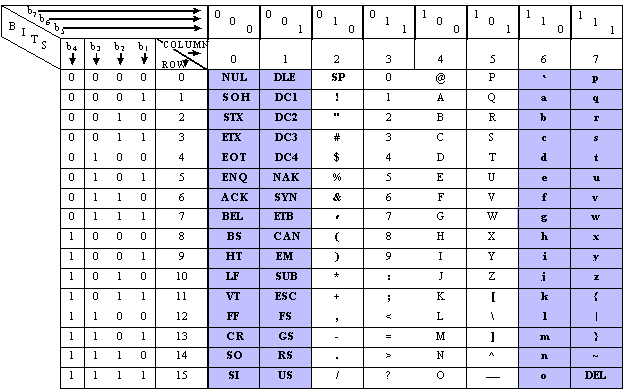
When an ASCII short orderwire AMD type function is required, the following CMD AMD protocol shall be used, unless another protocol in this standard is substituted. An AMD message shall be constructed in the standard word format, as described herein, and the AMD message shall be inserted in the message section of the frame. The receiving station shall be capable of receiving an AMD message contained in any ALE frame, including calls, responses, and acknowledgments. Within the AMD structure, the first word shall be a CMD AMD word, which shall contain the first three characters of the message. It shall be followed by a sequence of alternating DATA and REP words that shall contain the remainder of the message. The CMD, DATA, and REP words shall all contain only characters from the expanded ASCII 64 subset, which shall identify them as an AMD transmission. Each separate AMD message shall be kept intact and shall only be sent in a single frame, and in the exact sequence of the message itself. If one or two additional characters are required to fill the triplet in the last word sent, the position(s) shall be "stuffed" with the "space" character (0100000) automatically by the controller, without operator action. The end of the AMD message shall be indicated by the start of the frame conclusion, or by the receipt of another CMD. Multiple AMD messages may be sent within a frame, but they each shall start with their own CMD AMD with the first three characters.
Receipt of the CMD AMD word shall warn the receiving station that an AMD message is arriving and shall instruct it to alert the operator and controller and display the message, unless they disable these outputs. The station shall have the capability to distinguish among, and separately display, multiple separate AMD messages that were in one or several transmissions.
The AMD word format shall consist of a CMD (110) in bits
P3 through P1 (W1 through W3), followed by the three standard
character fields C1, C2, and C3. In each character field, each
character shall have its most significant bits (MSBs) bit 7 and
bit 6 (C1-7 and C1-6, C2-7 and C2-6, and C3-7 and C3-6) set to
the values of "01" or "10" (that is, all three
characters are members of the expanded ASCII 64 subset). The
rest of the AMD message shall be constructed identically, except
for the alternating use of the DATA and REP preambles.
Any quantity of AMD words may be sent within the message section of the frame within the
Tm max limitation of 30 words (90 characters).
Tm max shall be expanded from 30 words,
to a maximum of 59 words, with the inclusion of CMD words
within the message section. The maximum AMD message shall remain
30 words, exclusive of additional CMD words included within
the message section of the frame. The maximum number of CMD
words within the message section shall be 30. The message characters
within the AMD structure shall be displayed verbatim as received.
If a detectable information loss or error occurs, the station
shall warn of this by the substitution of a unique and distinct
error indication, such as all display elements activated (like
a "block"). The display shall have a capacity of at
least 20 characters (DO: at least 40). The AMD message storage
capacity, for recall of the most recently received message(s),
shall be at least 90 characters plus sending station address.
(DO: at least 400). By operator or controller direction, the
display shall be capable of reviewing all messages in the AMD
memory and shall also be capable of identifying the originating
station's address. If words are received that have the proper
AMD format but are within a portion of the message section under
the control of another message protocol (such as DTM), the other
protocol shall take precedence and the words shall be ignored
by the station's AMD function.
NOTE: If higher data integrity or reliability is required, the
CMD DTM and DBM protocols should be used.
The DTM ALE (orderwire) message protocol function enables stations
to communicate (full ASCII or unformatted binary bits) messages
to and from any selected station(s) for direct output to and input
from associated data terminals or other date terminal equipment
(DTE) devices through their standard data
circuit-terminating equipment (DCE) ports. The DTM data
transfer function is a standard speed mode (like AMD) with improved
robustness, especially against weak signals and short noise bursts.
When used over medium frequency (MF)/HF by the ALE system, DTM
orderwire messages may be unilateral or bilateral, and broadcast
or acknowledged. As the DTM data blocks are of moderate sizes,
this special orderwire message function enables utilization of
the inherent redundancy and FEC techniques to detect weak HF signals
and tolerate short noise bursts.
The DTM data blocks shall be fully buffered at each station and
should appear transparent to the using DTEs or data terminals.
As a DO, and under the direction of the operator or controller,
the stations should have the capability of using the DTM data
traffic mode (ASCII or binary bits) to control switching of the
DTM data traffic to the appropriate DCE port or associated DTE
equipment, such as to printers and terminals (if ASCII mode),
or computers and cryptographic devices (if binary bits mode).
As an operator or controller selected option, the received DTM
message may also be presented on the operator display similar
to the method for AMD in A.5.7.2.
There are four CMD DTM modes: BASIC, EXTENDED, NULL, and
ARQ. The DTM BASIC block ranges over a moderate size and contains
a variable quantity of data, from zero to full as required, which
is exactly measured to ensure integrity of the data during transfer.
The DTM EXTENDED blocks are variable over a larger range of sizes,
in integral multiples of the ALE basic word, and are filled with
integral multiples of message data. The DTM NULL and ARQ modes
are used for both link management, and error and flow control.
The characteristics of the CMD DTM orderwire message functions
are listed in table A-XXXII and are summarized below:
CMD DTM Mode BASIC EXTENDED ARQ NULL
| Maximum Size, Bits | 651 | 7371 | 0 |
| Cyclic Redundancy Check | 16 Bits | 16 Bits | 0 |
| Data Capacity, ASCII | 0-93 | 3-1053, by 3 | 0 |
| Data Capacity, Bits | 1-651 | 21-7371, by 21 | 0 |
| ALE Word Redundancy | 3 Fixed | 3 Fixed | 0 |
| Data Transmission | 392 ms - | 392 ms - | 0 |
| 12.152 sec | 2.29 min |
When an ASCII, or binary bit, digital data message function is
required, the following CMD DTM orderwire structures and
protocols shall be used as specified herein, unless another standardized
protocol is substituted. The DTM structure shall be inserted
within the message section of the standard ALE frame. A CMD
DTM word shall be constructed in the standard
24-bit format, using the CMD preamble (see table A-XXXIII).
The message data to be transferred shall also be inserted in
words, using the DATA and REP preambles. The words
shall then be Golay FEC encoded and interleaved, and then shall
be transmitted immediately following the CMD DTM word.
A CMD CRC shall immediately follow the data block words,
and it shall carry the error control CRC FCS.
When the DTM structure transmission time exceeds the maximum limit
for the message section (Tm max), the DTM
protocol shall take precedence and shall extend the Tm
limit to accommodate the DTM. The DTM mode preserves the required
consistency of redundant word phase during the transmission.
The message expansion due to the DTM is always a multiple of one
Trw, as the basic ALE word structure is used. The
transmission time of the DTM data block (DTM words x 392 ms) does
not include the Trw for the preceding CMD DTM
word or the following CMD CRC. Figure A-47 shows an example
of a DTM message structure.
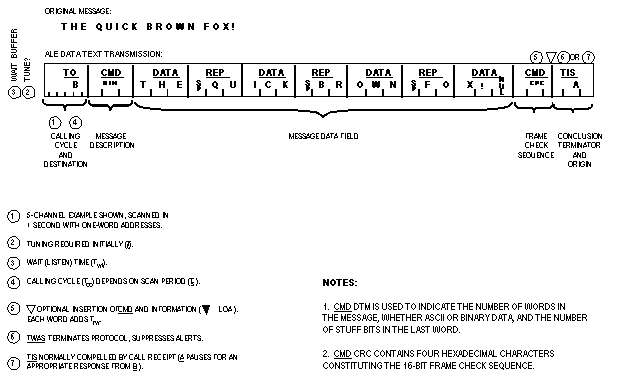
The DTM protocol shall be as described herein. The CMD
DTM BASIC and EXTENDED formats (herein referred to as DTM data
blocks) shall be used to transfer messages and information among
stations. The CMD DTM ARQ format shall be used to acknowledge
other CMD DTM formats and for error and flow control, except
for non-ARQ and one-way broadcasts. The CMD DTM NULL format
shall be used to (a) interrupt ("break") the DTM and
message flow, (b) to interrogate station to confirm DTM capability
before initiation of the DTM message transfer protocols, and (c)
to terminate the DTM protocols while remaining linked. When used
in ALE handshakes and subsequent exchanges, the protocol frame
terminations for all involved stations shall be TIS until
all the DTM messages are successfully transferred, and all are
acknowledged if ARQ error control is required. The only exceptions
shall be when the protocol is a one-way broadcast or the station
is forced to abandon the exchange by the operator or controller,
in which cases the termination should be TWAS.
Once a CMD DTM word of any type has been received by a
called (addressed) or linked station, the station shall remain
on channel for the entire specified DTM data block time (if any),
unless forced to abandon the protocol by the operator or controller.
The start of the DTM data block itself shall be exactly indicated
by the end of the CMD DTM BASIC or EXTENDED word itself.
The station shall attempt to read the entire DTM data block information
in the DATA and REP words, and the following CMD
CRC, plus the expected frame continuation, which shall contain
a conclusion (possibly preceded by additional functions in the
message section, as indicated by additional CMD words).
With or without ARQ, identification of each DTM data block and
its associated orderwire message (if segmented into sequential
DTM data blocks) shall be achieved by use of the sequence and
message control bits, KD1 and KD2, (as shown in table A-XXXIII),
which shall alternate with each DTM transmission and message,
respectively. The type of data contained within the data block
(ASCII or binary bits) shall be indicated by KD3 as a data identification
bit. Activation of the ARQ error control protocol shall use the
ARQ control bit KD4. If no ARQ is required, such as in one-way
broadcasts, multiple DTM data blocks may be sent in the same frame,
but they shall be in proper sequential order if they are transferring
a segmented message.
When ARQ error or flow control is required, the CMD DTM
ARQ shall identify the acknowledged DTM data block by the use
of the sequence and message control bits KD1 and KD2, which shall
be set to the same values as the immediately preceding and referenced
DTM data block transmission. Control bit KD3 shall be used as
the DTM flow control to pause or continue (or resume) the flow
of the DTM data blocks. The ACK and request-for-repeat (NAK)
functions shall use the ARQ control bit KD4. If no ARQ has been
required by the sending station, but the receiving station needs
to control the flow of the DTM data blocks, it shall use the DTM
ARQ to request a pause in, and resumption of, the flow.
| DTM Bits | Word Bits | |||
| CMD
preamble | MSB LSB | P3=1
P2=1 P1=0 | MSB | W1
W2 W3 |
| First
character "d" | MSB LSB | C1 (bit-7) = 1
C1 (bit-6) = 1 C1 (bit-5) = 0 C1 (bit-4) = 0 C1 (bit-3) = 1 C1 (bit-2) = 0 C1 (bit-1) = 0 | W4
W5 W6 W7 W8 W9 W10 | |
| Control
bits | MSB LSB | KD4
KD3 KD2 KD1 | W11
W12 W13 W14 | |
| DTM
data code bits | MSB LSB | DC10
DC9 DC8 DC7 DC6 DC5 DC4 DC3 DC2 DC1 | LSB | W15
W16 W17 W18 W19 W20 W21 W22 W23 W24 |
NOTES:
| ||||
When data transfer ARQ error and flow control is required, the
DTM data blocks shall be sent individually, in sequence, and each
DTM data block shall be acknowledged before the next DTM data
block is sent. Therefore, with ARQ there shall be only one DTM
data block transmission in each ALE frame. If the transmitted
DTM data block causes a NAK in the returned DTM ARQ, as described
below, or if ACK or DTM ARQ is detected in the returned frame,
or if no ALE frame is detected at all, the sending station shall
resend an exact duplicate of the unacknowledged DTM data block.
It shall send and continue to resend duplicates (which should
be up to at least seven) one at a time and with appropriate pauses
for responses, until the involved DTM data block is specifically
acknowledged by a correct DTM ARQ. Only then shall the next DTM
data block in the sequence be sent. If the sending station is
frequently or totally unable to detect ALE frame or DTM ARQ responses,
it should abort the DTM transfer protocol, terminate the link,
and relink and reinitiate the DTM protocol on a better channel,
under operator or controller direction.
Before initiation of the DTM data transfer protocols, the sending
stations should confirm the existence of the DTM capability in
the intended receiving stations, if not already known. When a
DTM interrogation function is required, the following protocol
shall be used. Within any standard protocol frame (using TIS),
the sending station shall transmit a CMD DTM NULL, with
ARQ required, to the intended station(s). These receiving stations
shall respond with the appropriate standard frame and protocol,
with the following variations. They shall include a CMD
DTM ARQ if they are DTM capable, and they shall omit it if they
are not DTM capable. The sending station shall examine the ALE
and DTM ARQ responses for existence, correctness, and the status
of the DTM KD control bits, as described herein. The transmitted
CMD DTM NULL shall have its control bits set as follows:
KD1 and KD2 set opposite of any subsequent and sequential CMD
DTM BASIC or EXTENDED data blocks, which will be transmitted next;
KD3 set to indicate the intended type of traffic, and KD4 set
to require ARQ. The returned CMD DTM ARQ shall have its
control bits set as follows: KD1 and KD2 set to match the interrogating
DTM NULL; KD3 set to indicate if the station is ready for DTM
data exchanges, or if a pause is requested; and KD4 set to ACK
if the station is ready to accept DTM data transmissions with
the specified traffic type, and NAK if it cannot or will not participate,
or it failed to read the DTM NULL.
The sending (interrogating) station shall handle any and all stations
that return a NAK, or do not return a DTM ARQ at all, or do not
respond at all, in any combination of the following three ways,
and for any combination of these stations. The specific actions
and stations shall be selected by the operator or controller.
The sending station shall: (a) terminate the link with them,
using an appropriate and specific call and the TWAS terminator;
or (b) direct them to remain and stay linked during the transmissions,
using the CMD STAY protocol in each frame immediately before
each CMD DTM word and data block sent; or (c) redirect
them to do anything else that is controllable using the CMD
functions described within this standard.
Each received DTM data block shall be examined using the CRC data
integrity test included within the mandatory associated CMD
CRC that immediately follows the DTM data block structure. If
the data block passes the CRC test, the data shall be passed through
to the appropriate DCE port (or normal output as directed by the
operator or controller). If the data block is part of a larger
message segmented before DTM transfer, it shall be recombined
before output. If any DTM data blocks are received and do not
pass the CRC data integrity test, any detectable but uncorrectable
errors or areas likely to contain errors and should be tagged
for further analysis, error control, or inspection by the operator
or controller.
If ARQ is required, the received but unacceptable data block shall be temporarily stored, and a DTM ARQ NAK shall be returned to sender, who shall retransmit an exact duplicate DTM data block. Upon receipt of the duplicate, the receiving station shall again test the CRC. If the CRC is successful, the data block shall be passed through as described before, the previously unacceptable data block should be deleted, and a DTM ARQ ACK shall be returned. If the CRC fails again, both the duplicate and the previously stored data blocks shall be used to correct, as possible, errors and to create an "improved" data block. See figure A-48 for an example of data block reconstruction. The "improved" data block shall then be CRC tested. If the CRC is successful, the "improved" data block is passed through, the previously unacceptable data blocks should be deleted, and a DTM ARQ ACK shall be returned. If the CRC test fails, the "improved" data block shall be stored and a DTM ARQ NAK shall be returned. This process shall be repeated until: (a) a received duplicate, or an "improved" data block passes the CRC test (the data block is passed through, and a DTM ARQ ACK is returned); (b) the maximum number of duplicates (such as seven or more) have been sent without success (with actions by the sender as described above); or (c) the operators or controllers terminate or redirect the DTM protocol.
During reception of ALE frames and DTM data blocks, it is expected
that fades, interferences, and collisions will occur. The receiving
station shall have the capability to maintain synchronization
with the frame and the DTM data block transmission, once initiated.
It shall also have the capability to read and process any colliding
and significantly stronger (that is, readable) ALE signals without
confusing them with the DTM signal (basic ALE reception in parallel,
and always listening). Therefore, useful information that may
be derived from readable collisions of ALE signals should not
be arbitrarily rejected or wasted. The DTM structures, especially
the DTM EXTENDED, can tolerate weak signals, short fades, and
short noise bursts. For these cases and for collisions, the DTM
protocol can detect DTM words that have been damaged and "tag"
them for error correction or repeats. The DTM constructions are
described herein. Within the DTM data block structure, the CMD
DTM word shall be placed ahead of the DTM data block itself.
The DTM word shall alert the receiving station that a DTM data
block is arriving, how long it is, what type of traffic it contains,
what its message and block sequence is, and if ARQ is required.
It shall also indicate the exact start of the data block (the
end of the CMD DTM word), and shall initiate the reception,
tracking, decoding, reading, and checking of the message data
contained within the data block, which itself is within the DATA
and REP words. The message data itself shall be either
one of two types, binary bits or ASCII.
The ASCII characters (typically used for text) shall be the standard
7-bit length, and the start, stop, and parity bits shall be removed
at the sending (and restored at the receiving) station. The binary
bits (typically used for other character formats, computer files,
and cryptographic devices) may have any (or no) pattern or format,
and they shall be transferred transparently (that is, exactly
as they were input to the sending station) with the same length
and without modification.
The size of the DTM BASIC or EXTENDED data block shall be the
smallest multiple of DATA and REP words that will
accommodate the quantity of the ASCII or binary bits message data
to be transferred in the DTM data block. If the message data
to be transferred does not exactly fit the unencoded data field
of the DTM block size selected, the available empty positions
shall be "stuffed" with ASCII "DEL" (1111111)
characters or all "1" bits. The combined message and
"stuff" data in the uncoded DTM data field shall then
be checked by the CRC for error control in the DTM protocol.
The resulting 16-bit CRC word shall always be inserted into the
CMD CRC word that immediately follows the DTM data block
words themselves. All the bits in the data field shall then be
inserted into standard DATA and REP words on a 21-bit
or three-character basis and Golay FEC encoded, interleaved, and
tripled for redundancy. Immediately after the CMD DTM
word, the DTM DATA and REP words shall follow standard
word format, and the CMD CRC shall be at the end.
The DTM BASIC data block has a relatively compact range of sizes
from 0 to 31 words and shall be used to transfer any quantity
of message data between zero and the maximum limits for the DTM
BASIC structure, which is up to 651 bits or 93 ASCII characters.
It is capable of counting the exact quantity of message data
it contains, on a bit-by-bit basis. It should be used as a single
DTM for any message data within this range. It shall also be
used to transfer any message data in this size range that is an
"overflow" from the larger size (and increments) DTM
EXTENDED data blocks, which shall immediately precede the DTM
BASIC in the DTM sequence of sending.
The DTM EXTENDED data blocks are also variable in size in increments
of single ALE words up to 351. They should be used as a single,
large DTM to maximize the advantages of DTM throughput. The size
of the data block should be selected to provide the largest data
field size that can be totally filled by the message data to be
transferred. Any "overflow" shall be in a message data
segment sent within an immediately following and appropriately
sized DTM EXTENDED or BASIC data block. Under operator or controller
direction, multiple DTM EXTENDED data blocks, with smaller than
the maximum appropriate ID sizes, should be selected if they will
optimize DTM data transfer throughput and reliability. However,
these multiple data blocks will require that the message data
be divided into multiple segments at the sending station, that
they be sent only in the exact order of the segments in the message,
and that the receiving stations recombine the segments into a
complete received message. When binary bits are being transferred,
the EXTENDED data field shall be filled exactly to the last bit.
When ASCII characters are being transferred, there are no stuff
bits as the 7-bit characters fit the ALE word 21-bit data field
exactly.
If stations are exchanging DTM data blocks and DTM ARQs, they
may combine both functions in the same frames, and they shall
discriminate based on the direction of transmission and the sending
and destination addressing. If ARQ is required in a given direction,
only one DTM data block shall be allowed within any frame in that
direction, and only one DTM ARQ shall be allowed in each frame
in the return direction. If no ARQ is required in a given direction,
multiple DTM data blocks may be included in frames in that direction,
and multiple DTM ARQ's may be included in the return direction.
As always throughout the DTM protocol, any sequence of DTM data
blocks to be transferred shall have the KD1 sequence control bits
alternating with the preceding and following DTM data blocks (except
duplicates for ARQ, which shall be exactly the same as the originally
transmitted DTM data block).
Also, all multiple DTM data blocks transferring multiple segments
of a larger data message shall all have their KD2 message control
bits set to the same value, and opposite of the preceding and
following messages. If a sequence of multiple but unrelated DTM
data blocks are sent (such as several independent and short messages
within several DTM BASIC data blocks), they may be sent in any
sequence. However, the KD1 or KD2 sequence and message control
bits shall alternate with those in the adjacent DTM data blocks.
The CMD DTM words shall be constructed as shown in table
A-XXXIII. The preamble shall be CMD (110) in bits P3 through
P1 (W1 through W3). The first character shall be "d"
(1100100) in bits C1-7 through C1-1) (W4 through W10), which shall
identify the DTM "data" function.
For DTM BASIC, EXTENDED, and NULL, when the "ARQ" control
bit KD4 (W11) is set to "0," no correct data receipt
acknowledgment is required; and when set to "1," it
is required. For DTM ARQ, "ARQ" control bit KD4 is
set to "0" to indicate acknowledgment or correct data
block receipt (ACK); and when set to "1," it indicates
a failure to receive the data and is therefore a request-for-repeat
(NAK). For DTM ARQ responding to a DTM NULL interrogation, KD4
"0" indicates non-participation in the DTM protocol
or traffic type, and KD4 "1" indicates affirmative participation
in both the DTM protocol and traffic type.
For DTM BASIC, EXTENDED, and NULL, when the "data type"
control bit KD3 (W12) is set to "0," the message data
contained within the DTM data block shall be binary bits with
no required format or pattern; and when KD3 is set to "1"
the message data is 7-bit ASCII characters. For DTM ARQ, "flow"
control bit KD3 is set to indicate that the DTM transfer flow
should continue, or resume; and when KD3 is set to "1"
it indicates that the sending station should pause (until another
and identical DTM ARQ is returned, except that KD3 shall be "0").
For DTM BASIC, EXTENDED, and NULL, when the "message"
control bit KD2 (W13) is set to the same value as the KD2 in any
sequentially adjacent DTM data block, the message data contained
within those adjacent blocks (after individual error control)
shall be recombined with the message data within the present DTM
data block segment-by-segment to reconstitute the original whole
message, and when KD2 is set opposite to any sequentially adjacent
DTM data blocks, those data blocks contain separate message data
and shall not be combined. For DTM ARQ, "message" control
bit KD2 shall be set to match the referenced DTM data block KD2
value to provide message confirmation.
For DTM BASIC, EXTENDED, and NULL, the "sequence" control
bit KD1 (W14) shall be set opposite to the KD1 value in the sequentially
adjacent DTM BASIC, EXTENDED, or NULLs to be sent (the KD1 values
therefore alternate, regardless of their message dependencies).
When KD1 is set to the same value as any sequentially adjacent
DTM sent, it indicates that it is a duplicate (which shall be
exactly the same). For DTM ARQ, "sequence" control
bit KD1 shall be set to match the referenced DTM data block or
NULL KD1 value to provide sequence confirmation.
When used for the DTM protocols, the ten DTM data code (DC) bits
DC10 through DC1 (W15 through W24) shall indicate the DTM mode
(BASIC, EXTENDED, ARQ, or NULL). They shall also indicate the
size of the message data and the length of the data block. The
DTM NULL DC value shall be "0" (0000000000), and it
shall designate the single CMD DTM NULL word. The DTM
EXTENDED DC values shall range from "1" (0000000001)
to "351" (0101011111), and they designate the CMD
DTM EXTENDED word and the data block multiple of DATA and
REP words that define the variable data block sizes. The
EXTENDED sizes shall range from 1 to 351 words, with a range of
21 to 7371 binary bits, in increments of 21; or three to 1053
ASCII characters, in increments of three. The DTM BASIC DC values
shall range from "353" (0101100001) to "1023"
(1111111111), and they shall designate the CMD DTM BASIC
word and the exact size of the message data in compact and variable
size data blocks, with up to 651 binary bits or 93 ASCII characters.
The DTM ARQ DC value shall be "352" (0101100000), and
it shall designate the single CMD DTM ARQ word. The DC
values "384" (0110000000) and all higher multiples of
"32m" (m x 100000) shall be reserved until standardized.
See table A-XXXII for DC values and DTM block sizes and other
characteristics.
The DBM ALE (orderwire) message protocol function enables ALE
stations to communicate either full ASCII, or unformatted binary
bit messages to and from any selected ALE station(s) for direct
output to and input from associated data terminal or other DTE
devices through their standard DCE ports. This DBM data transfer
function is a high-speed mode (relative to DTM and AMD) with improved
robustness, especially against long fades and noise bursts. When
used over MF/HF by the ALE system, DBM orderwire messages may
be unilateral or bilateral, and broadcast or acknowledged. As
the DBM data blocks can be very large, this special orderwire
message function enables exploitation of deep interleaving and
FEC techniques to penetrate HF-channel long fades and large noise
bursts.
The DBM data blocks shall be fully buffered at each station and
should appear transparent to the using DTEs or data terminals.
As a design objective and under the direction of the operator
or controller, the stations should have the capability of using
the DBM data traffic mode (ASCII or binary bits) to control switching
of the DBM data traffic to the appropriate DCE port or associated
DTE equipment, such as to printers and terminals (if ASCII mode)
or computers and cryptographic devices (if binary bits mode).
As an operator or controller-selected option, the received DBM
message may also be presented on the operator display, similar
to the method for AMD in table A.5.7.2.
There are four CMD DBM modes: BASIC, EXTENDED, NULL, and
ARQ. The DBM BASIC block is a fixed size and contains a variable
quantity of data, from zero to full as required, which is exactly
measured to ensure integrity of the data during transfer. The
DBM EXTENDED blocks are variable in size in integral multiples
of the BASIC block, and are filled with integral multiples of
message data. The DBM NULL and ARQ modes are used for both link
management, and error and flow control. The characteristics of
the CMD DBM orderwire message functions are listed in table
A-XXXIV, and they are summarized below:
| CMD DBM Mode | BASIC | EXTENDED | ARQ NULL |
| Maximum Size, Bits | 588 | 262836 | 0 |
| CRC | 16 Bits | 16 Bits | 0 |
| Data Capacity, ASCII | 0-81 | 81-37377, by 84 | 0 |
| Data Capacity, Bits | 0-572 | 572-261644, by 588 | 0 |
| ALE Word Redundancy | 49 Fixed | 49-21805, by 49 | 0 |
| Data Transmission | 3.136 Sec | 3.136 sec - 23.26 min, | 0 |
| by 3.136 sec increments | |||
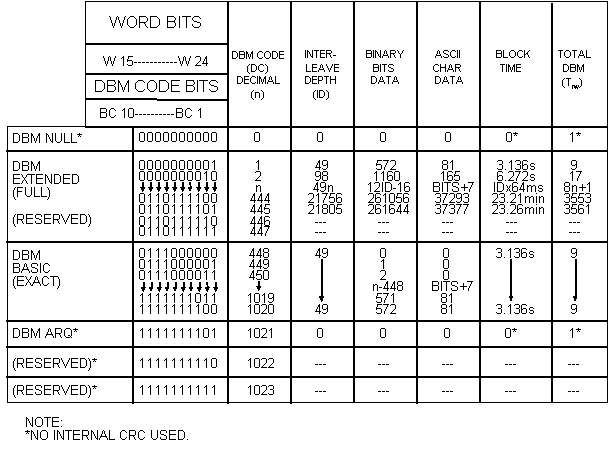
When an ASCII, or binary bit, digital data message function is
required, the following CMD DBM orderwire structures and
protocols shall be used as specified herein, unless another standardized
protocol is substituted. The DBM structure shall be inserted
within the message section of the standard frame. A CMD
DBM word shall be constructed in the standard format. The data
to be transferred shall be Golay FEC encoded, interleaved (for
error spreading during decoding), and transmitted immediately
following the CMD DBM word.
When the DBM structure transmission time exceeds the maximum for the message section
(Tm max), the DBM protocol shall take precedence
and shall extend the Tm limit to accommodate the DBM.
The DBM mode preserves the required consistency of redundant
word phase during the transmission. The message expansion due
to the DBM is always a multiple of 8 Trw, as the interleaver
depth is always a multiple of 49. The transmission time of the
DBM data block (Tdbm) itself is equal to (interleaver
depth x 64ms), not including the Trw for the preceding
CMD DBM word. Figure A-49 shows an example of an exchange
using the DBM orderwire to transfer and acknowledge messages.
Figure A-50 shows an example of a DBM data interleaver, and figure
A-51 shows the transmitted DBM bit-stream sequence.
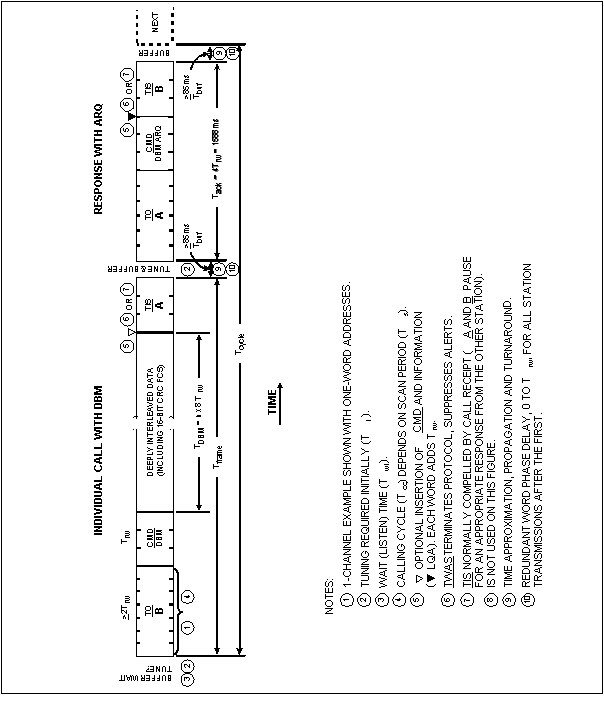
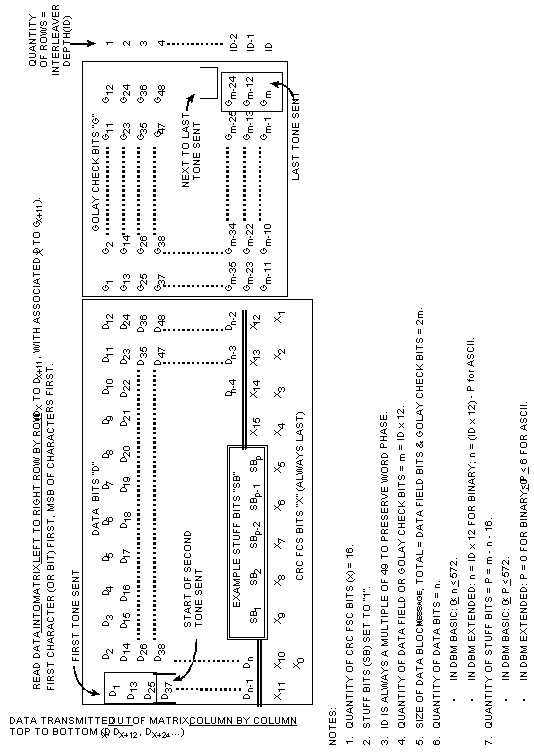
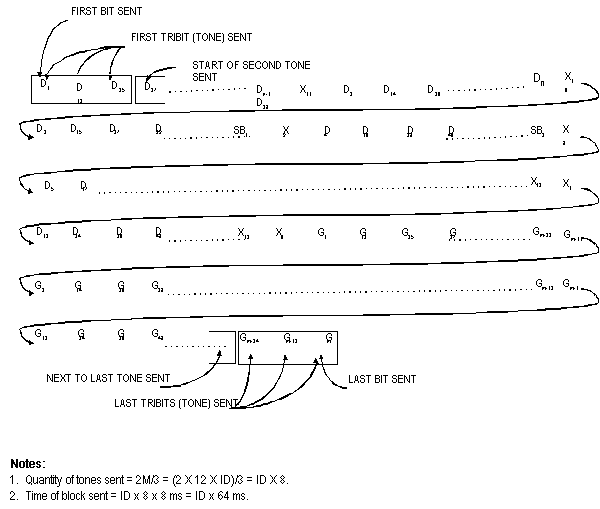
The DBM protocol shall be as described herein. The CMD DBM BASIC
and EXTENDED formats (herein referred to as DBM data blocks) shall
be used to transfer messages in information among ALE stations.
The CMD DBM ARQ format shall be used to acknowledge other CMD
DBM formats and for error and flow control, except for non-ARQ
and one-way broadcasts. The CMD DBM NULL format shall be used
to: (a) interrupt ("break") the DBM and message flow;
(b) to interrogate stations to confirm DBM capability before initiation
of the DBM message transfer protocols; and (c) to terminate the
DBM protocols while remaining linked. When used in handshakes
and subsequent exchanges, the protocol frame terminations for
all involved stations shall be TIS until all the DBM messages
are successfully transferred, and all are acknowledged if ARQ
error control is required. The only exceptions shall be when
the protocol is a one-way broadcast or the station is forced to
abandon the exchange by the operator or controller, in which cases
the termination should be TWAS.
Once a CMD DBM word of any type has been received by a
called (addressed) or linked station, the station shall remain
on channel for the entire specified DBM data block time (if any),
unless forced to abandon the protocol by the operator or controller.
The start of the DBM data block itself shall be exactly indicated
by the end of the CMD DBM BASIC or EXTENDED word itself.
The station shall attempt to read the entire DBM data block information,
plus the expected frame continuation, which shall contain a conclusion
(possibly preceded by additional functions in the message section,
as indicated by additional CMD words).
With or without ARQ, identification of each DBM data block and its associated orderwire message (if segmented into sequential DBM data blocks) shall be achieved by use of the sequence and message control bits, KB1 and KB2, (see table A-XXXV) which shall alternate with each DBM transmission and message, respectively. The type of data contained within the data block (ASCII or binary bits) shall be indicated by KB3 as a data identification bit. Activation of the ARQ error-control protocol shall use the ARQ control bit KB4. If no ARQ is required, such as in one-way broadcasts, multiple DBM data blocks may be sent in the same frame, but they shall be in proper sequence if they are transferring a segmented message.
| DBM Bits | Word Bits | |||
| CMD
preamble | MSB LSB | P3 = 1
P2 = 1 P1 = 0 | MSB | W3
W1 W2 |
| First
character "b" | MSB LSB | C1 (bit-7) = 1
C1 (bit-6) = 1 C1 (bit-5) = 0 C1 (bit-4) = 0 C1 (bit-3) = 0 C1 (bit-2) = 1 C1 (bit-1) = 0 | W4
W5 W6 W7 W8 W9 W10 | |
| Control
bits | MSB LSB | KB4
KB3 KB2 KB1 | W11
W12 W13 W14 | |
| DTM
data code bits | MSB LSB | BC10
BC9 BC8 BC7 BC6 BC5 BC4 BC3 BC2 BC1 | LSB | W15
W16 W17 W18 W19 W20 W21 W22 W23 W24 |
NOTES:
| ||||
When ARQ error or flow control is required, the CMD DBM
ARQ shall identify the acknowledged DBM data block by the use
of the sequence and message control bits KB1 and KB2, which shall
be set to the same values as the immediately preceding and referenced
DBM data block transmission. Control bit KB3 shall be used as
the DBM flow control to pause or continue (or resume) the flow
of the DBM data blocks. The ACK and NAK functions shall use the
ARQ control bit KB4. If no ARQ has been required by the sending
station, but the receiving station needs to control the flow of
the DBM data blocks, it shall use the DBM ARQ to request a pause
in, and resumption of, the flow.
When data transfer ARQ error and flow control is required, the
DBM data blocks shall be sent individually and in sequence. Each
DBM data block shall be individually acknowledged before the next
DBM data block is sent. Therefore, with ARQ there shall be only
one DBM data block transmission in each frame. If the transmitted
DBM data block causes a NAK in the returned DBM ARQ, as described
below, or if no ACK or DBM ARQ is detected in the returned frame,
or if no frame is detected at all, the sending station shall resend
an exact duplicate of the unacknowledged DBM data block. It shall
continue to resend duplicates (which should be at least seven),
one at a time and with appropriate pauses for responses, until
the involved DBM data block is specifically acknowledged by a
correct DBM ARQ. Only then shall the next DBM data block in the
sequence be sent. If the sending station is frequently or totally
unable to detect frame or DBM ARQ responses, it should abort the
DBM transfer protocol, terminate the link and relink and reinitiate
the DBM protocol on a better channel (under operator or controller
direction).
Before initiation of the DBM data transfer protocols, the sending
stations should confirm the existence of the DBM capability in
the intended receiving stations, if not already known. When a
DBM interrogation function is required, the following protocol
shall be used. Within any standard protocol frame (using TIS),
the sending station shall transmit a CMD DBM NULL, with
ARQ required, to the intended station(s). These receiving stations
shall respond with the appropriate standard frame and protocol,
with the following variations. They shall include a CMD
DBM ARQ if they are DBM capable, and they shall omit it if they
are not DBM capable. The sending station shall examine the ALE
and DBM ARQ responses for existence, correctness, and the status
of the DBM KB control bits, as described herein. The transmitted
CMD DBM NULL shall have its control bits set as follows:
KB1 and KB2 set opposite of any subsequent and sequential CMD
DBM BASIC or EXTENDED data blocks which will be transmitted next;
KB3 set to indicate the intended type of traffic; and KB4 set
to require ARQ. The returned CMD DBM ARQ shall have its
control bits set as follows: KB1 and KB2 set to match the interrogating
DBM NULL; KB3 set to indicate if the station is ready for DBM
data exchanges, or if a pause is requested; and KB4 set to ACK
if the station is ready to accept DBM data transmissions with
the specified traffic type, and NAK if it cannot or will not participate,
or if it failed to read the DBM NULL.
The sending (interrogating) station shall handle any stations
which return a NAK, or do not return a DBM ARQ, or do not respond,
in any combination of the following, and for any combination of
these stations. The specific actions and stations shall be selected
by the operator or controller. The sending station shall: (a)
terminate the link with these stations, using an appropriate and
specific call and the TWAS terminator; (b) direct the stations
to remain and stay linked during the transmissions, using the
CMD STAY protocol in each frame immediately before each
CMD DBM word and data block sent; or (c) redirect them
to do anything else which is controllable using the CMD
functions described within this standard.
Each received DBM data block shall be examined using the CRC data
integrity test which is embedded within the DBM structure and
protocol. If the data block passes the CRC test, the data shall
be passed through to the appropriate DCE port (or normal output
as directed by the operator or controller). If the data block
is part of a larger message which was segmented before DBM transfer,
it shall be recombined before output. If any DBM data blocks
are received and do not pass the CRC data integrity test, any
detectable but uncorrectable errors; or areas likely to contain
errors, should be tagged for further analysis, error control,
or inspection by the operator or controller.
If ARQ is required, the received but unacceptable data block shall
be temporarily stored, and a DBM ARQ NAK shall be returned to
the sender, who shall retransmit an exact duplicate DBM data block.
Upon receipt of the duplicate, the receiving station shall again
test the CRC. If the CRC is successful, the data block shall
be passed through as described before, the previously unacceptable
data block should be deleted, and a DBM ARQ ACK shall be returned.
If the CRC fails again, both the duplicate and the previously
stored data blocks shall be used to correct, as possible, errors
and to create an "improved" data block. See figure
A-48 for an example of data block reconstruction. The "improved"
data block shall then be CRC tested. If the CRC is successful,
the "improved" data block is passed through, the previously
unacceptable data blocks should be deleted, and a DBM ARQ ACK
shall be returned. If the CRC test fails, the "improved"
data block shall also be stored and a DBM ARQ NAK shall be returned.
This process shall be repeated until: (a) a received duplicate,
or an "improved" data block passes the CRC test (and
the data block is passed through, and a DBM ARQ ACK is returned);
(b) the maximum number of duplicates (such as seven or more) have
been sent without success (with actions by the sender as described
above); or (c) the operators or controllers terminate or redirect
the DBM protocol.
During reception of frames and DBM data blocks, it is expected
that fades, interferences, and collisions will occur. The receiving
station shall have the capability to maintain synchronization
with the frame and the DBM data block transmission, once initiated.
It shall also have the capability to read and process any colliding
and significantly stronger (that is, readable) ALE signals without
confusing them with the DBM signal (basic ALE reception in parallel,
and always listening). The DBM structures, especially the DBM
EXTENDED, can tolerate significant fades, noise bursts, and collisions.
Therefore, useful information which may be derived from readable
collisions of ALE signals should not be arbitrarily rejected or
wasted.
The DBM constructions shall be as described herein. Within the
DBM data block structure, a CMD DBM word shall be placed
ahead of the encoded and interleaved data block itself. The DBM
word shall alert the receiving station that a DBM data block is
arriving, how long it is, what type of traffic it contains, what
its interleaver depth is, what its message and block sequence
is, and if ARQ is required. It shall also indicate the exact
start of the data block itself (the end of the CMD DBM
word itself) and shall initiate the reception, tracking, deinterleaving,
decoding, and checking of the data contained within the block.
The message data itself shall be either one of two types, binary
bits or ASCII. The ASCII characters (typically used for text)
shall be the standard 7-bit length, and the start, stop, and parity
bits shall be removed at the sending (and restored at the receiving)
station. The binary bits (typically used for other character
formats, computer files, and cryptographic devices) may have any
(or no) pattern or format, and they shall be transferred transparently,
that is, exactly as they were input to the sending station, with
the same length and without modification. The value of the interleaver
depth shall be the smallest (multiple of 49) which will accommodate
the quantity of ASCII or binary bits message data to be transferred
in the DBM data block. If the message data to be transferred
does not exactly fit the uncoded data field of the DBM block size
selected (except for the last 16 bits, which are reserved for
the CRC), the available empty positions shall be "stuffed"
with ASCII "DEL" characters or all "1" bits.
The combined message and "stuff" data in the uncoded
DBM data field shall then be checked by the CRC for error control
in the DBM protocol. The resulting 16-bit CRC word shall always
occupy the last 16 bits in the data field. All the bits in the
field shall then be Golay FEC encoded, on a 12-bit basis, to produce
rows of 24-bit code words, arranged from top to bottom in the
interleaver matrix (or equivalent), as shown in figure A-50.
The bits in the matrix are then read out by columns (of length
equal to the interleaver depth) for transmission. Immediately
after the CMD DBM word, the encoded and interleaved data
blocks bits shall follow in bit format, three bits per symbol
(tone).
The DBM BASIC data block has a fixed size (interleaver depth 49)
and shall be used to transfer any quantity of message data between
zero and the maximum limits for the DBM BASIC structure, which
is up to 572 bits or 81 ASCII characters. It is capable of counting
the exact quantity of message data which it contains, on a bit-by-bit
basis. It should be used as a single DBM for any message data
within this range. It shall also be used to transfer any message
data in this size range which is an "overflow" from
the larger size (and increments) DBM EXTENDED data blocks (which
shall immediately precede the DBM BASIC in the DBM sequence of
sending).
The DBM EXTENDED data blocks are variable in size, in increments
of 49 times the interleaver depth. They should be used as a single,
large DBM to maximize the advantages of DBM deep interleaving,
FEC techniques, and higher speed (than DTM or AMD) transfer of
data. The interleaver depth of the EXTENDED data block should
be selected to provide the largest data field size which can be
totally filled by the message data to be transferred. Any "overflow"
shall be in a message data segment sent within an immediately
following DBM EXTENDED or BASIC data block. Under operator or
controller direction, multiple DBM EXTENDED data blocks, with
smaller than the maximum appropriate interleaver depth sizes,
should be selected if they will optimize DBM data transfer throughput
and reliability. However, these multiple data blocks will require
that the message data be divided into multiple segments at the
sending station and sent only in the exact order of the segments
in the message. The receiving stations must recombine the segments
into a complete received message. When binary bits are being
transferred, the EXTENDED data field shall be filled exactly to
the last bit. When ASCII characters are being transferred, the
EXTENDED data field may have 0 to 6 "stuff" bits inserted.
Individual ASCII characters shall not be split between DBM data
blocks and the receiving station shall read the decoded data field
on a 7-bit basis, and it shall discard any remaining "stuff"
bits (modulo-7 remainder).
If stations are exchanging DBM data blocks and DBM ARQs, they
may combine both functions in the same frames. They shall discriminate
based on the direction of transmission and the sending and destination
addressing. If ARQ is required in a given direction, only one
DBM data block shall be allowed within any frame in that direction,
and only one DBM ARQ shall be allowed in each frame in the return
direction. If no ARQ is required in a given direction, multiple
DBM data blocks may be included in frames in that direction, and
multiple DBM ARQs may be included in the return direction.
As always throughout the DBM protocol, any sequence of DBM data
blocks to be transferred shall have their KB1 sequence control
bits alternating with the preceding and following DBM data blocks
(except duplicates for ARQ, which shall be exactly the same as
their originally transmitted DBM data block). Also, all multiple
DBM data blocks transferring multiple segments of a large data
message shall all have their KB2 message control bits set to the
same value, and opposite of the preceding and following messages.
If a sequence of multiple but unrelated DBM data blocks are sent
(such as several independent and short messages within several
DBM BASIC data blocks), they may be sent in any sequence. However,
when sent, the associated KB1 and KB2 sequence and message control
bits shall alternate with those in the adjacent DBM data blocks.
The CMD DBM words shall be constructed as shown in table
A-XXXV. The preamble shall be CMD (110) in bits P3 through
P1 (W1 through W3). The first character shall be "b"
(1100010) in bits C1-7 through C1-1 (W4 through W10), which shall
identify the DBM "block" function.
For DBM BASIC, EXTENDED, and NULL, when the ARQ control bit KB4
(W11) is set to "0," no correct data receipt acknowledgment
is required; and when set to "1," it is required. For
DBM ARQ, ARQ control bit KB4 is set to "0" to indicate
acknowledgment or correct data block receipt (ACK); and when set
to "1," it indicates a failure to receive the data and
is therefore a request-for-repeat (NAK). For DBM ARQ responding
to a DBM NULL interrogation, KB4 "0" indicates non-participation
in the DBM protocol or traffic type, and KB4 "1" indicates
affirmative participation in both the DBM protocol and traffic
type.
For DBM BASIC, EXTENDED, and NULL, when the data type control
bit KB3 (W12) is set to "0," the message data contained
within the DBM data block shall be binary bits with no required
format or pattern; and when KB3 is set to "1" the message
data is 7-bit ASCII characters. For DBM ARQ, flow control bit
KB3 is set to "0" to indicate that the DBM transfer
flow should continue or resume; and when KB3 is set to "1"
it indicates that the sending station should pause (until another
and identical DBM ARQ is returned, except that KB3 shall be "0").
For DBM BASIC, EXTENDED, and NULL, when the "message"
control bit KB2 (W13) is set to the same value as the KB2 in any
sequentially adjacent DBM data block, the message data contained
within those adjacent blocks (after individual error control)
shall be recombined with the message data within the present DBM
data block to reconstitute (segment-by-segment) the original whole
message; and when KB2 is set opposite to any sequentially adjacent
DBM data blocks, those data blocks contain separate message data
and shall not be combined. For DBM ARQ, "message" control
bit KB2 shall be set to match the referenced DBM data block KB2
value to provide message confirmation.
For DBM BASIC, EXTENDED, and NULL, the sequence control bit KB1
(W14) shall be set opposite to the KB1 value in the sequentially
adjacent DBM BASIC, EXTENDED, or NULLs be sent (the KB1 values
therefore alternate, regardless of their message dependencies).
When KB1 is set the same as any sequentially adjacent DBM sent,
it indicates a duplicate. For DBM ARQ, sequence control bit KB1
shall be set to match the referenced DBM data block or NULL KB1
value to provide sequence confirmation.
When used for the DBM protocols, the ten DBM data code (BC) bits
BC10 through BC1 (W15 through W24) shall indicate the DBM mode
(BASIC, EXTENDED, ARQ, or NULL). They shall also indicate the
size of the message data and the length of the data block. The
DBM NULL BC value shall be "0" (0000000000), and it
shall designate the single CMD DBM NULL word. The DBM
EXTENDED BC values shall range from "1" (0000000001)
to "445" (0110111101), and they shall designate the
CMD DBM EXTENDED word and the data block multiple (of 49
INTERLEAVER DEPTH) which defines the variable data block sizes,
in increments of 588 binary bits or 84 ASCII characters. The DBM
BASIC BC values shall range from "448" (0111000000)
to "1020" (1111111100), and they shall designate the
CMD DBM BASIC word and the exact size of the message data
in a fixed size (INTERLEAVER DEPTH = 49) data block, with up to
572 binary bits or 81 ASCII characters. The DBM ARQ BC value
shall be "1021" (1111111101), and it shall designate
the single CMD DBM ARQ word.
NOTES:
1. The values "446" (0110111110) and "447" (0110111111) are reserved.
2. The values "1022" (1111111110) and "1023" (1111111111) are reserved until standardized (see table A-XXXIV).
AQC-ALE is designed to use shorter linking transmissions than those of baseline second generation ALE (2G ALE) described previously in this appendix. AQC-ALE uses an extended version of the 2G ALE signaling structure to assure backward compatibility to already fielded radios. Special features of AQC-ALE include the following: